Enriched, real-time phishing management
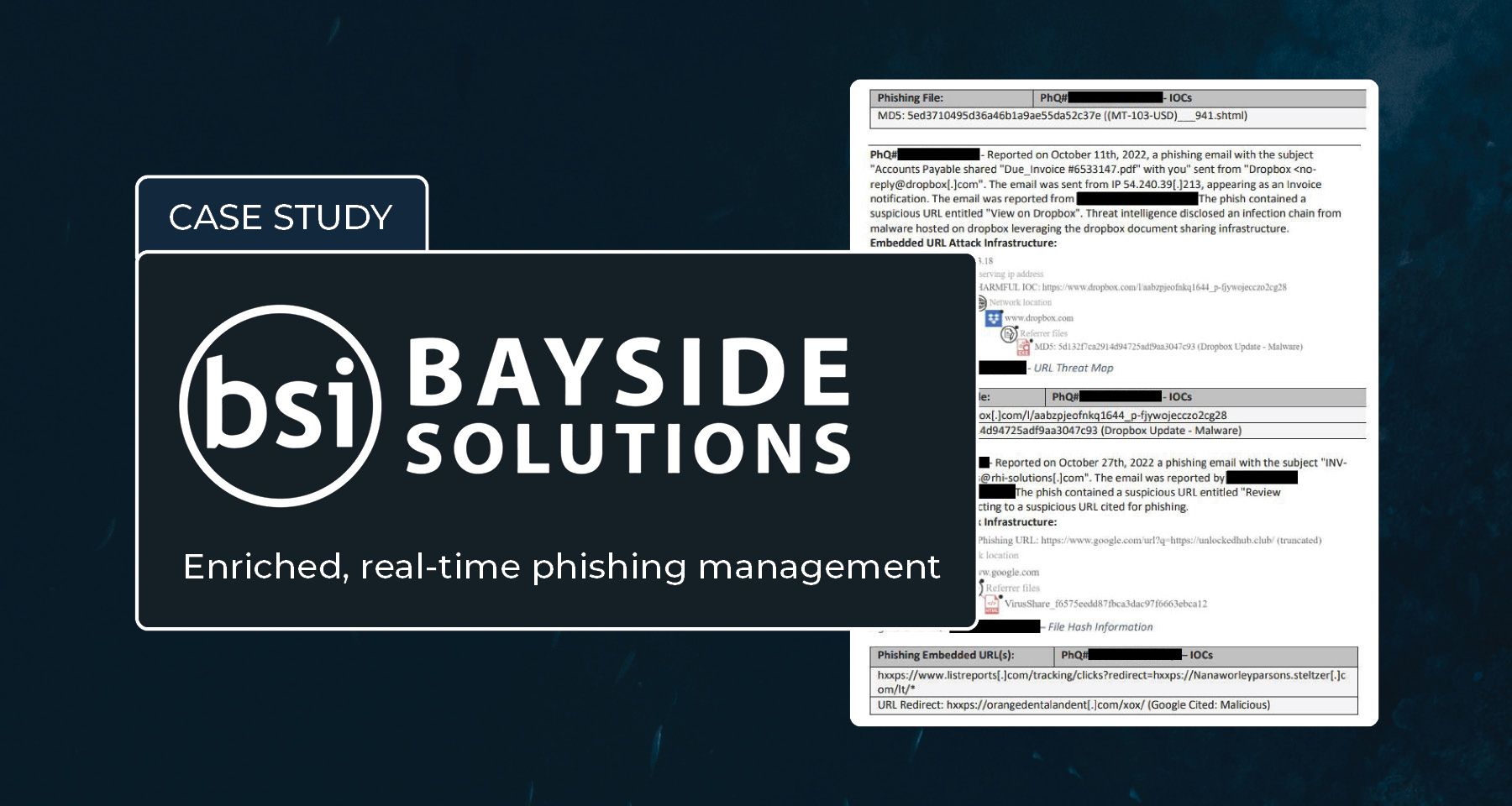
Case Study: BSI's "PhishQueue" service leverages Pulsedive's Enterprise TIP to help clients detect, investigate, and defend against phishing attacks.
US cybersecurity firm founded in 2001, serving clients in energy, finance, defense, high-technology, and other sectors.
BSI’s PhishQueue is a phishing management service that allows users to report suspicious messages, get expert analysis, and detect threats.
