Sharing, Compared Part 4: Where Do We Go From Here?
Quantitative and qualitative insights inform our roadmap and best practices to achieve success in CTI networking.

Background
This is the final installment in a multi-part series based on the CTI Networking Report 2024, the sequel to my inaugural study from 2022. Check out Part 1 for more context around this research.
Part 4 covers a roadmap for success, including real feedback of success and advice from respondents. Based on trends in qualitative and quantitative insights, we aggregate our findings in a guide that introduces how to engage in more intentional, inclusive, and strategic CTI networking.
Overview
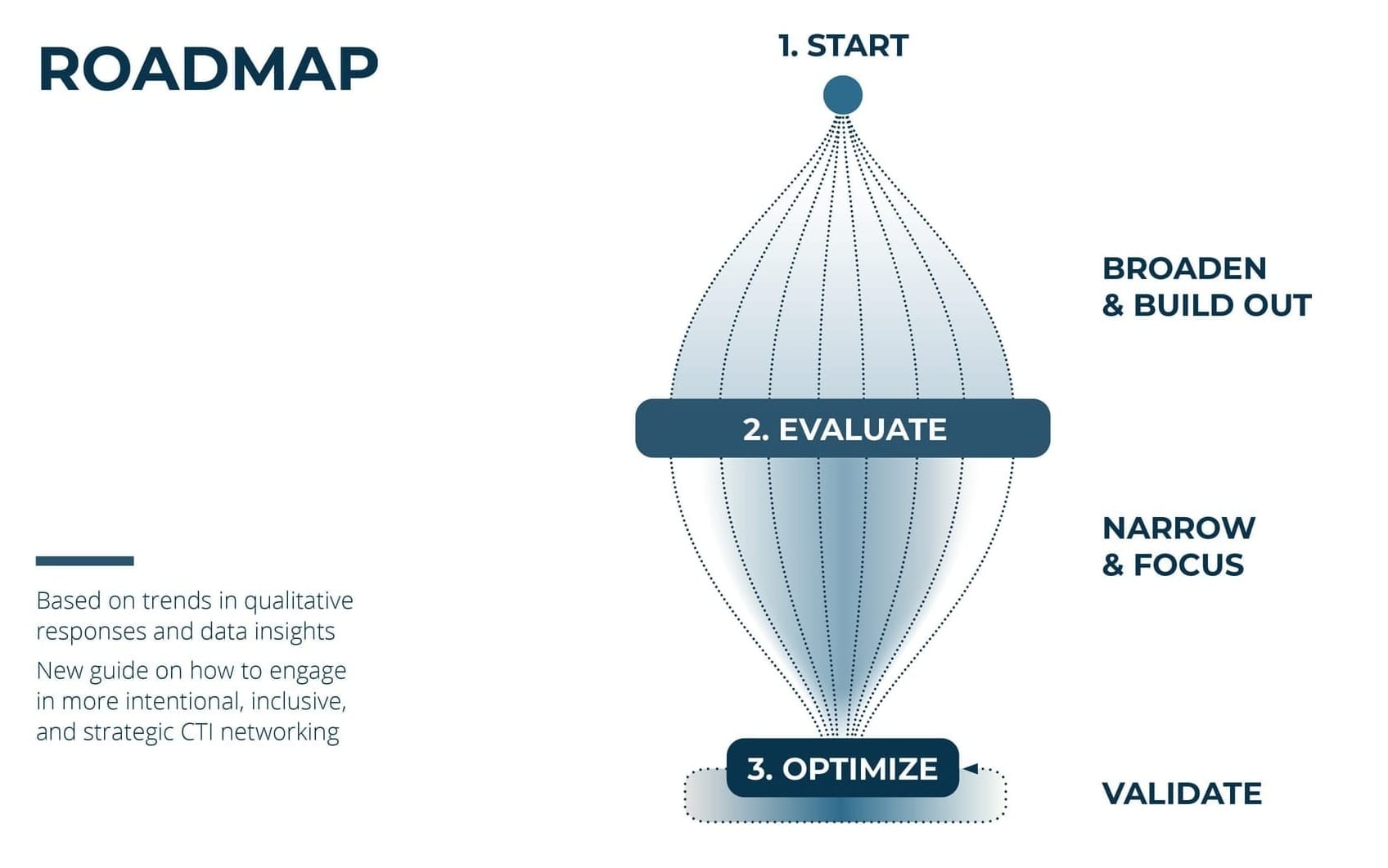
Start: Broaden and Build Out
Everyone starts somewhere.
With your unique requirements, security program needs, and capabilities (and limitations) in mind, try out a diversity of methods that are already in your orbit. Build up a foundation from your existing network, organizational opportunities, reputation, and skillset.
Evaluate: Narrow and Focus
After obtaining some successes and exposure to varied CTI networking opportunities, it’s time to hone in on what provides outsized value.
Examine which investments of time, energy, and budget yield outsized results. Prioritize and commit to those top three activities while maintaining limited capacity for new opportunities. Eliminate, scale back, or delegate activities that are not providing sufficient value.
Optimize: Validate
As with all things security, the process is continuous and iterative.
