PikaBot Rising
Dive into the distribution methods and capabilities of Pikabot, a loader that has been growing in prevalence since early 2023.
Pikabot is an emerging loader that has been active since early 2023. The malware provides access to environments with the ability to remotely execute commands for reconnaissance or the ingress of additional tools. Over the past year, security researchers have observed Pikabot distributed through malspam and malvertising. Its usage became more prevalent following the takedown of Qakbot by law enforcement agencies in 2023.
This blog provides an overview of the distribution mechanisms and features of Pikabot with to highlight its capabilities which include:
- Anti-analysis checks
- Loading junk libraries
- Executing commands
- Gathering system information
Distribution Mechanisms
Pikabot has been distributed primarily through spam emails. Following the takedown of Qakbot in August 2023, there was an increase in campaigns using Pikabot. Similar to campaigns spreading other malware, these emails are often part of a hijacked thread containing either an attachment or a link to download the file.
Spam Campaigns
Trend Micro Research identified a spam campaign used to deliver Pikabot. The campaign leveraged thread hijacking, where threat actors inject themselves into existing email threads and send emails as if the malicious entity was always part of the thread. Typically, Pikabot intrusions start through a JavaScript file that is used to download and execute the second stage payload. In other observed intrusions, instead of a Javascript file, the ZIP archive contained either an IMG or PDF file. In the case of an IMG, it consists of a LNK file masquerading as a Word document and the Pikabot DLL. The LNK file is used to execute the Pikabot DLL. For PDFs, the PDF serves as a lure that is used to download the DLL sample. The LOLBIN, rundll32.exe, is used to execute the DLL file.
Malvertising
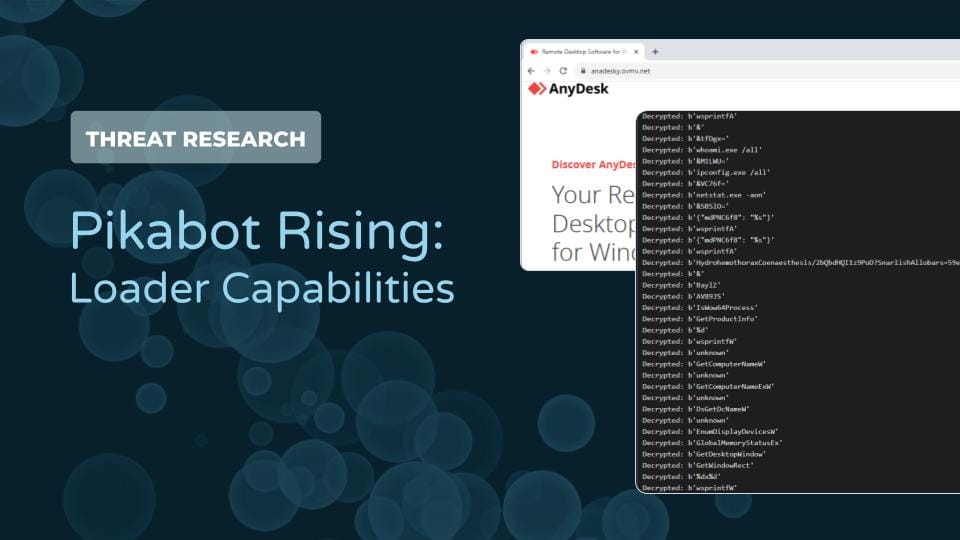
Threat researchers have also identified cases where Pikabot was distributed through malicious advertising. In one example, Pikabot impersonated the remote access tool AnyDesk in a malvertising campaign (Malwarebytes). The campaign used paid advertisements for the phishing sites to appear at the top of a user’s Google search results and rely on a user clicking the sponsored link instead of the actual AnyDesk URL. After users clicked the malvertising link, they were redirected to a page mimicking the AnyDesk webpage.
The page hosts a malicious .msi file used to run Pikabot. The MSI uses process hollowing to execute the malicious code in a SearchProtocolHost.exe process, by creating the process in a suspended state, unmapping the process memory, writing the malicious code to memory, and then resuming the thread.
Features of Pikabot
Dynamic API Resolving
Pikabot samples resolve APIs at runtime. This means that some of the necessary APIs needed for the sample to execute are loaded during its execution and not when the program is compiled. This is an attempt by the malware author to make it more difficult to determine functionality through static analysis of imported APIs. Three functions are resolved through API hashing and once GetProcAddress and LoadLibraryA are resolved, they can be used to resolve other APIs that are stored as decrypted strings.