BSI leverages Pulsedive Enterprise Threat Intelligence Platform (TIP) for intelligence processing and management.
A Fight Against Phishing
Phishing attacks remain one of the most common forms of cybercrime that can have severe consequences for organizations. To help clients defend their networks, Bayside Solutions, Inc. (BSI) sought to enable users to proactively identify and report suspicious emails while freeing up precious in-house resources.
Clients were eager to implement such a service, but BSI first needed a way to collect and organize the intelligence generated by automated and human research. This led to the design of “PhishQueue,” the phishing management service offering expert examination and threat detection.
Bolstered by Intelligence
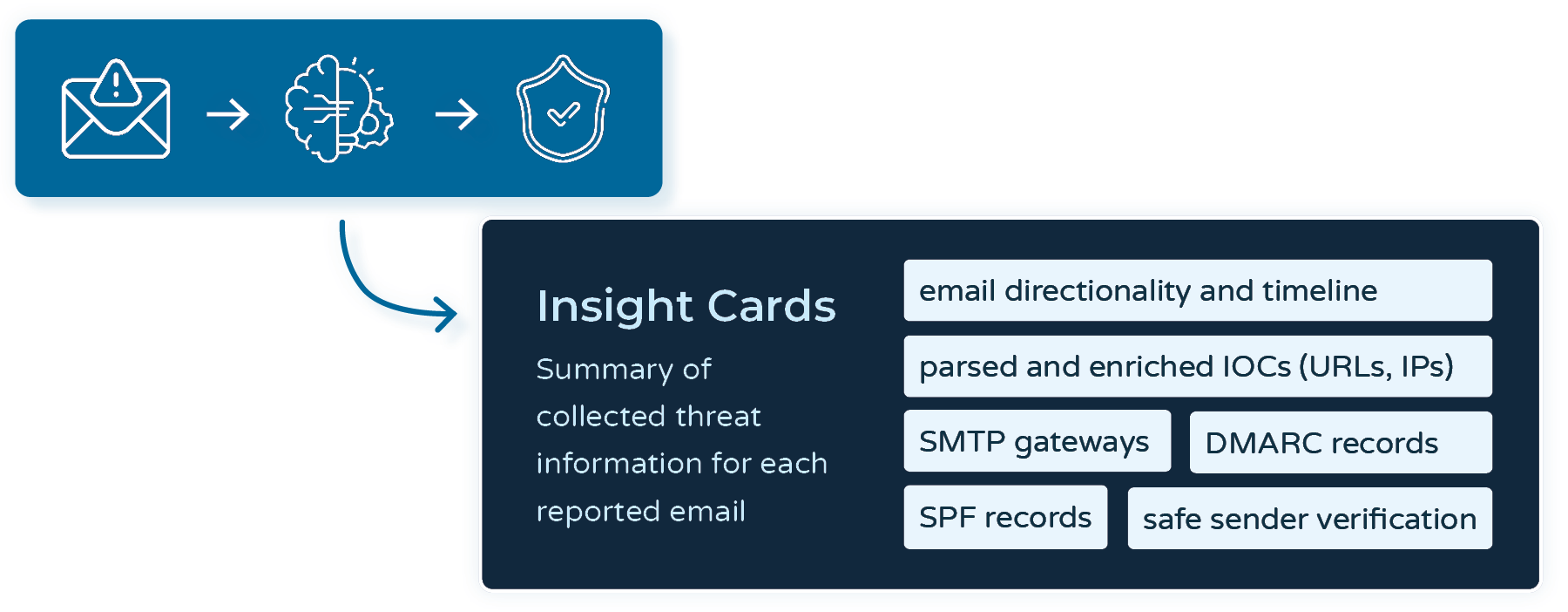
Developed around proprietary systems, PhishQueue would:
- Ingest emails reported by users
- Analyze content: inspecting headers and attachments, verifying sender authenticity, detecting spoofing or malicious activity
- Develop insight cards with tagging for long-term tracking and analysis
- Return timely responses and reporting to end users
- Return actionable IOCs and Purge requests to customer IT / security teams
The ideal threat intelligence partner had two core features: critical, on-demand enrichment data and a centralized database to efficiently manage PhishQueue’s unique IOCs. As a bonus for situations requiring deeper investigations, BSI sought a cyber threat intelligence (CTI) tool with robust user interfaces for human analysis and pivoting.
