Updates: Features, Integrations, Mentions
A round-up of all recent things Pulsedive. 5.1 release, Microsoft Sentinel and Cisco SecureX integrations, plus mentions in the news.
A round-up of all recent things Pulsedive.
Released: Pulsedive 5.1
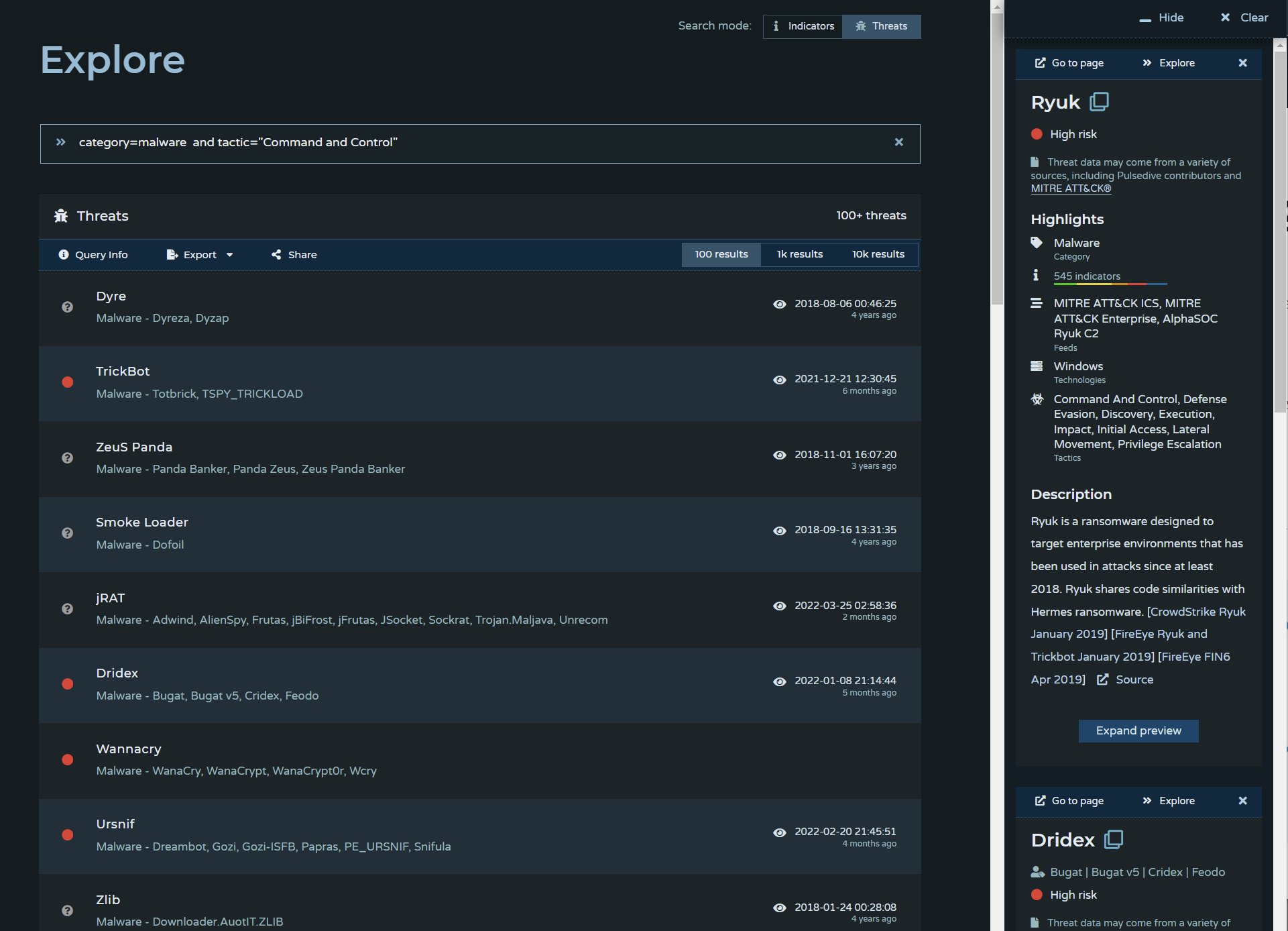
The Pulsedive 5.1 release introduces "Explore for Threats", which allows users to search across our threat dataset with boolean logic and wildcards.
You can search threats with any combination of threat name, alias, category, risk, last seen timestamp, feed, and threat attribute. Check out the Explore Guide at pulsedive.com/explore/threats/ to get started.
New: Microsoft Sentinel & Pulsedive Feed Data Connector
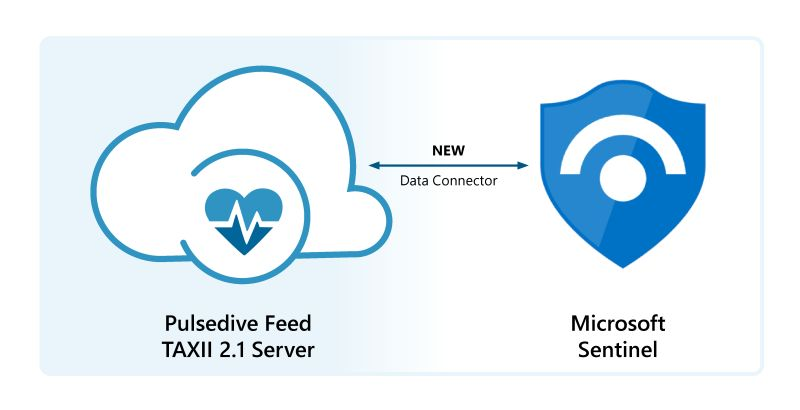
Pulsedive worked with the Microsoft Sentinel team to import the Pulsedive Feed using the Threat Intelligence – TAXII Data Connector. With Microsoft Sentinel + Pulsedive’s cloud-native deployment, combine known threats from around the world with world-class analytics, modeling, detection, and investigation. Read on at Microsoft's announcement below:

Updated: Cisco SecureX Threat Response & Pulsedive
As a Cisco Secure Technical Alliance Partner, Pulsedive recently updated our dedicated partner page to showcase the capabilities of our integration. If you use Cisco SecureX Threat Response, it's easy to leverage Pulsedive's enriched CTI datasets to support investigation and analysis. Check it out here: https://www.cisco.com/c/en/us/products/security/technical-alliance-partners/pulsedive.html
Mention: Best Threat Intelligence Solutions (cybernews)
The commercial cyber threat intelligence solutions market can be complex and hard to navigate. Cyber threat intelligence programs require an evolving mix of the right talent, operations, and technologies; understanding which tools, managed services, and skill sets are worth the time to invest in and operationalize is a major challenge. At Pulsedive, we take an honest approach with ease of access and a user-focused experience.
That’s why we’re happy to announce that Pulsedive has been included in a list of top threat intelligence solutions by cybernews. Their research team compiled services, available resources, and summarizes key offerings of each solution for readers. Scroll to the end to find their final recommendations list (with links) to learn more about different providers in the CTI domain.

The lists aim to help professionals better navigate through their digital lives. Beyond threat intelligence, the team also covers topics like VPN comparisons and cyber war news.
Mention: Gaining More Insight Into Malicious Domains (dotmagazine)
Pulsedive & Realtime Register have worked together for years, collaborating on better ways to mitigate widespread DNS abuse (see: our case study). The team uses several products for different use cases: the Feed for automated ingestion, API for on-demand scanning and enrichment, and the Community Platform UI to research, pivot, and contribute known malicious domains.

This post details how the Realtime Register team sought to adopt an IR-inspired approach to malicious domains, seeking to proactively address threats, instead of the current time-consuming and costly method of reacting to abuse reports.
"It’s a combination of good data sources, sound systems, and an effective process.... built around five principles: Gather, analyze, share, exchange, and respond, referring to what can be done with threat intelligence in general and, in particular, regarding malicious domains: Gather data from high quality domain reputation feeds, use good analysis tools that allow detailed correlations (visualizations are a great plus), share with registries, resellers and other parties who can act on the information to mitigate the threats, exchange information with those who may have related information that is of interest and respond by acting on the actionable information in order to mitigate the threats."
