Hunting in The Home Lab: Putting Cyber Threat Intelligence into Practice
Case Study: Arch Cloud Labs implements hobbyist-friendly solutions like Pulsedive Community and Pro to research, track, and share wide-ranging personal security projects, from investigating cryptojacking malware actors to hunting for CVEs.
Case Study: Arch Cloud Labs implements hobbyist-friendly solutions like Pulsedive Community and Pro to research, track, and share wide-ranging personal security projects, from investigating cryptojacking malware actors to hunting for CVEs.
Threat Intelligence for the Community
Home lab enthusiasts experience a frustrating lack of access to key threat intelligence tools and services used by professional security analysts, incident responses, hunters, and reverse engineers.
Often, limited or out-of-range pricing and licensing options set by intelligence vendors exclude independent researchers and home users from the benefits of the latest threat intelligence research.
Arch Cloud Labs set out to find, evaluate, and share affordable (including 100% free!) resources. The goal was to help all security enthusiasts interested in threat intelligence know where to look and share best practice examples to get the most out of the top cybersecurity community resources.
About Arch Cloud Labs
Arch Cloud Labs is a personal security home lab and blog run by Jared, a Professional Security Engineer. Currently hosting a handful of honeypots, SIEMs, and various virtual machines, Jared uses Arch Cloud Labs as a space to test new technologies, investigate ongoing threats, share tutorials, and openly disseminate findings with the security community.
Follow Arch Cloud Labs
- www.archcloudlabs.com
- Github: archcloudlabs
- Twitter: @DLL_Cool_J
Pulsedive features used:
- Indicator lookup, enrichment, and pivoting
- Threat infrastructure research
- Pro Tier API for automated & on-demand scanning
What I love most about Pulsedive is that it gives me, a home lab enthusiast, the ability to use threat intelligence data I would not otherwise have access to.”
- Jared, Arch Cloud Labs
Maximizing Pulsedive’s Threat Intelligence Platform
Arch Cloud Labs first came across Pulsedive in the buzz of Infosec Twitter and discovered its value for multiple threat research workflows. On one hand, Pulsedive provides convenient manual lookup and automated enrichment for domains, URLs, and IPs observed in home lab honeypots to perform deeper investigation and analysis. On the other, the Pulsedive platform helps track known and current threats - supporting new research and correlation. Below are a few key use cases.

Use Case 1: Contextualizing Honeypot Data
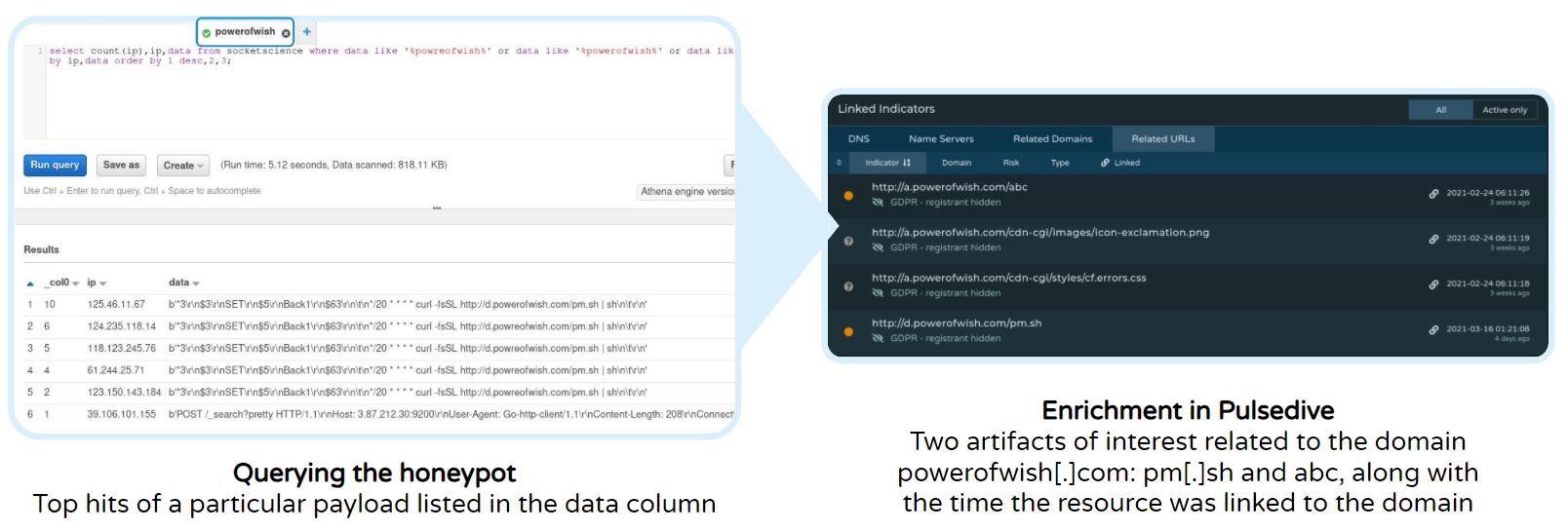
Context: Arch Cloud Labs hosts multiple honeypots for data collection, storing logs in an S3 bucket, and obtaining data insights via Amazon Athena queries. Athena treats S3 like a SQL backend enabling SQL queries to obtain information from an S3 bucket.