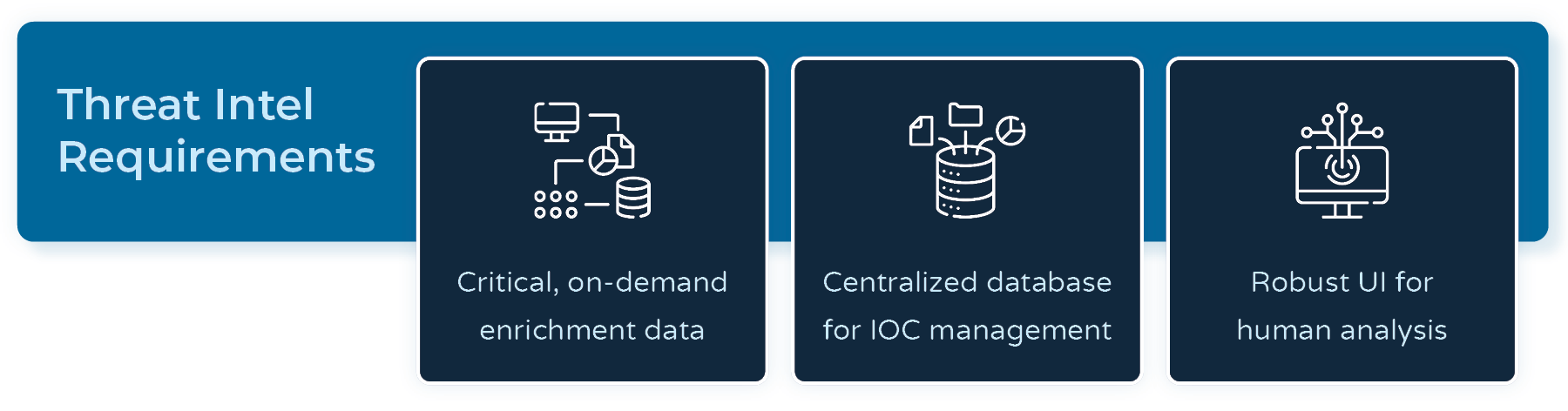
Unfortunately, many available threat intelligence platforms had irrelevant features, overly complex licensing and pricing, limitations on data ingestion, enrichment, and export, or needed more of the in-depth correlation, pivoting, and collaboration functionality that BSI required.
Three capabilities set Pulsedive apart as the winning choice:
- Flexibility in processing, editing, and exporting data
- Transparent risk factors behind each risk score, which supported analysis and accurate verdicts
- Preconfigured, high fidelity open source feeds with the ability to add, parse, and ingest new sources code-free
“Pulsedive Enterprise offers seamless integration and powerful threat enrichment... The collection of correlated research and threat feeds makes sharing and collaboration easy to implement.”
Anthony Arrington, Director of Cyber Threat Intelligence
Hitting the Ground Running
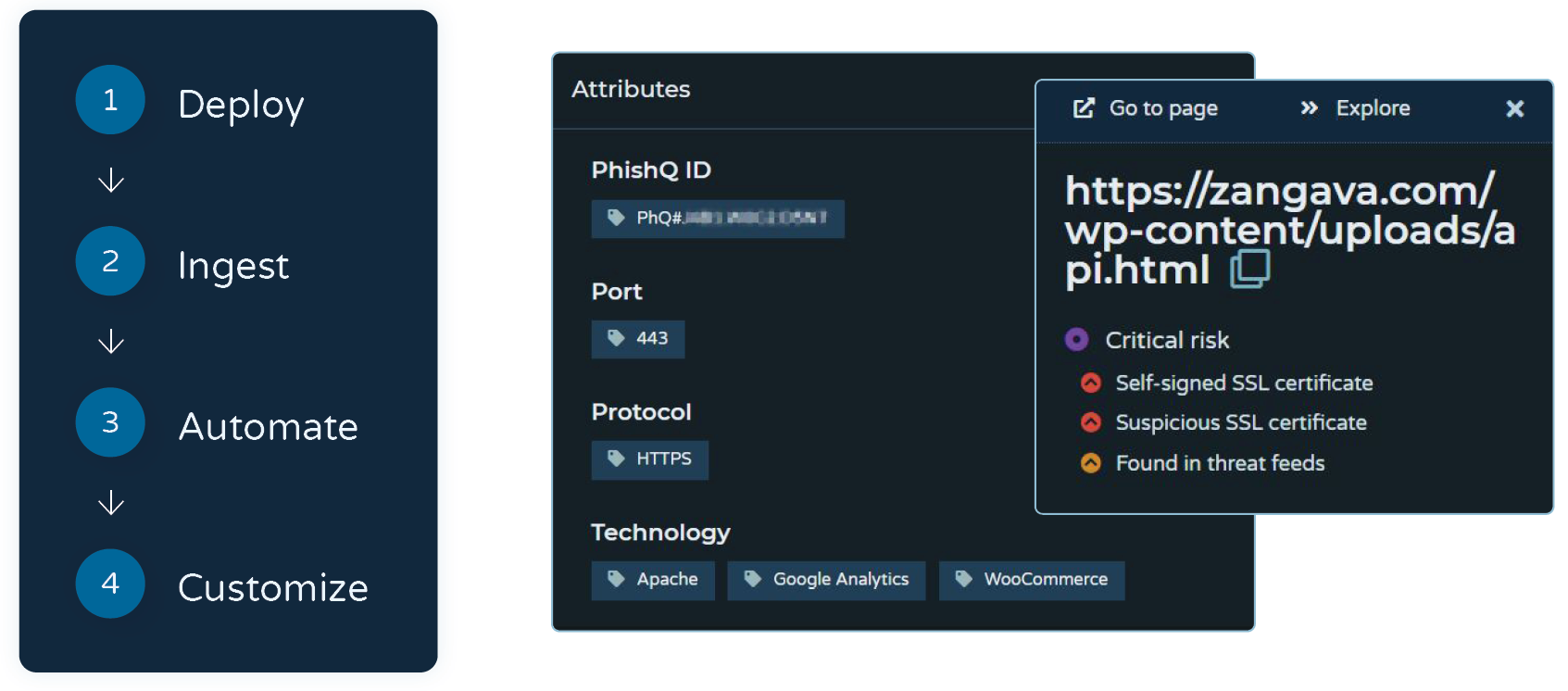
Collaborating over three months, BSI & Pulsedive transitioned from a Pulsedive POC with the PhishQueue MVP to full commercial implementation and solution launch. Together, the team:
- Deployed a fully functional Pulsedive POC
- Ingested reputable phishing feeds for real-time cross-referencing against known threats
- Built custom automation connectors and workflows to process and enrich IOCs
- Implemented BSI’s custom “PhishQueue ID” tagging system to track threat actors and campaigns
Results
After deployment in client environments, PhishQueue successfully expanded in both processing volume and CTI maturity. Their dedicated Pulsedive Enterprise Threat Intelligence Platform processes millions of IOCs weekly, with the streamlined workflows making it possible for the team to address over 95% of all reported emails within 2 hours during core hours. Facilitated by Pulsedive’s enrichment and custom curation capabilities, PhishQueue now also provides monthly reports with deep-dive threat activity and actor tracking.

Intelligence.
Equipped with live and historical data from Pulsedive, PhishQueue creates detailed phishing attack timelines with initiation, malicious activity, and remediation timestamps. The team has detected numerous phishing kits and tracks specific threat actors, including the resurgence of Emotet’s “Swiss army knife style” malware in early 2022. Beyond individual reports, PhishQueue’s ability to analyze threat actor tactics, techniques, and procedures (TTPs), monitor evolving themes, and assess motivations informs proactive defense at a larger scale.
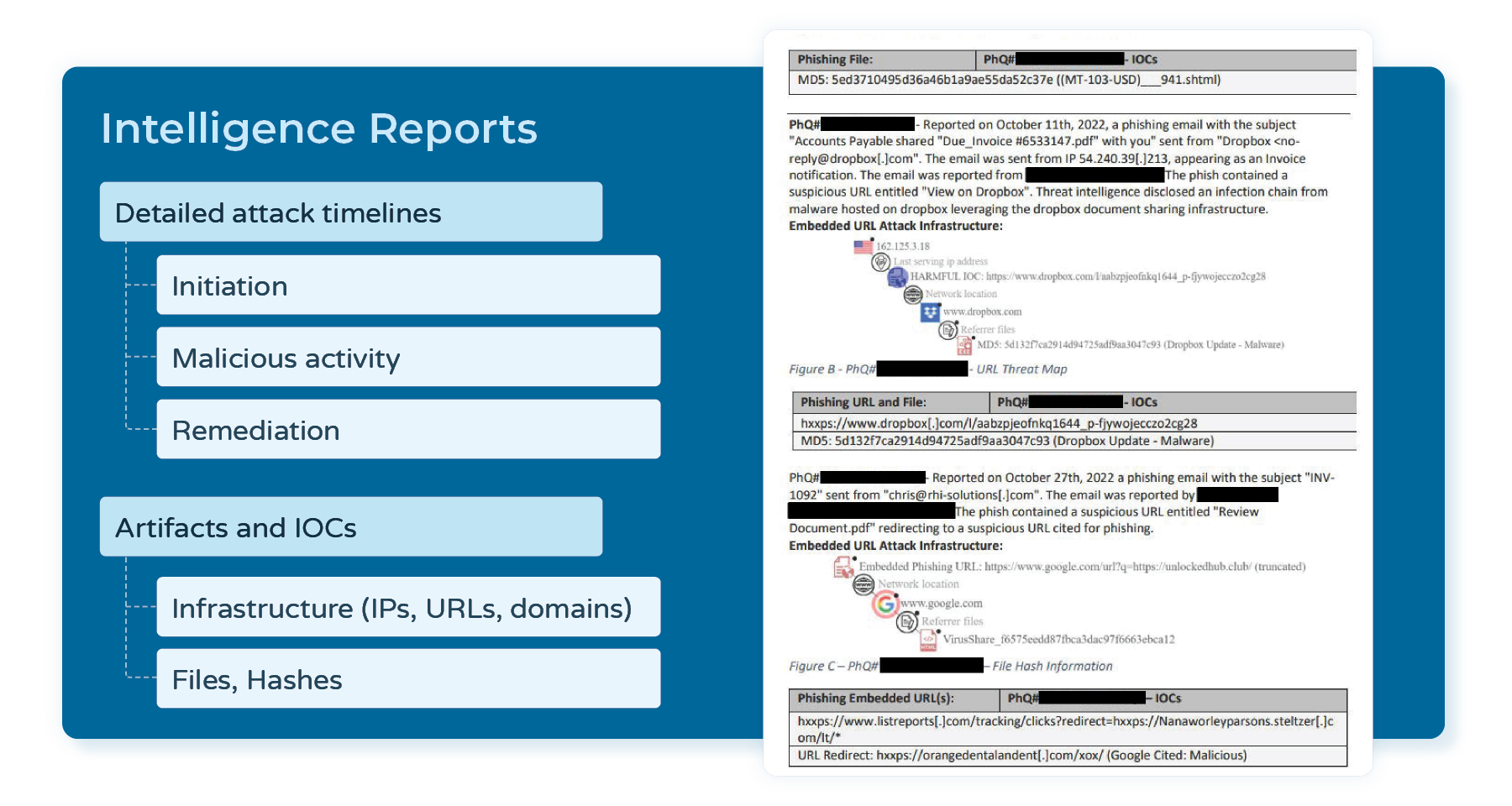
Closing the Gap.
In comparative analyses with leading phishing protection tools, PhishQueue is closing the gap on erroneous determinations. The team regularly detects and neutralizes false negatives, handles false positives, and addresses other mis-categorizations. In some cases, the inaccurate verdicts of widely used tools rose higher than 20%.
For example, PhishQueue was able to identify malicious emails with CAPTCHA, which other services failed to detect. This was a significant discovery as adding CAPTCHA increases the chance of a successful phishing attempt two-fold: creating a more realistic infection chain to trick users of legitimacy while slowing down defense operations.
