Pulsedive FAQs
Answers to some of the most popular and frequently asked questions we get at Pulsedive.

Below are a few answers to some of the most popular and frequently asked questions about the Pulsedive Community platform:
- What does Pulsedive do?
- Who uses Pulsedive?
- What can I do for FREE?
- How can I get a free API key?
- What kinds of data can I find?
- What's on an IOC page?
- What’s the difference between scanning and submitting?
- Can you tell me more about these passive and active scans - and your infrastructure?
- How does Pulsedive risk scoring work?
- What kinds of data can Pulsedive users edit?
- How do you keep data recent and relevant?
- How are threats linked to indicators?
- What's on a Threat page?
- How can I use Explore?
- How do I use Analyze?
- Does Pulsedive integrate with [insert software here]?
- Which paid Pulsedive products are best for which use cases?
- What if I want a private version of Pulsedive’s platform just for myself/my team?
- Where can I learn more about Pulsedive?
What does Pulsedive do?
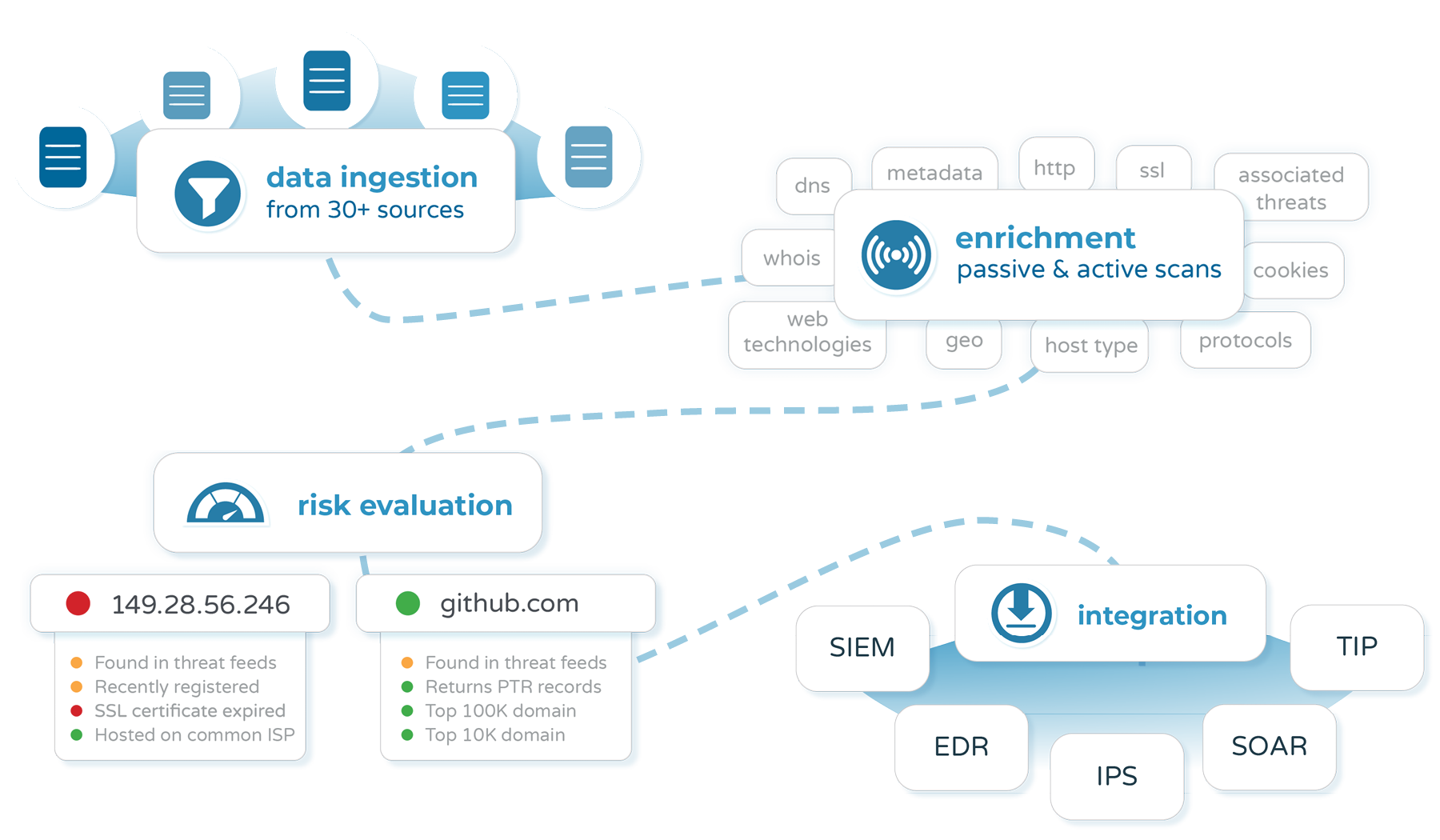
Pulsedive's community platform brings together known community threat intelligence into one place and vets that data to reduce noise and help security teams make determinations. We correlate observed IOCs not only by ASN or country but by more complex characteristics like HTTP headers and PTR records.
In other words, we ingest from user submissions and many quality feeds (you can find the current list at the bottom of our overview).
We then perform scans to provide a wealth of real-time contextual information on each indicator. This includes all the properties, linked indicators, risk factors, and risk scores you see on our indicator pages (for example, check out our Pulsedive domain indicator page). We also deduplicate indicators, merge threat aliases, update news streams, and more to provide vetted, unique, and timely threat intelligence.
Who uses Pulsedive?
Everyone (can).
Our global community includes a wide range of users, from students to CISOs across sectors - and teams blue, red, and purple. A majority of users come from security analyst and engineering backgrounds, most often in security operations and, obviously, threat intelligence teams. However, we also support many home hobbyists, academic and independent researchers, students, and special use cases as well.
What can I do for FREE?
With a free account, you can search and/or scan any indicator and get back contextual intelligence, investigate threats, check out our source feeds, query, and filter across our entire database, stream the latest news/events, and more.
Simply put, many of the actions an individual researcher, hunter, analyst, or enthusiast might want to try out in a threat intelligence platform are already free. We even include an API key with every registered account.
If you have additional needs for yourself or your team, we have upgrades like:
- Individual Pro subscriptions, which come with more data in the same intuitive interface
- Commercial API plans to flexibly integrate Pulsedive into your workflow
- Commercial Feed plans for bulk download of vetted threat intelligence
How can I get a free API key?
