Should You Pay Hacker Ransom?
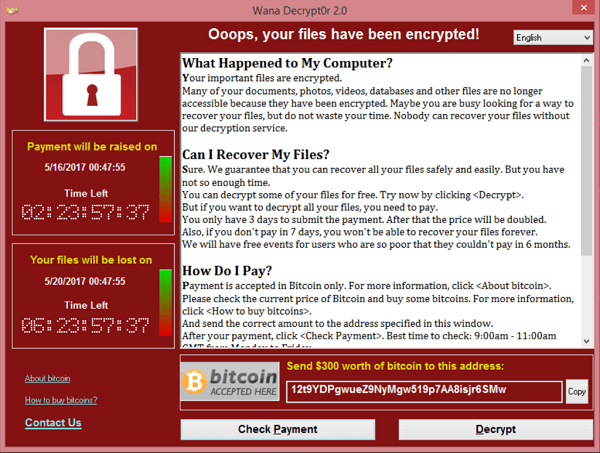
If you haven’t heard by now, Uber paid hackers $100,000 in ransom last year in exchange for deleting the stolen personal information of 57 million victims. Hackers have also been know to demand ransom for DDoS attacks, malware, IP leaks, and now infrastructure disruptions.
More companies than you’d think actually give in to ransom demands; ZDNet reported last year that two-thirds of companies affected by a wave of ransomware ended up paying the ransom. It makes sense, as ransomware in particular can have detrimental and lasting effects on businesses:
- Critical scripts, applications, or databases are encrypted, bringing business products or sites down.
- Important documents are encrypted and employees can’t do their work, stopping important business processes.
- Intellectual property or media is encrypted, resulting in the loss of many hours of work and production delays.
And that’s just for ransomware. DDoS attacks can take entire networks down, IP leaks can affect profits, and security breaches could lead to identity theft or even insider trading, all of which can translate to direct or indirect losses.
From a financial perspective, it might make sense to pay the ransom. Time is money; a business is potentially losing thousands or millions of dollars for each hour of downtime, incident response, legal involvement, etc, so paying a few thousand dollars ransom sounds like a quick fix to get things back up and running smoothly. Unfortunately, paying ransom might do more harm than good for your business and for society, and here’s why.
There’s no guarantee paying ransom will do anything.
As that ZDNet article writes, “some companies have discovered the hard way that cybercriminals are not to be trusted, with many only paying hackers to unencrypt their files only to find that they never get their data back.”
In Uber’s case, they paid the hackers to contain the breach, but there’s no real assurance the data hasn’t gotten out. The hackers could claim to have gotten rid of it while selling it on the side for more money, or someone else could have inadvertently gotten a hold of the dump.
In the more immediate case of getting business processes up and running, put simply there is no guarantee that will happen by paying the ransom. The best course of action is to contact authorities.
You may still be legally required to disclose a breach.
Paying ransom might cost a few thousand dollars and, if kept quiet, could save some face. But if the breach is discovered, and it probably will be, the fines, legal fees, and damage to a business’s reputation could cost millions, or worse.
By law and depending on the situation, a business may be legally obligated to disclose a security breach; more information by state can be found here. So if you think paying the ransom to keep things quiet will make things go away, you’re probably breaking the law.
It’s not easy to cover up a security breach.
If that’s your goal that is. Sure, Uber may have gotten away with it for a time, but the data breaches at Target and Home Depot, for instance, were actually first reported by Brian Krebs on his blog, Krebs on Security. Days after Krebs broke the story on Home Depot, they went public, and that did not look good for Home Depot.
And, well, if people find out not only about the breach but that you also tried to cover it up… let’s just say that probably won’t go down well.
You don’t know where the money is going.
If we knew who these hacker groups are, it wouldn’t be smart for them to execute these attacks. They could literally be anyone, from hostile nation states like North Korea and groups involved with ISIS and other terrorist organizations, to arms dealers and human trafficking rings. Cybercrime is a great way to make money: low-risk and high-reward. As such, you don’t really know what causes that ransom is going to.
And worse, terrorists, for instance, don’t need that much money to carry out attacks. According to this NPR article, “take the attack on the London transportation system in 2005 that killed 57 people and injured hundreds. The U.N. estimated that cost a total of about $14,000.” Uber paid $100,000.
Paying ransom could encourage future attacks.
Put simply, if someone attacked your business and you paid the ransom, why wouldn’t other groups try to target your business? It’s easy money.
In conclusion…
Like vaccines, we need herd immunity to help prevent cyber attacks involving ransom. First, we need to make sure we’re protected. I know, easier said than done, but we have to start somewhere, right? Just like businesses are preparing for fires and floods, they should be preparing for data breaches and cyber attacks.
Second, all of us need to stand up to cybercrime and refuse to pay ransom, or this problem won’t go away any time soon. Fortunately, businesses now have plenty of reasons not to pay, thanks to this blog post. You’re welcome, society.