BONUS: What's on a Pulsedive Page?
It is an interesting UI challenge when the CTI community loves having access to "all the data right up front", while maintaining hierarchy and flow. To help new users orient themselves on our information-rich IOC and Threat pages, we developed 2 graphic guides that explain our approach and the types of data available:
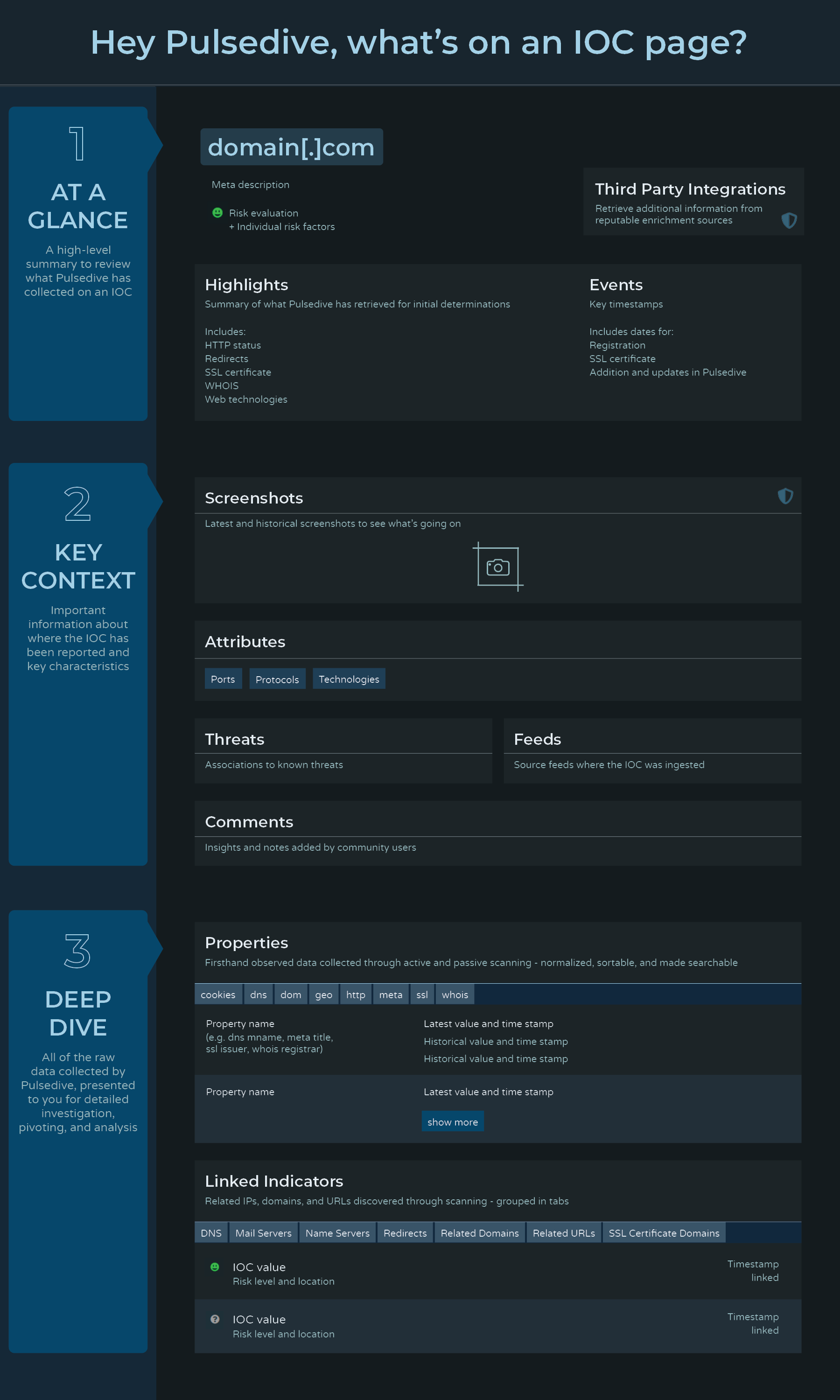
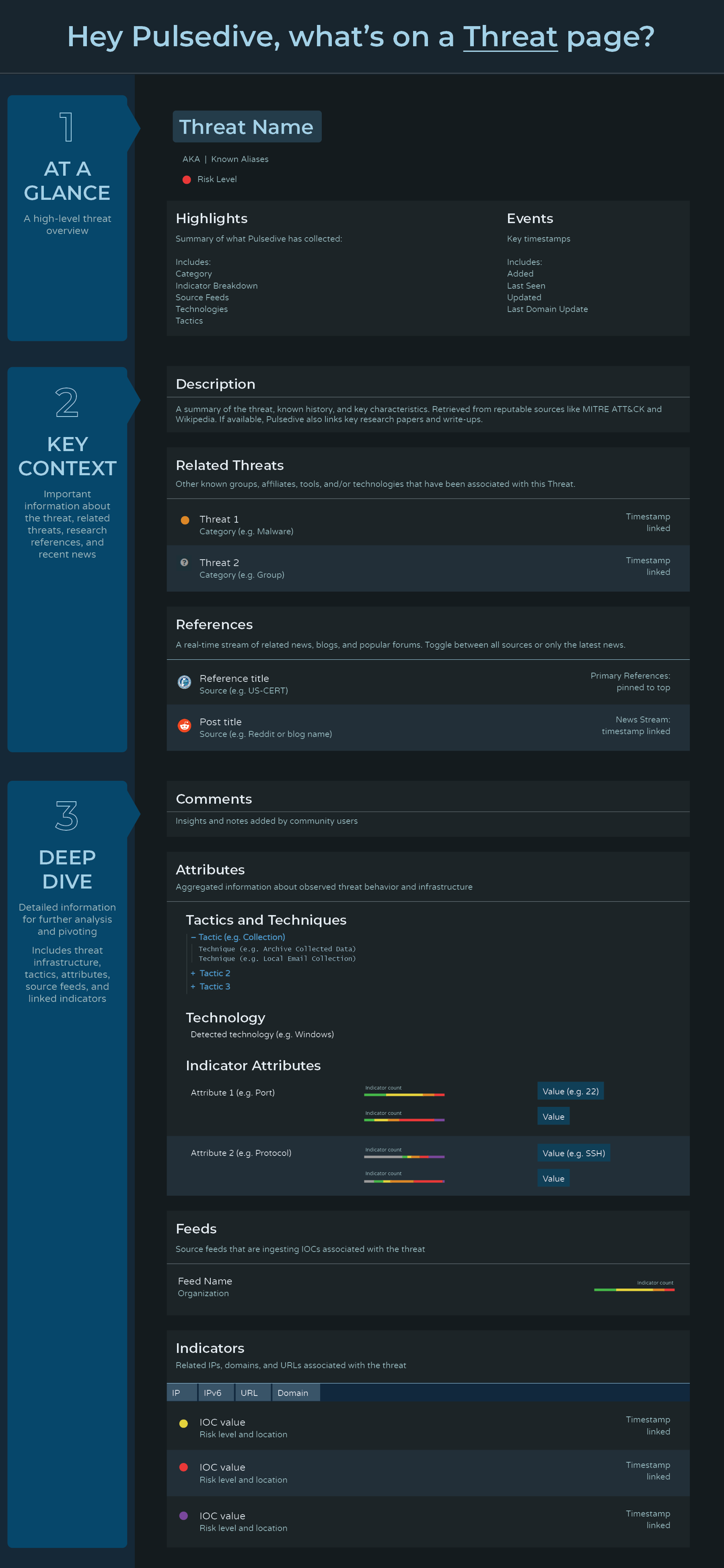
That's all, folks! Thanks for your all your continued feedback and support - more to come.
Contact us anytime at support@pulsedive.com or join our Slack to send a message.