Every registered user has an API key. After registering a free account (https://pulsedive.com/register) and logging in, you can find your key on your account page or at the top of any of our API docs pages.
What kinds of data can I find?
Here are just a few of the types of data you can find related to indicators, threats, and feeds in Pulsedive. Users can also pivot from these data points within the platform and easily copy or export data for further analysis.
Indicator Data
- Risk scores and risk factors
- Registration timeline
- Pulsedive timestamps
- Source feeds and comments
- Associated threats
- Ports and protocols
- Web technologies
- WHOIS registration
- Location data
- DNS records
- Query strings
- HTTP headers
- SSL certificate metadata
- Cookies
- Meta tags
- Mail servers
- Redirects
- Related domains and URLs
- Screenshots (Pro*)
- Third-party integrations (Pro*)
Threats
- Risk scores
- Known aliases
- Related news and references
- Comments
- Tactics and techniques
- Shared attributes
- Source feeds
- Linked indicators
Feeds
- Summary
- Name and organization
- Linked Indicators
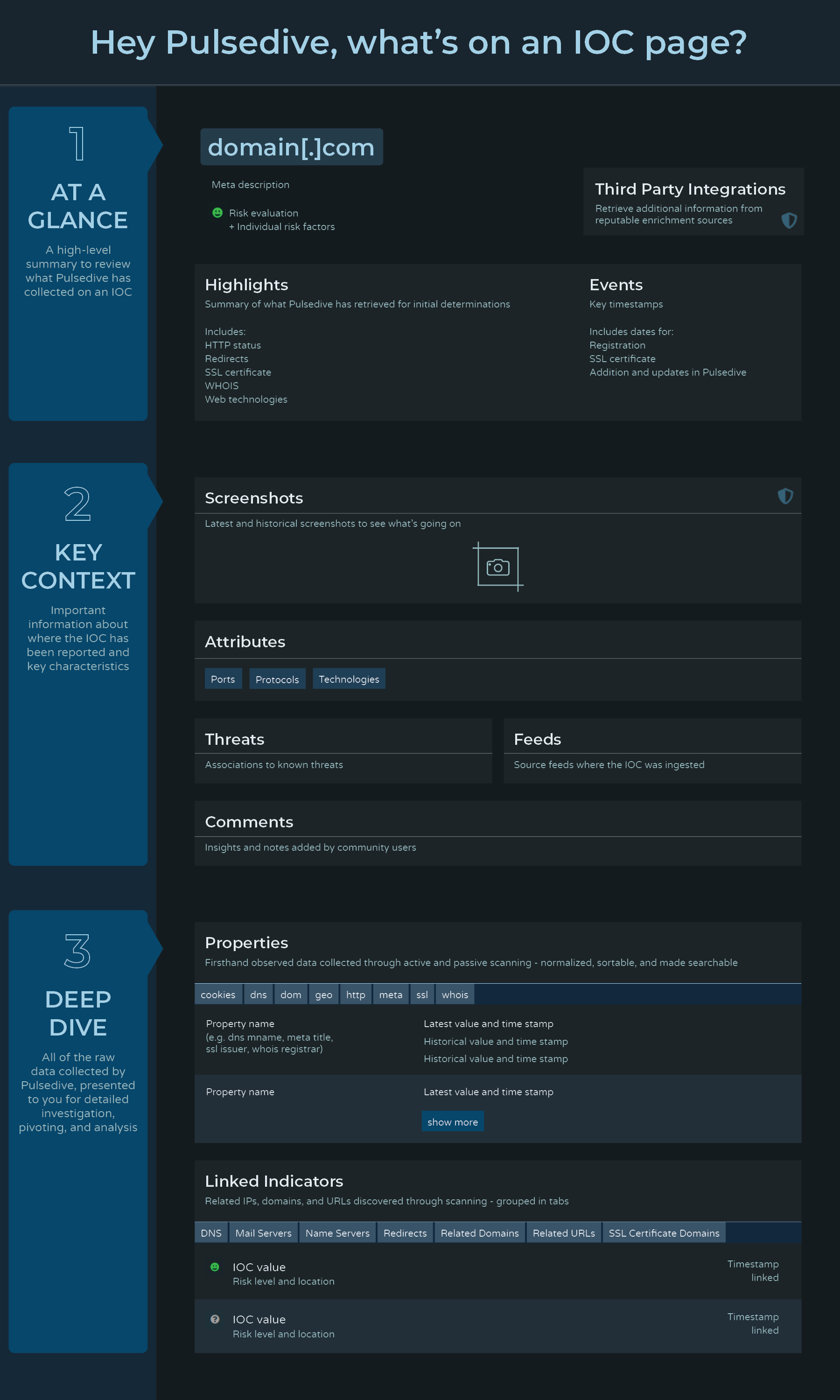
What's on an IOC page?
There's a lot of information we collect and share with you on domains, IPs, and URLs. To get you started, here's an overview of how to read our IOC pages and all the potential types of data you might find on one.
What’s the difference between scanning and submitting?
In Pulsedive, you can scan without submitting. If an indicator is not already in our database, it means you can opt to perform a passive or active scan, retrieve, and review the data, but no data is permanently stored.
This is valuable for users who do not want or cannot share indicators publicly with the community. However, we encourage our users to submit when possible, so everyone can benefit from new threat intelligence.
Can you tell me more about these passive and active scans - and your infrastructure?
Every indicator is scanned and enriched by Pulsedive. The result is a wealth of real-time, contextual information.
Passive Scans: Perform WHOIS requests and fetch DNS records.
Active Scans: Reach out with a web browser to collect valuable data like HTTP headers, SSL certificate information, and redirects. Also runs a port scan with ~15 common ports.
Pulsedive has several scanning “nodes” set up all around the world that are hardened, so there is no direct connection between Pulsedive and malicious IOCs.
The next generation of our infrastructure will include more data and utilize rotating proxies - stay tuned!
How does Pulsedive risk scoring work?
While we pull data from many sources, we scan and enrich every single indicator ourselves. Pulsedive uses all of the data collected to determine which risk factors are present and evaluate an indicator’s risk level.

Many risk factors go into the risk score for an indicator, including considerations like:
- “Is this a direct-to-IP URL?”
