Leveraging Threat Intelligence in Security Operations
Explore the essential role of Cyber Threat Intelligence (CTI) in understanding and mitigating cybersecurity threats - detailing its types, processes, and effective implementation in enhancing security operations and incident response.

Understanding and mitigating threats is essential for organizations and to enable security operations and ultimately reduce risk. Cyber threat intelligence (CTI) plays a vital role in this effort, allowing teams to collect, analyze and act on contextualized information in a timely manner. This blog explores the fundamentals of what CTI is, types of intelligence, processes, use cases, and examples of effective implementation in security operations and incident response functions.
What is Cyber Threat Intelligence?
Cyber Threat Intelligence (CTI) is the process of collecting, processing and sharing information about cyber threats. This information is distilled from various data points that provide users additional information about a risk.
- Actionable: Does the information allow stakeholders to make decisions based on what is available?
- Timely: Is the information stale or does it have value in being actioned?
- Relevance: Does the information provide insights into an issue that affects stakeholders or is it just general knowledge?
In using this criteria for CTI, threat intelligence analysts must have organizational knowledge in addition to knowledge about threats and vulnerabilities in order to categorize and prioritize the information being collected. Since it is not possible for a single business unit to have perfect knowledge about an organization, threat intelligence functions should be able to identify relevant stakeholders that should be getting information regularly or on an ad-hoc basis.
Types of Cyber Threat Intelligence
For Cyber Threat Intelligence to be effective, it needs to be appropriate for the consumer of such information which may cover a broad audience range depending on the intelligence disseminated. For example, providing tactical level information such as indicators of compromise (IoCs) or detailed technical intrusions to C-level executives and a board of directors is not as useful for them as informing them about long-term trends and risks. On the flip side, providing high-level insights and predictions about sector or geopolitical risks would not be as useful for a security operations team as updated IoCs and TTPs to prevent immediate threats and active campaigns. The Actionable criterion can help determine what sort of information needs to be shared with different audiences. For example, network IoCs can potentially be blocked using firewalls if that information is shared with networking teams. As such, CTI often gets bucketed into three categories: strategic, operational and tactical intelligence.
- Strategic Intelligence: Provide details about the threat landscape and risks for an industry vertical or geographic region. These details are used to inform decision-makers and high-level executives about risks and serve to guide stakeholders for long-term strategies and investments
- Operational Intelligence: Provide details about specific threats, events, and attacks. The purpose is to understand the timing and nature of future attacks, determine attack vectors, perform hunts, and remediate risks. This information looks to answer the following questions:
- Who
- What
- Where
- Why
- When
- How - Description of how intrusions took place
- Tactical Intelligence: This includes detailed descriptions of attacker tactics, techniques and procedures (TTPs) and IoCs. Allows responders and security teams to search across security tooling for additional signs of compromise and guides response direction, prioritization of patching, and timely monitoring/triage of alerts.
Great CTI Resources


How CTI Works - The Intelligence Lifecycle
Cyber Threat Intelligence and threat intelligence work as a whole follows a lifecycle. The process begins with planning and direction -guiding what type of data is collected and how it is processed, as well as goals/motivations behind the collection. Once finished intelligence products are shared (dissemination), feedback is invaluable to identify and understand the usefulness of the information shared and any gaps moving forward. This feedback should be incorporated in the next collection cycle to ensure that the data being collected is fulfilling the intelligence requirements.
- Planning and Direction
- Align the CTI process and efforts to specific organizational needs and priorities.
- Identify what CTI is being used to achieve and the intelligence requirements that collection must satisfy.
- Identify the personnel involved in producing reports and stakeholders who will receive finished intelligence products.
- Collection scope and information turnaround time should also be defined at this stage.
- Collection
- Collect data and sources which will then be converted into intelligence.
- Collection may involve leveraging various sources to get the required data points, including both internal and third party data, on a scheduled or unstructured basis.
- Processing
- All collected data needs to be processed in a repeatable way to ensure that it is relevant and accurate.
- This may involve cleaning data and converting it into a structured standard format or translating information from various languages into a single language for ease of review.
- Processing is a mix of automation and human efforts, including rules-based and manual methods.
- Analysis and Production
- The processed information is analyzed to draw conclusions and recommendations along with identifying indicators of compromise or attack that can be provided to other teams.
- All analyzed intelligence must be converted into a finished product that can be shared with the stakeholders identified in Stage 1.
- Sharing (Dissemination) and Feedback
- Intelligence products are shared with stakeholders, which may include internal teams, partners, trusted sharing platforms, external audiences, and more.
- Feedback is solicited and incorporated into the next collection cycle.
CTI Use Cases
Security Operations
Security Operation Centers are one of many security teams that may benefit by incorporating CTI into their workflows.
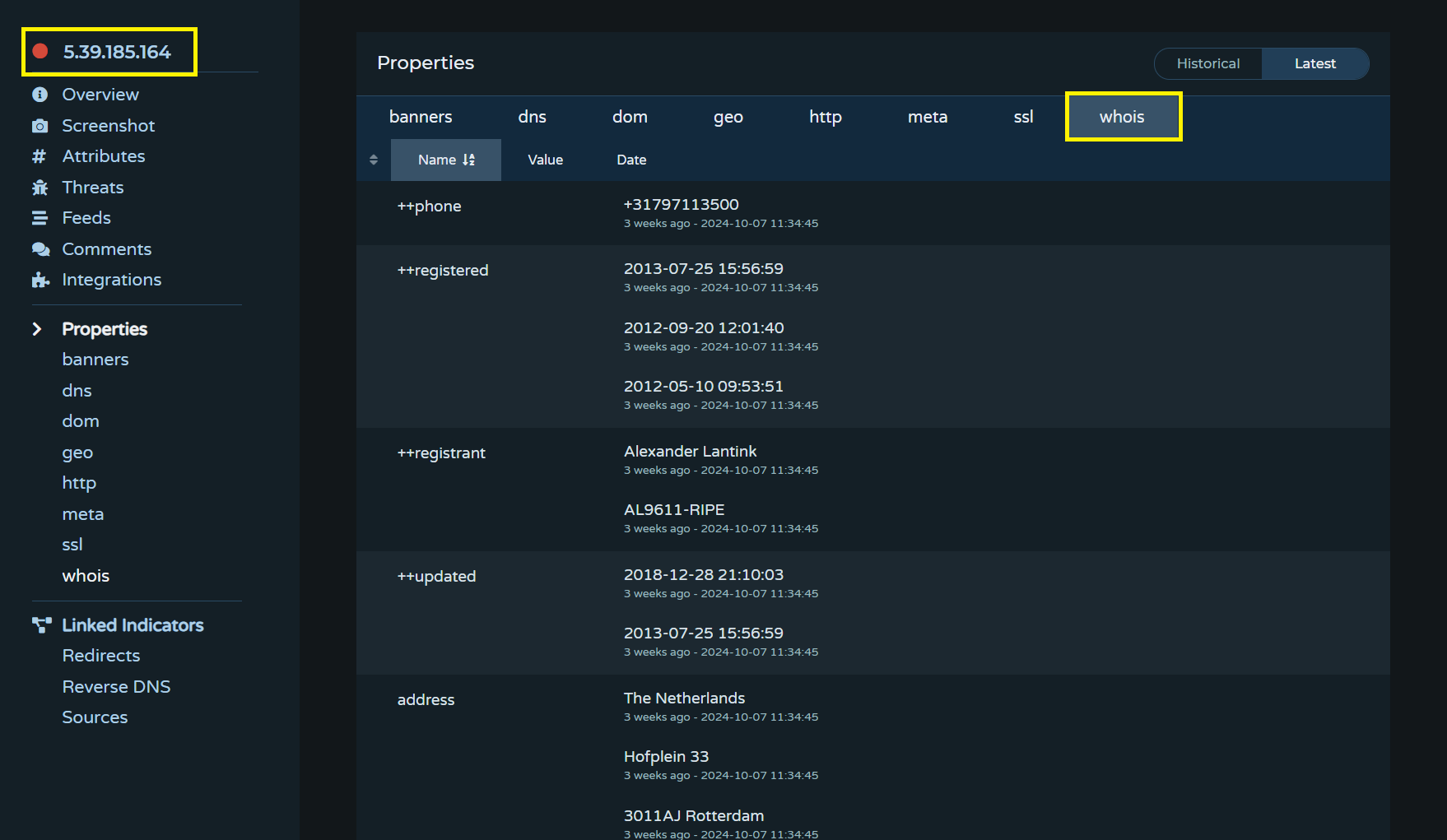
Enriching Security Alerts with Contextual Information
Security analysts often spend significant time looking up information such as IP geolocation data, domain metadata such as WHOIS records or registrar information. This information provides valuable context about assets involved in security alerts and may help analysts determine if an alert can be categorized as benign, suspicious or malicious.
Alerts focusing on Indicators of Compromise
Indicators of compromise can be incorporated into blocklists or watchlists on security tools. These lists alert on when specific indicators are observed within the environment. When high fidelity indicators are leveraged, these often yield high true positive rates and signs of an ongoing security incident. Proactive blocking of processes or network connections based on IoCs is another capability that many EDR or network security tools offer, these can be used to terminate malicious processes when they are observed in an environment.
Another way to leverage indicators of compromise is to hunt for them within environments. Security tools can be used to search for the presence of IoCs that have been shared by security researchers throughout an environment. Hits on these IoCs may lead to the discovery of a previously undiscovered incident.
Vulnerability Management
Incorporating threat intelligence within vulnerability management processes can help prioritize the order in which applications are patched. Intelligence can provide insights into which vulnerabilities are being actively exploited, which have exploit or PoC (proof-of-concept) code available and any additional indicators of compromise that teams can look for. Cyber threat intelligence teams can also share additional information on what threat actors can do with a particular vulnerability and how it can potentially be leveraged in intrusions.
Incident Response
Apart from proactive detection through intelligence driven alerting in security operations, threat intelligence can guide incident response efforts as well. Information on adversary TTPs can help inform responders on what to look for and may provide details about how a threat actor gained access into an environment. TTPs may also indicate what operations threat actors may perform in the environment along with the tools they may use. By leveraging information from other incidents, responders may be able to disrupt and contain hands-on keyboard activity before intrusions progress down the killchain.
Integrating Threat Intelligence in Your Security Tech Stack
By integrating threat intelligence in your existing cybersecurity tools, teams can drive improved security outcomes. Here are a few common ways threat intelligence connects to other technologies:
- SIEM (Security Information and Event Management): This tool helps you collect and analyze security event data from multiple sources for centralized monitoring and detection of potential threats.
- Centralized Log Management: This integration will help you analyze logs from different systems and applications to identify patterns and indicators of compromise.
- Endpoint Detection and Response: Integrating threat intelligence with an endpoint detection and response solution will allow you to detect and respond to threats targeting individual devices or endpoints within your network.
- Firewall/Antivirus: By incorporating threat intelligence into your firewall and antivirus tools, you can enhance their capabilities to identify and block malicious traffic/malware based on known threat indicators.
- IPS and IDS: By correlating internal and external data through threat intelligence, you can enhance the effectiveness of your IPS (Intrusion Prevention System) and IDS (Intrusion Detection System).
Conclusion
Cyber threat intelligence plays a vital role in helping organizations understand their threat profile and fortify their security defenses to minimize the impact of cyber incidents. Threat intelligence can be leveraged by different teams as a centralized hub of relevant, timely, and actionable knowledge. For more information and resources, check out the links below.
References
https://www.youtube.com/watch?v=J7e74QLVxCk
https://www.memcyco.com/6-stages-of-the-threat-intelligence-lifecycle/
https://www.recordedfuture.com/threat-intelligence
https://www.paloaltonetworks.ca/cyberpedia/threat-intelligence-use-cases-and-examples