Periodically assess the efficacy of your efforts, attribute CTI networking in deliverables, and adapt as needs change. Validate by understanding where and how you can demonstrate results tied to CTI networking activities – both for yourself and to your organization. Doing so provides visibility into the often overlooked value of CTI networking and encourages buy-in from stakeholders for future efforts.
Start
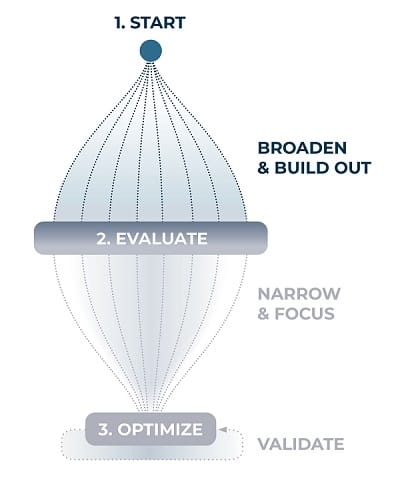
There is no one-sized-fits-all path. Lower your barrier by starting with your existing circle: set up 1:1s with current or former teammates, tap into vendor relationships, and or nurture connections from events (e.g. BSides). Follow researchers publishing interesting topics on social media and provide feedback. Define what would benefit your security program, then see where your organization is active (e.g. ISAC, ERGs).
Start at 1 hour/week with a patient, experimental mindset. Initiate chats around focus areas with peers and mentors, try out a new meetup, guest-publish on a blog, or contribute to a new group. Ask thoughtful questions if you feel like a newbie, curate interesting content, and establish credibility with your unique perspective. Increase hours spent only where you see results.
"Do not be afraid to try a new event that no one knows about, they can be smaller and easier to meet people”
"Ask questions! Contributing to a discussion doesn’t have to mean sharing information, it could be asking clarifying questions or encouraging others to elaborate...”
"Be skeptical. Be curious. Ask questions and do your own research to validate. Expect to be a lone wolf but if you find a pack, ensure you bring in others to grow the pack in a positive manner.”
"Thinking outside of the box; read, read, read, practice curating deliverables; networking!”
"Most importantly, don’t be a d***... with a relatively small community, we’re all Kevin Bacon degrees away...”
Evaluate
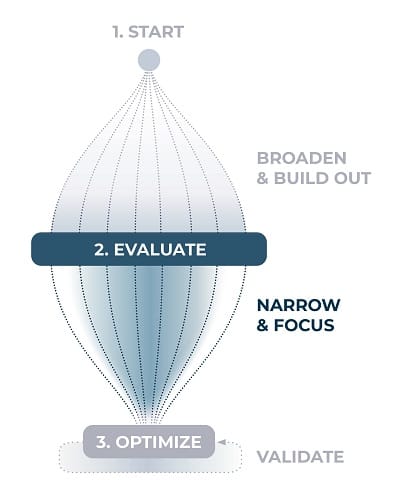
After some opportunities and exposure, you may feel you’re being stretched too thin. It’s time to hone in on what provides real value.
Think critically and commit to around three core channels that show serious promise or have proven results. Now that you’ve seen what works and what doesn’t, be selective and scale back time evaluating new opportunities. Consider structuring and scheduling your own 1:1’s or breakouts if you’ve found key peers from larger methods. Where possible, pass on introductions, embrace mentorship, and share invites to qualified peers. Don’t be afraid to (politely) bow out of commitments that lack ROI – the key here is quality, not quantity.
"Shortlist a few [methods] like a closed group or a 1-1 contact and stick to it... if focusing on more sources, try to create a workflow that make it easy to go through all the information”
"Focus on what you’re good at, share that information with partners who share back...limit the effort you exert with those who betray trust, only consume, or share [low-value] things.”
"I have gotten much more value out of quiet, TLP-Red high trust groups. [I]nformation shared in these groups is significantly better, they are smaller so you can get to know individuals, and there is a standing expectation that the information can be properly protected.”
"[I]nvest in low number of high value networking opportunities and try to build and contribute to long-lasting relationships, rather than trying to be all over the place with everyone since that is much more time consuming and the ROI is usually bad."
"Optimize and schedule your study... Don’t allow the sheer volume of threats and vulnerabilities to take over your life, force the company to set realistic guidelines and when you clock out, that means you’re OFF WORK, not studying threat feeds and IOC’s until 2am... Create a good working strategy and stick to it when threats arrive, seeking help through your delegates when you need new ideas, as you continue to isolate and limit the other areas that you can still contain. Above all, stay on top of emerging threats and meet weekly with your counterparts...”
Optimize
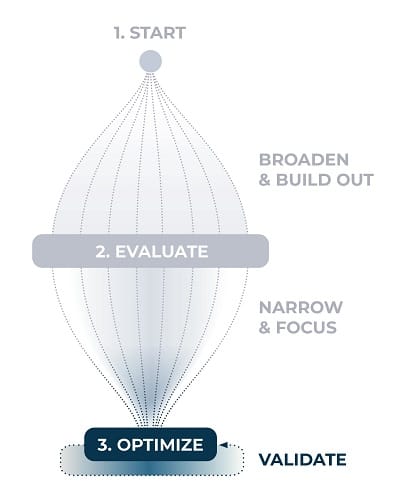
The process to maximize results with CTI networking is an iterative and continuous cycle. Building workflows, attributions, and measurements that truthfully recognize time and effort spent not only helps validate where and why you invest to yourself, but also to your team... and skeptical stakeholders.