- “Is the SSL certificate self-signed?”
- “Was this domain registered recently?”
- “Is this a top 10k domain?”
- “Has this been seen on a threat feed?”
What kinds of data can Pulsedive users edit?
Basic account users can submit and scan indicators, as well as add comments to indicator and threat pages.
Our enrichment and evaluation process is designed to avoid false positives, but we do have a trusted group of Contributors, Researchers, and Admins with elevated permissions who can further vet and update data. Message us at support@pulsedive.com if you have questions or find an issue with our data.
How do you keep data recent and relevant?
Due to our many sources and unique user submissions, we are processing threat intelligence data that no one else has, every day.
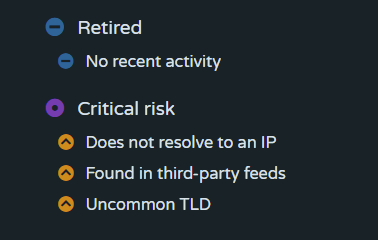
Indicators are automatically aged out after a period of inactivity unless they reappear in one of our sources, are reported by users, or are reactivated by a Contributor or Admin. These retired indicators show a “Retired” risk rating and can be excluded in “Explore” queries if specified. However, users can search for an indicator that is retired and still see all of the historical data.
How are threats linked to indicators?
Some OSINT feeds occasionally have threat information listed in one of the fields or columns, and other feeds are dedicated to a specific threat, like Zeus Bad Domains or Phishtank. Pulsedive is configured to link all IOCs in these feeds to the relevant threat.
Additionally, a limited set of vetted users with elevated permissions can link IOCs to threats upon submission, as well as edit IOCs to add or remove threats.
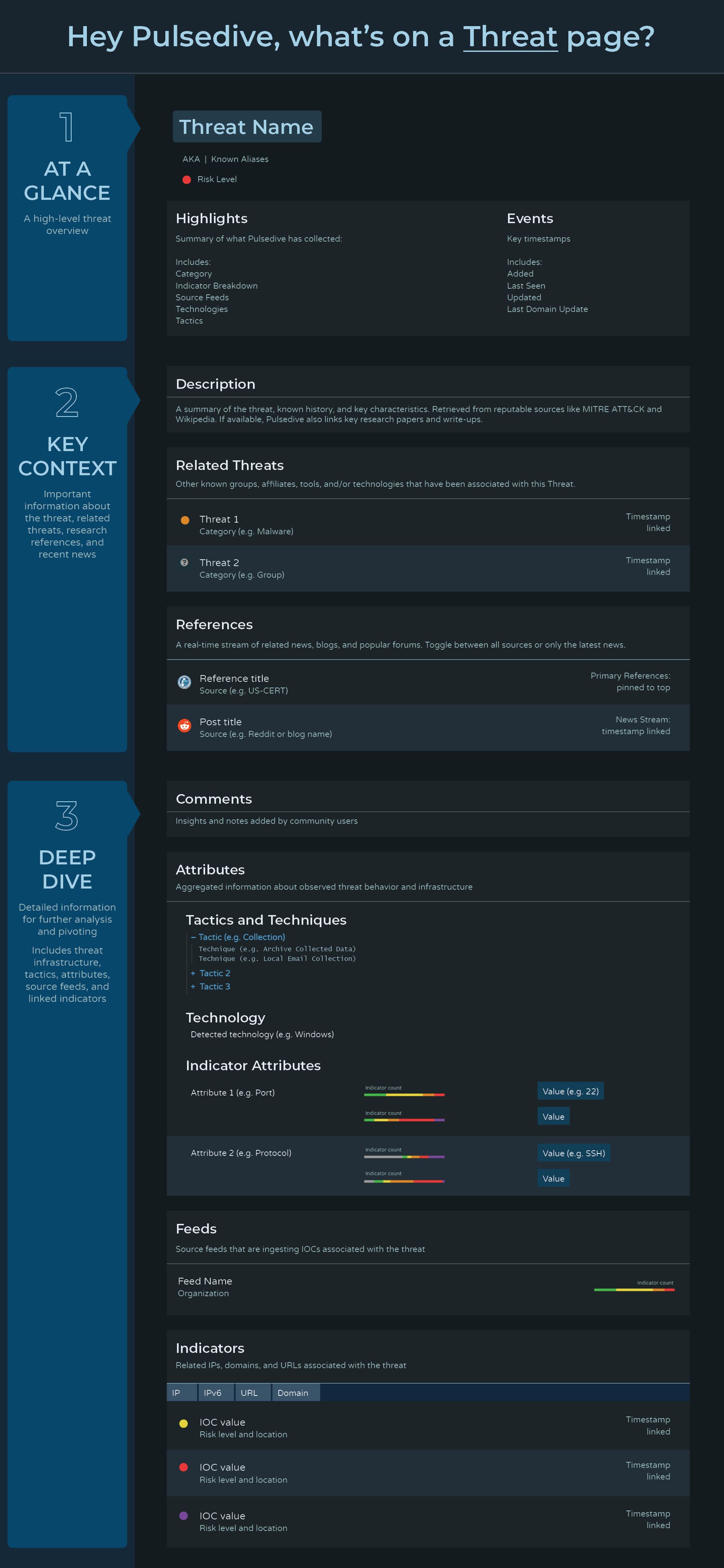
What's on a Threat page?
Threat pages cover overviews, news, IOCs, TTPs, and other relevant information regarding various threat types. Here's some of the information that can be found on our Threat pages.
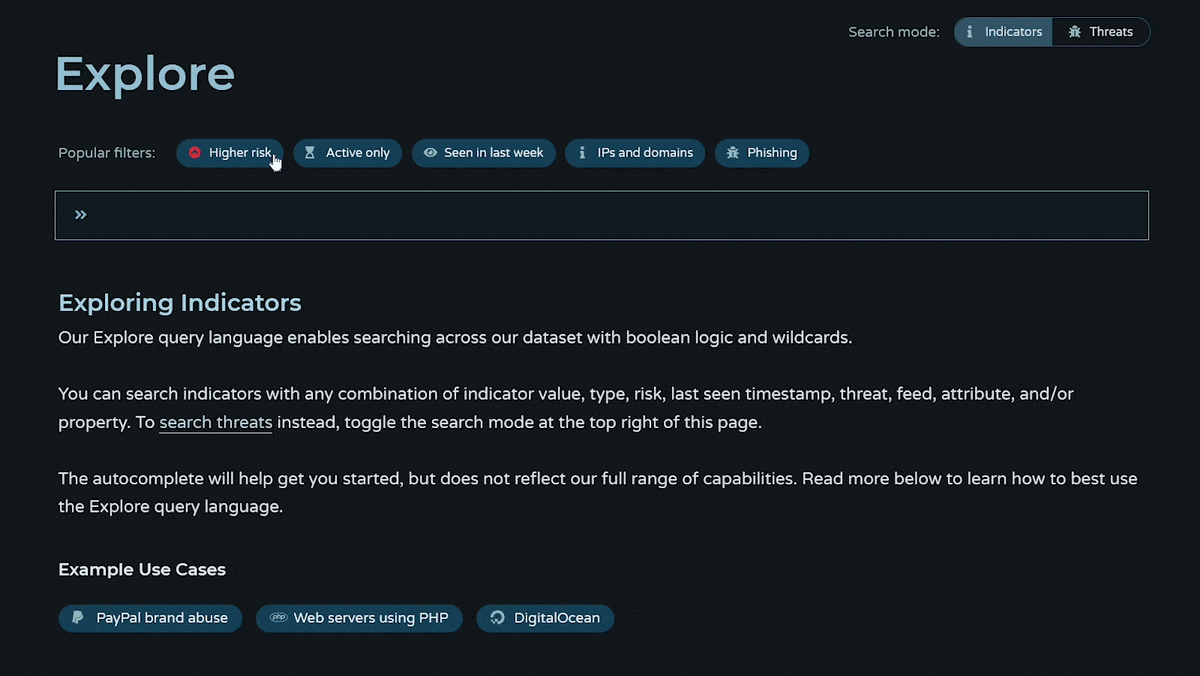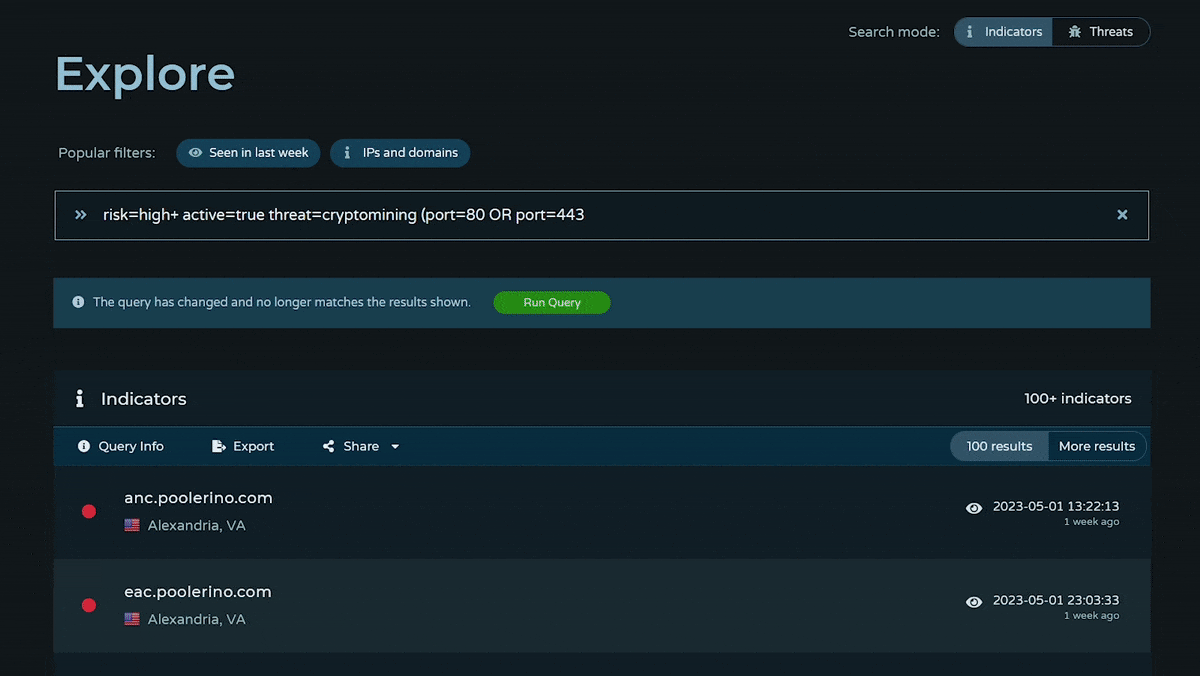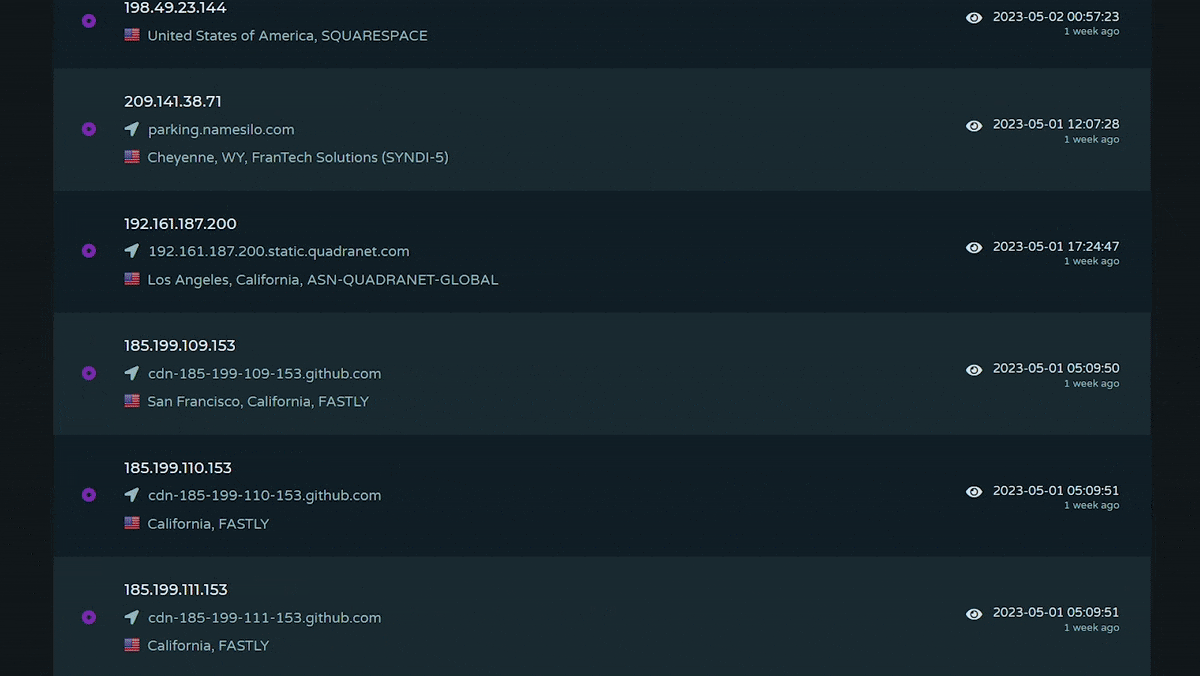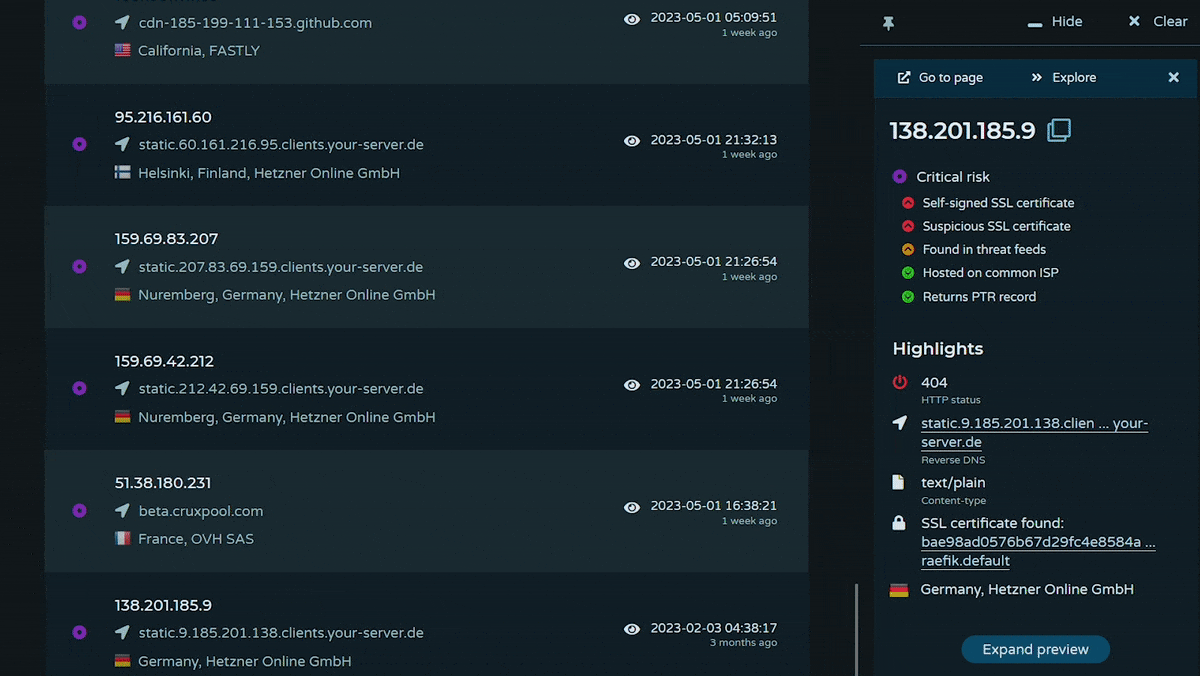
How can I use Explore?
Our Explore query language enables users to search across our entire Community dataset of indicators and threats with Boolean logic and wildcards. You can search indicators with any combination of indicator value, type, risk, last seen timestamp, threat, feed, attribute, and/or property. (Nearly anything we show on an IOC page, you can add to your query.) To search threats, toggle the search mode at the top right of the Explore page. You can search threats with any combination of threat name, alias, category, risk, last seen timestamp, feed, and threat attribute.
Autocomplete can help with suggestions to get started, but doesn't reflect our full range of capabilities. Our Explore page comes with a quick start guide that walks you through how to use the page and sample queries.
How do I use Analyze?
Analyze is used for the bulk processing, enrichment, and exporting of indicators. It's designed to support internal investigations, proactively find potential threats, parse and enrich indicators from external reports, and make it easy to extract and compare key information in bulk and on demand.