Indicator Enrichment: Arch Cloud Labs found other files hosted on target domains through Pulsedive’s Linked Indicators section available on every indicator page. By pivoting through other hosts associated with a target domain (in this case, powerofwish[.]com), Arch Cloud Labs identified further infrastructure and artifacts.
Running Samples: Arch Cloud Labs subsequently reached out via a download host to see if the files are still hosted externally. Used in conjunction with other free solutions like URL analysis sites and malware sandbox solutions, any home enthusiast can obtain and run samples - even those no longer publicly hosted - to gain insight on process execution without the need to set up their own environment.
Use Case 2: Hunting For Known Threats
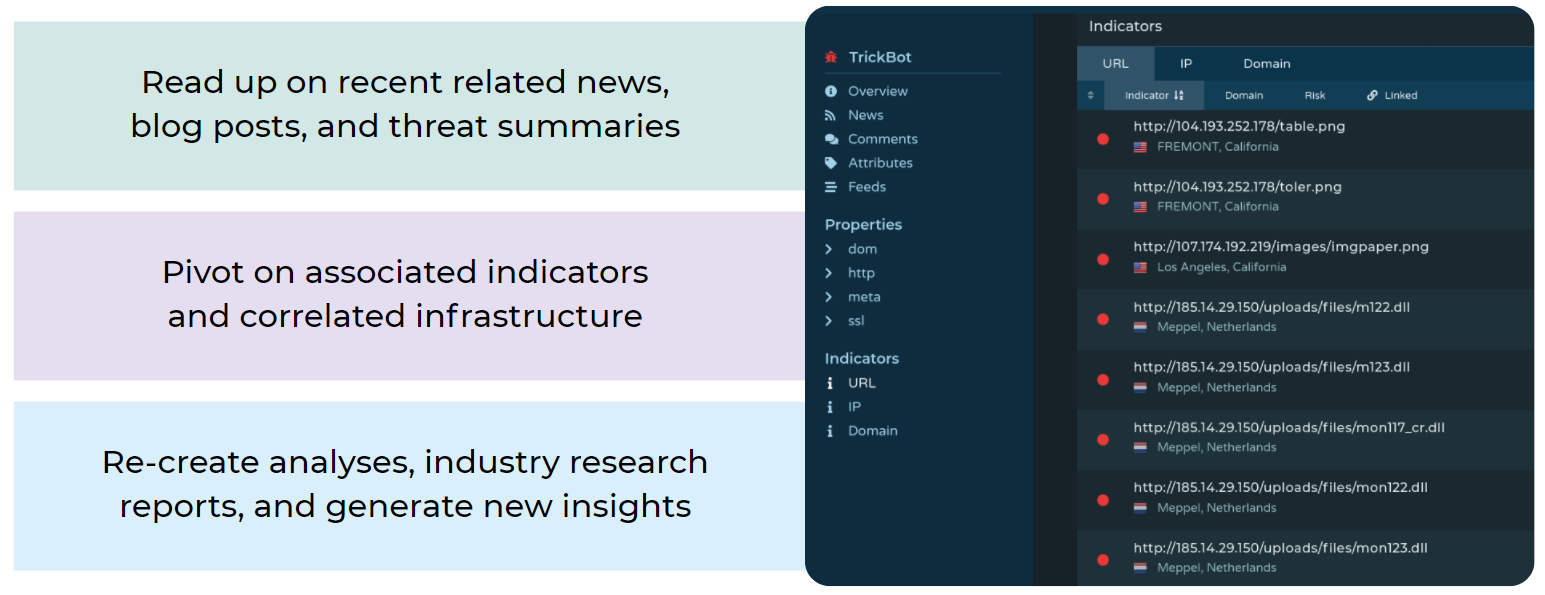
Staying Sharp by Staying Informed: Hobbyists like Arch Cloud Labs keep skills sharp by tracking and researching current threats found in security news headlines, Infosec Twitter feeds, and Reddit /netsec posts. This allows Arch Cloud Labs to recreate existing industry analysis, understand and compare different threats, and contribute to community knowledge.
However, in-depth practical research benefits from access to many levels of threat intelligence - from high-level summaries and news to detailed technical data points. While security enthusiasts are often eager to learn more about the current threat landscape, there are limited free and affordable channels to access comprehensive threat information.
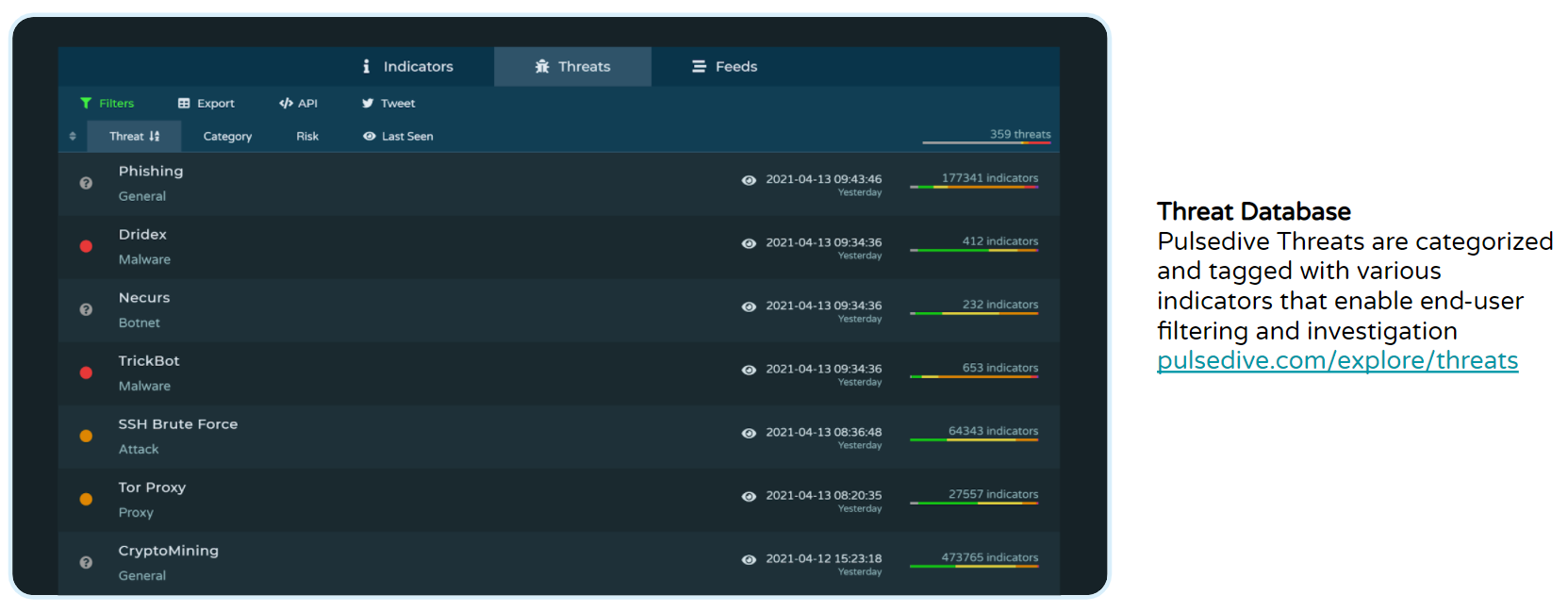
Arch Cloud Labs uses Pulsedive’s free and open threat database to search, filter, and track the latest threats, ranging from general phishing attacks to specific malware variants like Dridex and TrickBot. Access to Pulsedive’s threat profiles provides any security enthusiast with knowledge of reported C2 IPs, malware hosting domains, related news, shared infrastructure characteristics, and additional helpful context for further investigation.