OALabs developed Python code that can be used to decrypt the strings. The figure below shows some of the decrypted strings from the sample 39d6f7865949ae7bb846f56bff4f62a96d7277d2872fec68c09e1227e6db9206
Anti-Analysis Techniques
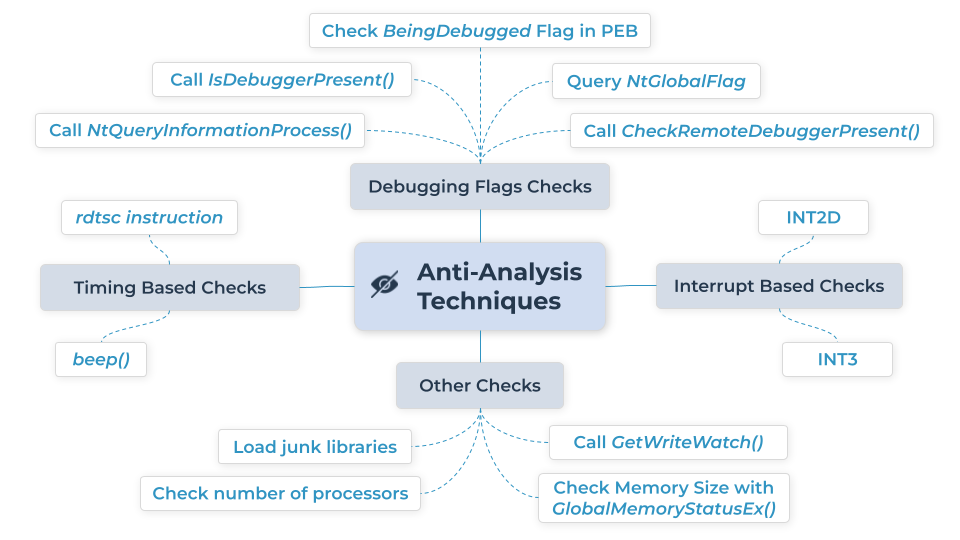
The sample leverages several anti-analysis techniques to make analysis of the malware more difficult, which include:
- Using INT2D and INT3 to raise exception handlers
- INT3 is a software breakpoint that is used to trigger an interrupt. When a debugger is not in use, the exception handler is called after an INT3 exception is raised. When a debugger is present, control of the program is not handed to the exception handler.
- For INT2D, Windows uses the EIP register as the exception address and then increments the EIP register value. This instruction may cause issues for debuggers since increasing the EIP may cause instructions to be skipped.
- Checking the BeingDebuggedFlag in the PEB
- Calling the APIs
CheckRemoteDebuggerPresent()andIsDebuggerPresent() - Loading junk libraries
- Delaying execution using the
beep()function- This is used in a similar fashion to the sleep function and is intended to delay execution. The beep function generates a noise that is played on speakers. The execution of the program waits until the sound stops to resume execution.
- Checking the value of the
NtGlobalFlagin the process environment block to see if a debugger is attached - Calling
NtQueryInformationProcess()with the flag0x7(ProcessDebugPort) - Using the
GetWriteWatch()to get addresses of the allocated pages written - Checking if the number of processors is less than or equal to 2
- Using the rdtsc instruction to detect single steps taken in a debugger
- Checking memory size with
GlobalMemoryStatusEx()to see if it is less than 2GB
Language Checks
Apart from the checks outlined above which cause the program to terminate, Pikabot samples also check the language of the system to avoid infecting CIS countries. ZScaler identified that the samples check for the following languages:
- Georgian
- Kazakh
- Uzbek
- Tajik
- Russian
- Ukrainian
- Belarusian
- Slovenian
The API function GetUserDefaultLandID returns the language for the current user. This information can also be determined from Control Panel -> Clock, Language, and Region -> Change date, time, or number formats -> Formats (Microsoft).
If any of these languages are identified, then the program terminates. This type of check to avoid infecting endpoints in CIS countries is not unique to Pikabot and has also been observed in several ransomware variants.
Capabilities
Once the anti-analysis checks are complete, the malware initiates connections with a Command and Control server. The malware also executes several commands to gather additional information about the compromised host. The commands include collecting network information using the ipconfig.exe binary and collecting user information through the whoami.exe /all command.
Apart from using native binaries to collect system information, researchers at Zscaler identified the following capabilities that the malware can perform.
- cmd
- destroy
- shellcode
- dll
- Exe
- knock_timeout
- Information collection
- screenshot
- whoami
- ipconfig
- processes
Conclusion
Pikabot is a relatively recent loader that increased in popularity from August 2023 onwards. As of January 2024, there has been just 1 sample shared on Malware Bazaar uploaded on January 3rd, 2024. The malware adopts several anti-analysis techniques which make it difficult to detect and analyse. Pikabot binaries resolve APIs using API hashing and decrypted strings, meaning looking at imports during static analysis may not provide insight into the malware’s functionality. The malware also can execute commands on the infected host, using this to conduct system information discovery activities.
Recommendations
- Continued User Awareness Training
- Both of Pikabot’s dissemination mechanisms require user execution. Continued user awareness training may help mitigate the risk from spam and malvertising by teaching users how these threats work and what to look out for.
- Monitor and block the execution of cmd or curl from scripting interpreters
- To alert on potentially malicious VBScript or JavaScript files attempting to download additional payloads or launching recently downloaded executable content.
- Some security products contain rules to block this type of activity. An example is the Block JavaScript or VBScript from launching downloaded executable content attack surface reduction rule in Microsoft Defender for Endpoint.
Indicators of Compromise
The table below contains a list of Pikabot network IoCs identified and added to the Pulsedive platform. IoCs can be queried in Pulsedive using the Explore query threat="Pikabot" and is available for export in multiple formats (CSV, STIX 2.1, JSON).
The table below shows some fingerprints for Pikabot C2 infrastructure:

