Operationalizing Cyber Threat Intelligence in a Managed SOC
Case Study: Ingalls Information Security strategically develops their cyber threat intelligence program with Pulsedive solutions - all while scaling the SOC more than 10x over 2 years

Case Study: Ingalls Information Security strategically develops their cyber threat intelligence program - all while scaling the SOC more than 10x over 2 years
The Need for Speed & Visibility
Ingalls Information Security ('Ingalls') is a Louisiana-based security consulting team serving a diverse range of customers including state, local, and education (SLED), non-profit, institutional, and commercial organizations all over the US. Ingalls helps organizations manage cyber risk through multi-faceted incident response, managed detection and response, professional services, and government programs offerings.
Prioritizing Cyber Threat Intelligence
Many incident response client referrals transition from IR engagements with Ingalls to ongoing managed detection & response (MDR) consulting. During these shifts, Ingalls identified cyber threat intelligence as a priority focus area - to better understand and track continuously changing threat landscapes. In order to expand visibility into the threat actors and TTPs impacting clients, the team sought to mature their in-house intelligence resources.
By making strategic investments in the right mix of people, processes, and technologies over time, Ingalls could more effectively detect, investigate, and respond to both well-known and emergent threats.
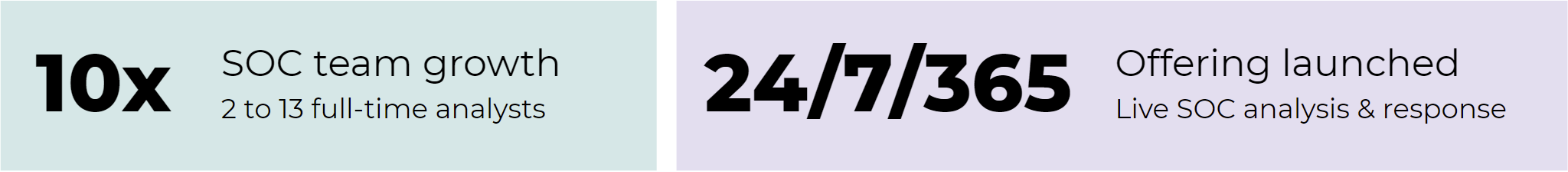
Holistic Growth
Read on to learn how Ingalls has successfully grown their integrated threat intelligence program by leveraging tools like Pulsedive, while also:
- Scaling from 2 to 13 full-time security analysts
- Launching a 24/7/365 live analysis and response SOC offering with CTI research capabilities
- Maintaining clear company vision, operations, and commitment to employee wellness
Top Pulsedive Features
- Automate enrichment of IOCs in SOAR playbooks with API
- Investigate and pivot on domain, IP, and URL data points in the community platform

Starting with the SOAR
Automating Enrichment to Accelerate Analysis
Ingalls initiated the integration of threat intelligence sources in MDR playbooks through vendor research and testing. When exploring Siemplify’s pre-built SOAR integrations, Ingalls found the Pulsedive API and began implementation. The straightforward Pulsedive deployment within the SOAR made it easy to automatically enrich domain and IP alerts from customer environments to support faster, more informed analysis and response.
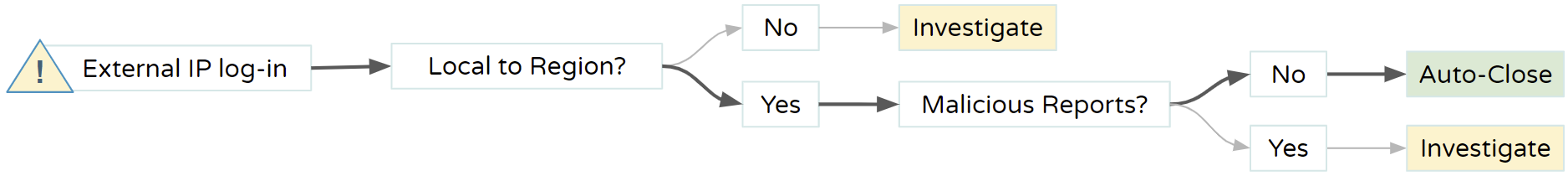
Example: Reducing Noise
By implementing workflows leveraging Pulsedive’s geo-IP data, the SOC automatically categorizes and reduces noise from SOAR platform alerts. Auto-closing alerts with IP addresses local to the region, that do not have reports of malicious behavior, help the analyst team stay focused on valuable research.
Building out the Analyst Toolset
Additional Research & Contextualization
The Ingalls team has since expanded the use of Pulsedive data to provide additional context around IOCs. During intelligence analysis and processing, analysts search and perform scans on domains, URLs and IPs to investigate potential risk and retrieve relevant information like WHOIS and geoIP information, HTTP headers, SSL certificate metadata, DNS records, and related indicators.
Pulsedive is a part of Ingall’s core analyst toolset, used in conjunction with malware sandboxes and open source feeds. This robust array of web applications and security solutions allows the growing team to work effectively in identifying and defending against threats such as phishing campaigns, ransomware, and more.

Expanding - and Sharing - Threat Intelligence Best Practices
Ingalls has continued to expand in-house threat intelligence capabilities, going beyond curating intelligence sources to also provide dark web research, breach monitoring services, and educational content.
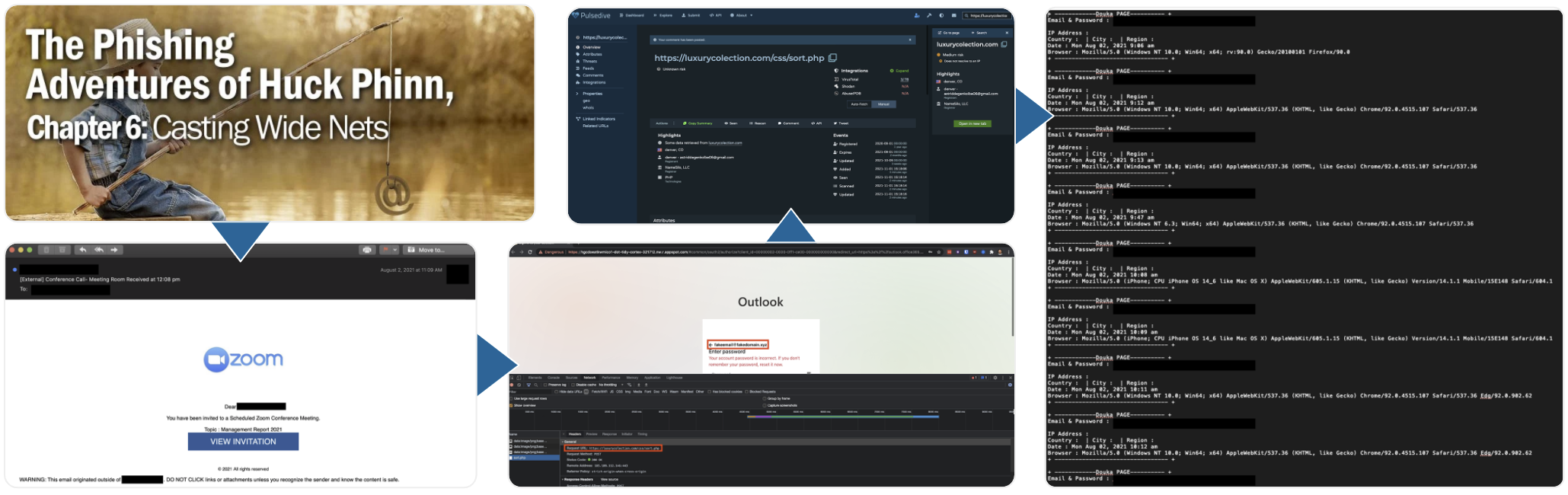
As part of their outreach and awareness efforts, the analyst team publishes insights from real-world investigations. For example, their “Phishing Adventures of Huck Phinn” series covers tips, tricks, and best practices to make the most of CTI tools like Pulsedive with other security practitioners.
What’s Next: With a threat intelligence lead joining the team, the formalized CTI function will act as a strategic analysis center and sophisticated knowledge hub that supports all of Ingalls’ business lines.
Pulsedive API
Integrate Pulsedive into your workflow.
Seamlessly integrate Pulsedive’s data and scanning capabilities with your existing ecosystem, custom solutions, or automated workflows to improve your security posture.
Pulsedive gathers and processes threat intelligence worldwide, producing easy-to-consume data returned in JSON format. The API allows you to contextualize, prioritize, automate, and simplify on-demand.