Tackling Trickbot: Most commonly distributed via phishing emails against targeted businesses, a home lab enthusiast typically lacks the visibility into TrickBot that enterprise security operation teams possess. Arch Cloud Labs uses Pulsedive to pivot within living threat profiles to gain unique insights into ongoing activity to bridge this gap.
Diving into ‘Risky’ Business: A favorite pastime of Arch Cloud Lab - identifying odd and overly descriptive file names related to known threats to kick off an investigation. In one particular case, Arch Cloud Labs generated a list of recent TrickBot domains based on risk level and uncovered a series of high-risk URLs resembling files from a college group project.
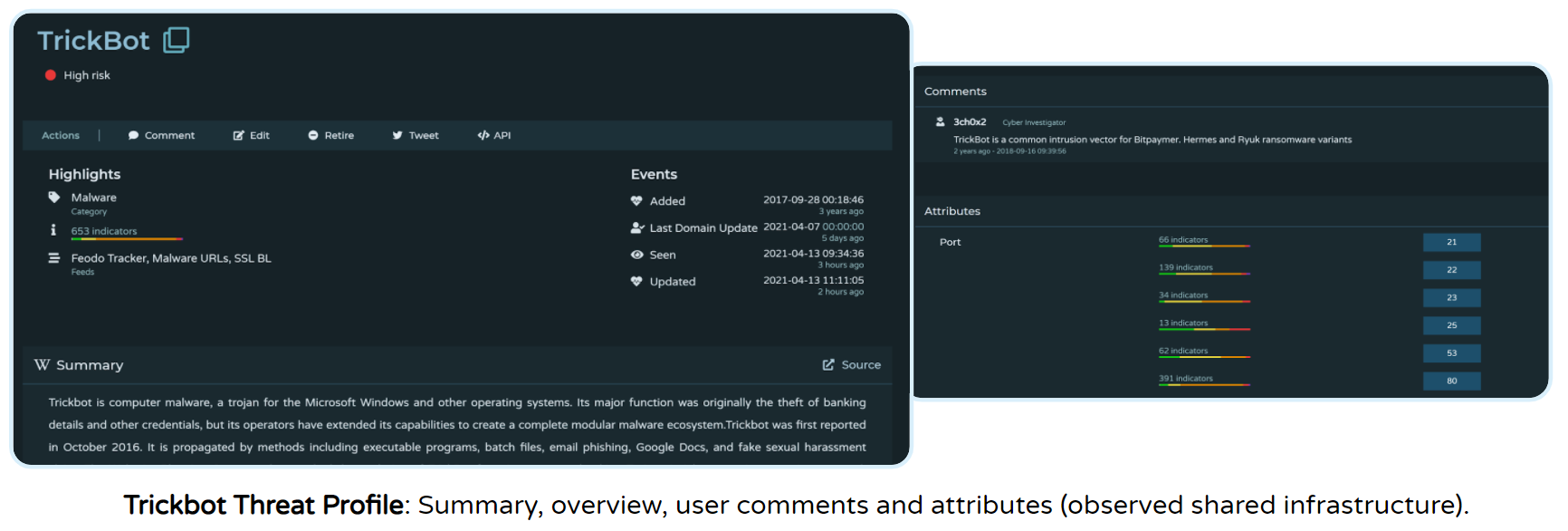
While the domain was no longer hosting the files when identifying associated IPs, Arch Cloud Labs successfully recovered the files, downloaded samples, and ran analyses by pivoting to complementary free file analysis tools. This combination of tools allows users to recreate analysis in other blogs/reports and find slight differences in prolifically distributed malware samples like Cryptojacking variants.