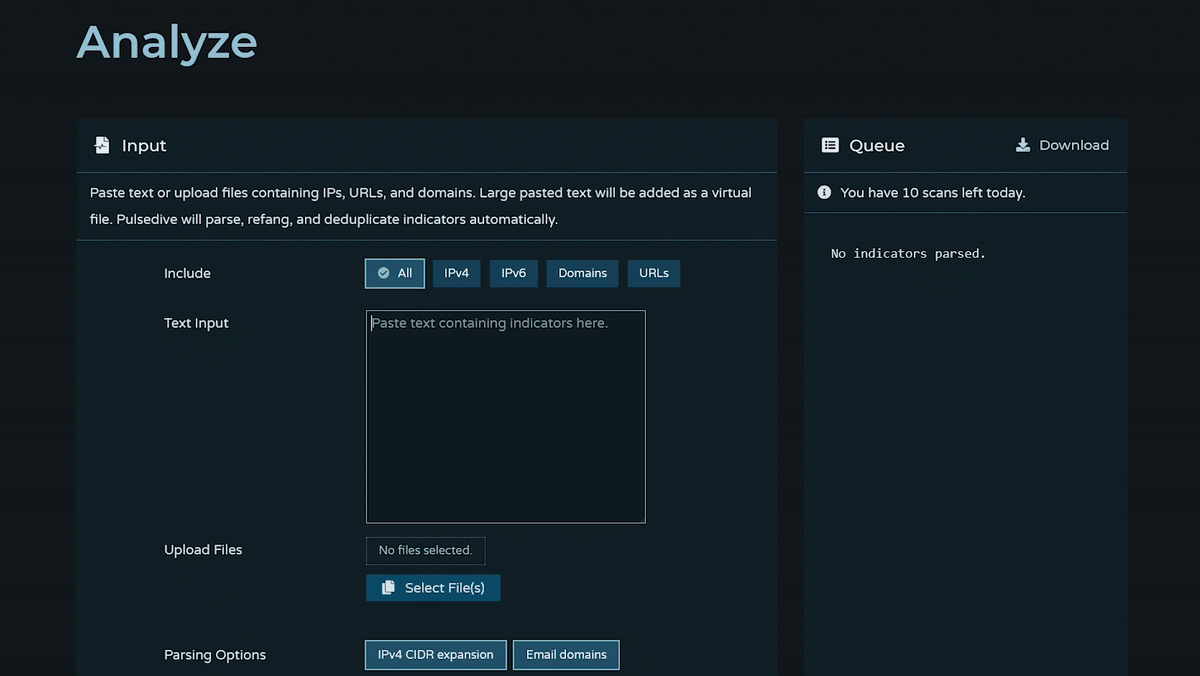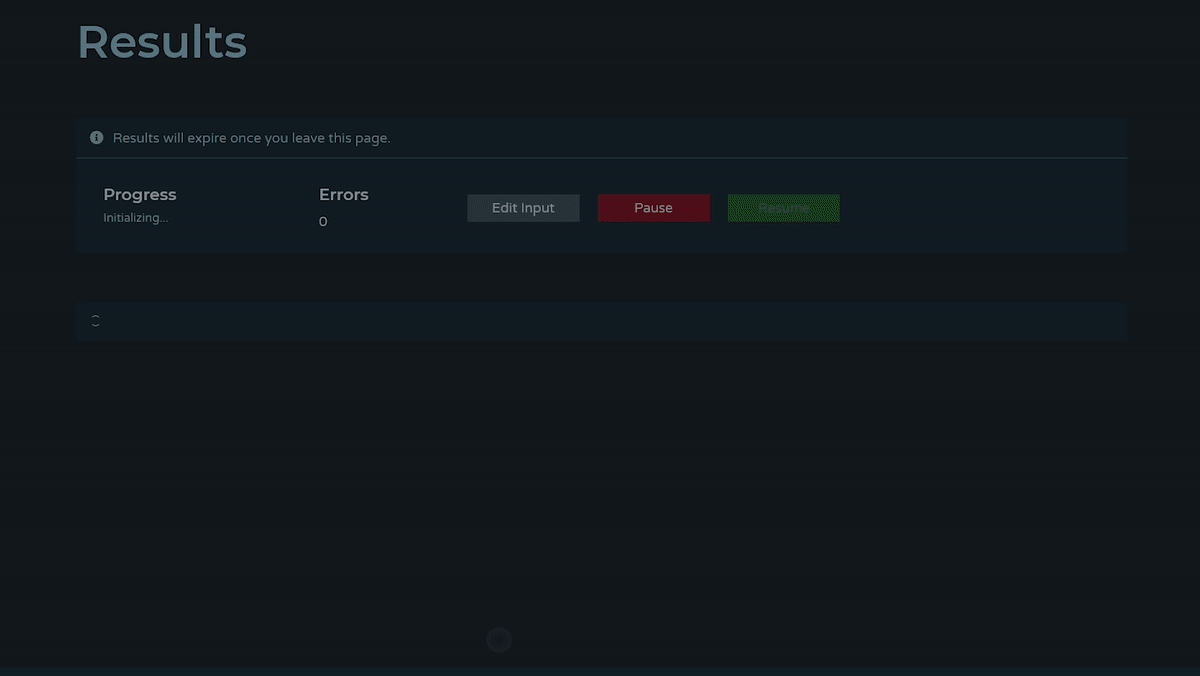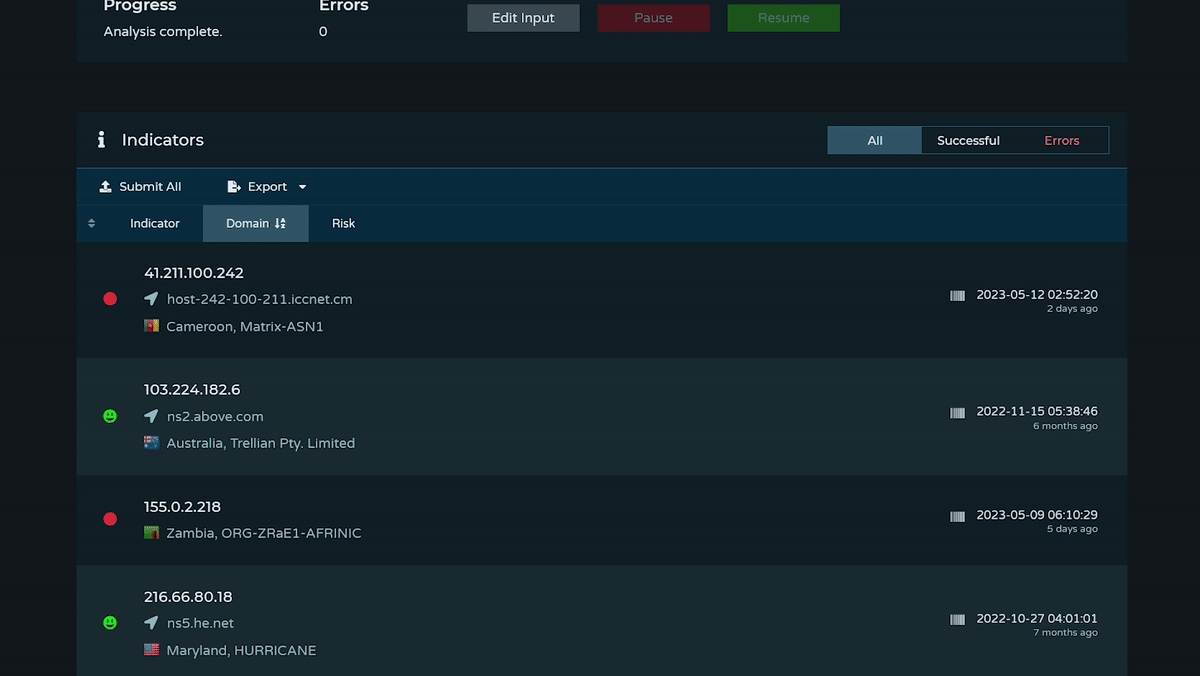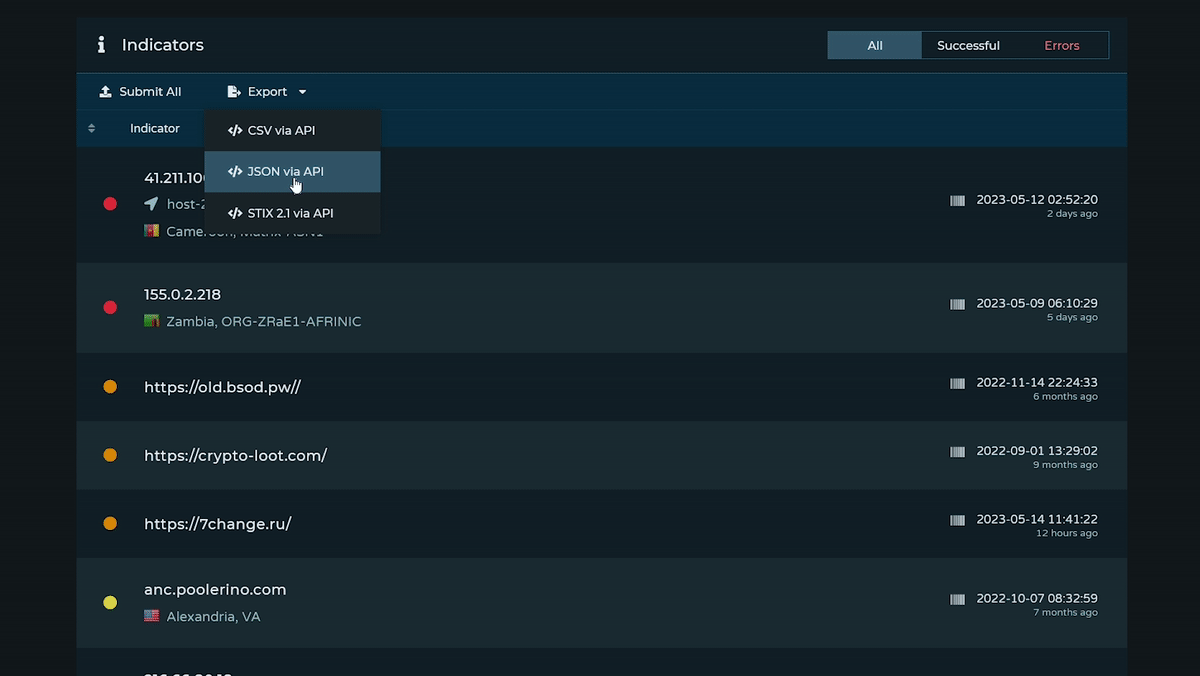