Data showed an increase in transparency to leadership, but that is merely the first step to more meaningful change. To be viewed as more than a “liability” and receive the buy-in to even begin considering approvals, there must be significant and demonstrated business benefits (i.e. the risks must be understood and accepted). Additionally, as roles, companies, and the threat landscape inevitably change, you must also be able to understand and align those to your methods and sources. As always, it’s never “set it and forget it.”
"Focus on areas that provide a measurable return and tout those successes internally. Managing up and illustrating the value of spending time and resources in this area is the best way to get buy-in from leadership.”
"[N]etworking helped confirm or validate sources, processes, or information. A couple of times, we had just-in-time warnings or information that helped us prepare for something bad.”
"Private intelligence between trusted groups is...the most valuable data for me. In many cases during investigation it is possible to correlate data with other researchers... confirming or completing analysis, or getting additional data to pivot.”
"CTI networking on social media has revealed a previously unknown malware communicating with a C2 node in a victim environment, and I was able to use that information to guide the response.”
"Most of what I know started with a discussion with others.”
Stories of Success
For ideas and inspiration, we compiled some interesting stories from respondents. Quotes originate from the open-ended survey prompt: “Describe a past experience where CTI networking yielded interesting results”
Timely Action
"A partner provided insight into a current investigation based on the telemetry they had visibility to. The telemetry allowed us to better respond to the event and remediate the adversary in-house vs outsourcing... Potentially saving the organization $100ks in fees and lost productivity.”
"CTI networking has allowed the team to respond to active attacks attempting to leverage a 0 day vulnerability within our environment.”
"A phishing wave hit a peer company, they posted their detection rule to a peer-to-peer sharing group, we implemented it and were able to detect the campaign when it hit us a few days later.”
"Due to CTI networking and building trust, we were tipped off that a third-party vendor... had been compromised and a connection into our network was also compromised. We were able to get ahead of the threat... due to the relationship I had built.”
"I was notified on a discord trust group by another CTI professional of a post on a forum about databases of a major [organization] being sold... 1. It was early in the morning when the post had been released 2. It was the weekend 3. I was away from my laptop as I was about to go to conference. By notifying me... I was able to pass on the intelligence to my higher ups which resulted in the [organization] being alerted in a matter of hours about the post. The [organization] and other government officials hadn’t heard anything about the post and were able to investigate."
"Sharing partnerships have led to tips that prevented and pre-empted breaches.”
Visibility & Context
"Sharing of indicators in a peer group immediately identified the threat actor based on high confidence information from a member of the group.”
"Investigating a TA in order to make attribution. C2 was traced across multiple countries by other [government organization] in the working group. At the end we were able to find out the entire infrastructure across [continent].”
"A colleague at another organization shared some infrastructure I used...to develop a detection that the colleague plug[ged] into their defensive tools to help protect their organization long term from a particular actor. I was able to... find additional clusters of adversary activity including malware and work collaboratively across industries to contribute to an indictment.”
"Trusted source confirmed activity on adversary network and infrastructure using scanning and assessment tools not available at my company or not readily available to me.”
CTI Program Development
"Took my team to a local CTI conference, where we listened to several talks around new methods of intelligence gathering and dissemination. We spoke to the presenters at the conference to share our perspective. Then the team was able to incorporate what we learned into new processes for identifying novel threat actor activity in our client environments.”
"Information from a peer group of cybersecurity professionals... resulted in improvements to framework used for prioritization of vulnerability management for enterprise customers with OT, as campaign and diamond model data was shared for attackers targeting the same industry vertical and technologies.”
Trust & Management Buy-in
"While investigating a persistent phishing campaign, CTI networking helped us find vulnerabilities in a threat actors phishing kit which we used to our benefit. Participants ranged from interns to team managers. This helped gain further trust from senior management for CTI networking.”
"CTI Networking has been able to contribute to high visibility situations such as MOVEit Exploitation, 3CX compromise. [H]aving established groups... provided timely ability to look in our environment before it came down from Leadership for our team to look into it. It is better to have the answers before they even ask.”
Conclusion
In its current state, CTI networking is demanding, messy, and heavily dependent on individual efforts. Based on respondent insights, there truly is no secret sauce or linear recipe for perfection. Our roadmap is a reminder of fundamental best practices: start with a broad exploration of available methods and consistent investment over time; evaluate for efficacy; and finally, optimize based on demonstrated results. By embracing a diversity in methods and remaining intentional on what is delivering value, individuals and organizations can align effort to requirement, contribute critical insights within peer groups, and go beyond simple detection to collaborating on significant takedowns and indictments. The anecdotes shared from real-world experiences underscore the tangible benefits of CTI networking, from corroborating threat activity to achieving significant cost savings.