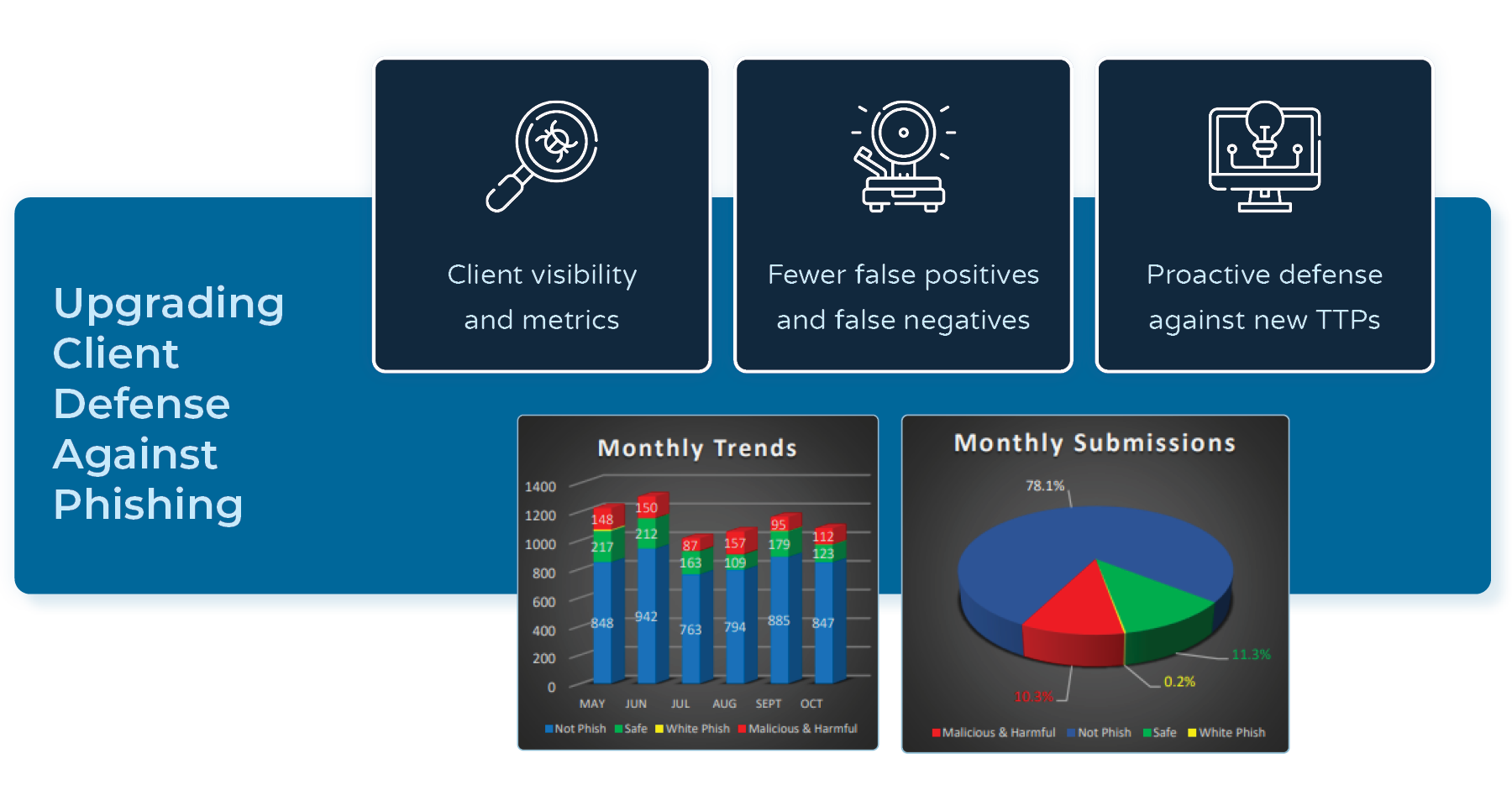
Conclusion.
Overall, PhishQueue has increased user engagement and awareness, while allowing client teams to redirect their security operations resources to more strategic measures.
Next, PhishQueue will leverage more of Pulsedive’s features by developing its own API framework. Doing so will allow the team to expand their insight cards, publish a unique threat feed, and create more customized tracking as BSI’s clients’ leading phishing email analysis service.
“Pulsedive Enterprise’s threat insights and workflows take the TIP beyond simple enrichment.
“Our unique deployment of the Pulsedive Enterprise platform allows tactical threat intelligence to be accessed from one centralized application. The rich API provides access to granular meta-data and privately hosted analyst notes. Pulsedive’s insight into sophisticated threats places the threat data under the fingertips of analysts to deploy quick and systematic countermeasures.”
Anthony Arrington, Director of Cyber Threat Intelligence
Have Q's about Enterprise or interested in a POC?
Related Links