Learn more with a step by step walkthrough in this blog.
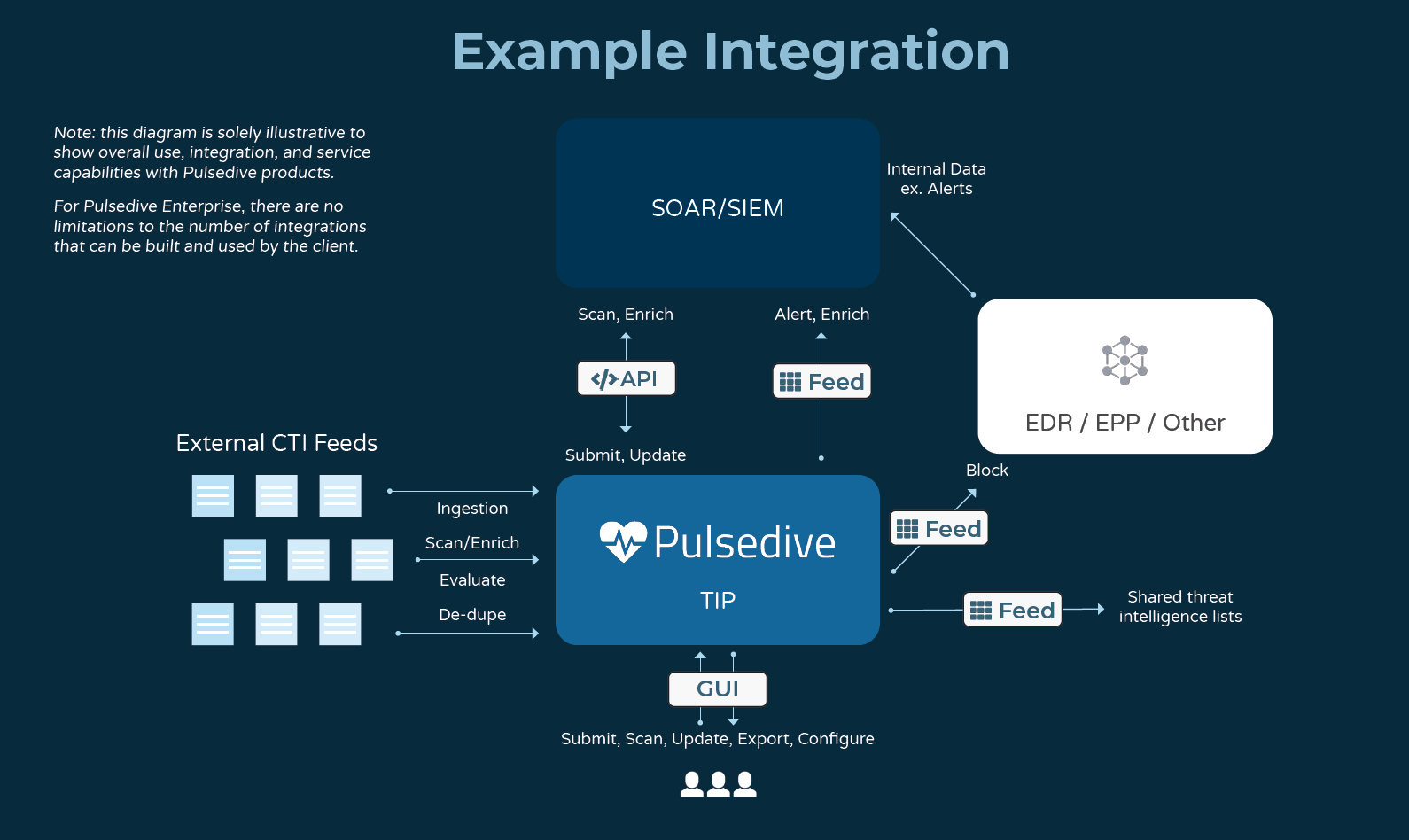
Does Pulsedive integrate with [insert software here]?