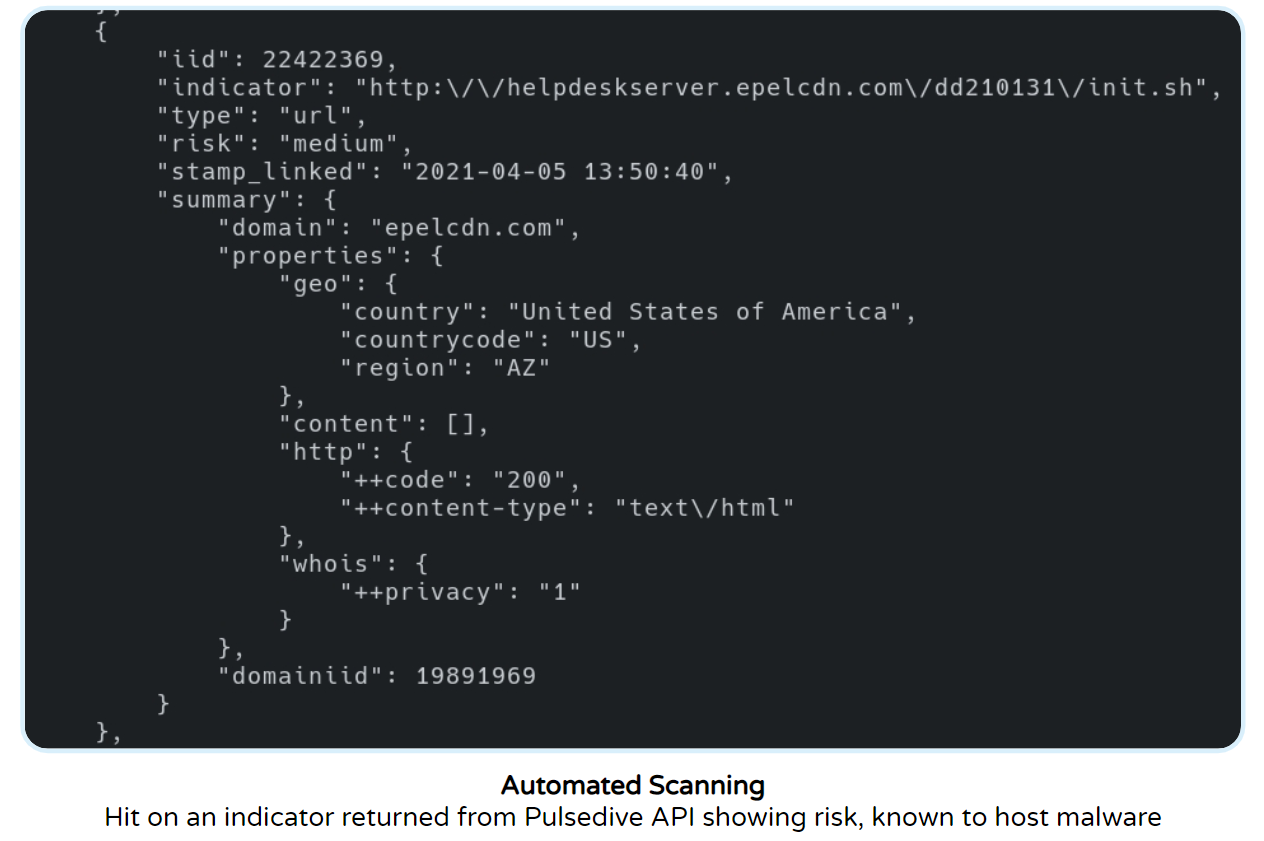
Use Case 3: Automated Enrichment & Detection
By leveraging the Pulsedive’s scan API endpoint, Arch Cloud Labs has also automated on-demand scanning of IPs from home lab honeypots to rapidly identify if a host is known to be malicious.
Threat Intelligence for All
At Pulsedive, we believe home lab hobbyists like Arch Cloud Labs deserve affordable means to access, pivot on, and integrate with comprehensive sets of timely threat intelligence.
As a community- and user-driven platform, Pulsedive will continue supporting individual user research and intelligence sharing efforts - and look forward to contributing to many projects to come.
More Data, Fewer Tabs.
Designed for individual security users, Pulsedive Pro provides even more data built right into the Pulsedive interface and integrated with other tools. Pro adds screenshots, higher API limits, critical-risk feeds, third-party integrations, and more - complete functionality to streamline threat intelligence investigation and analysis. The result?
Easy triage, research, and integration, without the enterprise price tag.