We design our API and Feed to be easily integrated with most tools - in JSON, CSV, and STIX/TAXII 2.1 formats. In addition to enabling custom integrations, we maintain a non-exhaustive list of integration partners here: https://pulsedive.com/about/integrations
If you have built or would like to see a new integration, reach out to us at support@pulsedive.com.
Which paid Pulsedive products are best for which use cases?
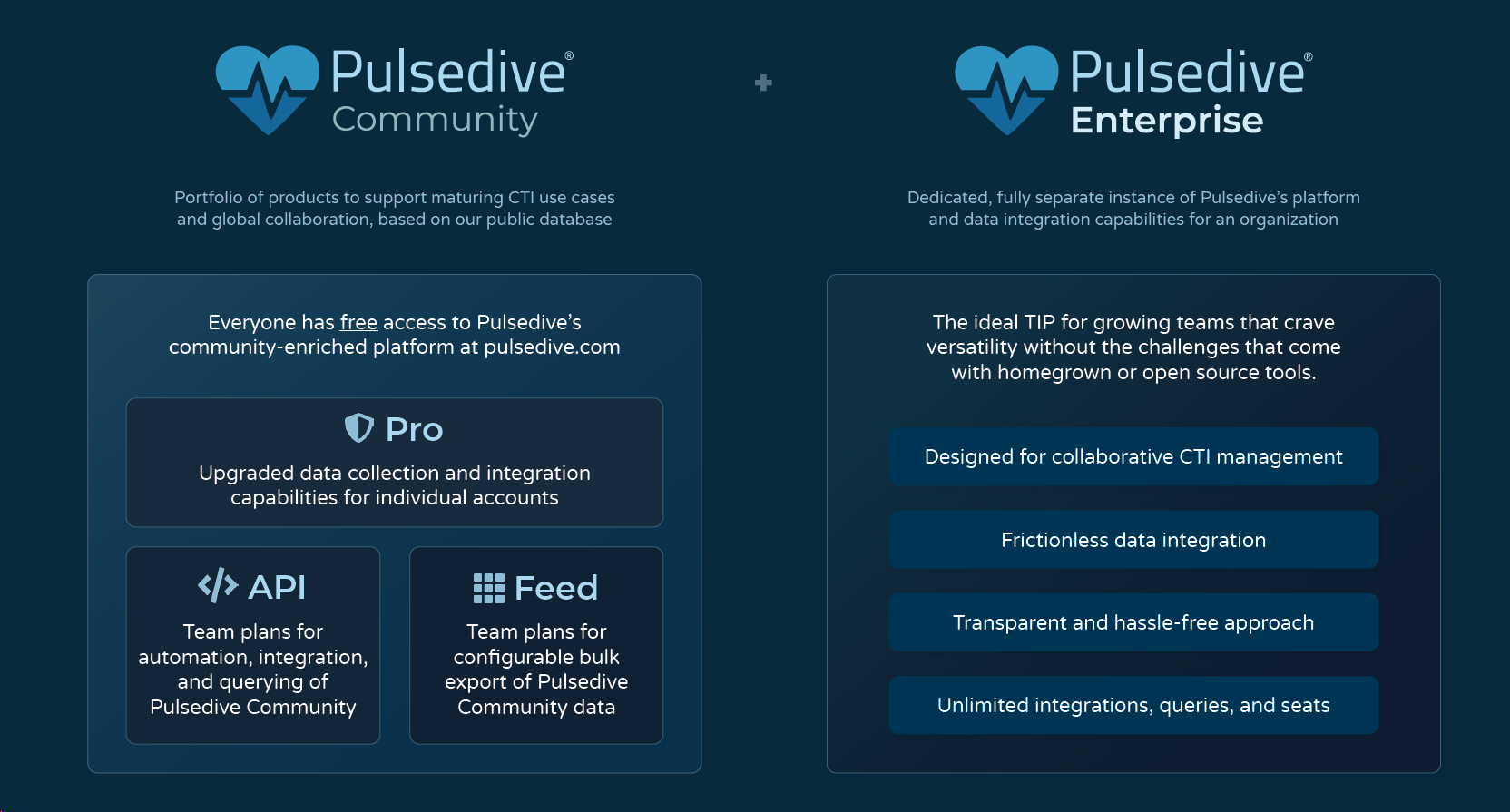
Pro: Ideal for individual analysts, researchers, and hobbyists to support analysis and personal projects. Pro comes with upgraded capabilities, like historical screenshots, 3rd party integrations, increased Analyze limits and Explore results, and more. Bundles are also available for security teams using the Pulsedive GUI for triage and research.
API: Recommended for on-demand lookups, enrichment, and scanning. Many customers leverage the Pulsedive API to enrich alerts, tickets, and other workflow steps with SIEM and SOAR solutions. Our flexible API also makes custom integrations a breeze. Check out the API docs to learn more.
Feed: Best configurable bulk export of Pulsedive's dataset for high-volume enrichment, alerting, and blocking. Available in CSV and STIX/TAXII 2.1 format. Popular use cases include alerting on IOCs, enriching logs, and blocking potential threats.
Our products are complementary, so each team may use one, two, or multiple combinations of our products within their security stack. See below for common ways customers use our products.
Enterprise: When you want a private Pulsedive platform all to yourself. See the next question for more details.
What if I want a private version of Pulsedive’s platform just for myself/my team?
Check out our Enterprise TIP. Our Enterprise TIP is a dedicated, private, cloud-hosted threat intelligence platform that takes all the functionality you know and love from Pulsedive with flexible customization and advanced threat intel management - just for your team. Enterprise is ideal for growing teams that crave versatility and affordability, without the challenges of maintaining homegrown or open-source systems. Learn more in our brochure or drop us a note at sales@pulsedive.com.
Where can I learn more about Pulsedive?
Learn about Pulsedive on our About pages. In addition, discover more about company behind Pulsedive on the Security Podcast of Silicon Valley, the team in our SecurityTrails interview, perspectives in our SafetyDetectives spotlight, or research into sharing practices at our SANS CTI Summit talks. We also have a Slack channel if you ever want to ask us a question directly!
Have questions? We have answers! Email support@pulsedive.com

