What is Threat Intelligence?

A quick Google search suggests that a consensus has not quite been reached on defining the term “cyber threat intelligence.” There are some blog posts (yep, this one too) and even white papers attempting to assign some specifics or even trying to define threat intelligence by defining what it isn’t, and I’m happy to tell you that now I’m here to add to the confusion. So, let’s give it a shot and see how far we get.
Network-based
Going to start with an example. Let’s say I work at some company’s security team and an employee forwarded the spam email below.

This email appears a little suspicious and, judging by the links, probably leads to malware. Link analysis here.
After requesting some info from Pulsedive or a similar service, I get a full URL, domain, and IP address that I can use to help protect my employees. If I see the URL in my employer’s network logs, then I know that an employee clicked on a potentially malicious link and I can either block it or trigger an alert and have my team respond accordingly. If the employee is able to reach the malicious URL after clicking, it might be an indication that the employee’s machine is then compromised, so the URL becomes what’s known as an indicator of compromise (IOC). The same logic applies for the related domains and IP addresses; if the employee communicates with them, it might spell out compromise.
That all brings us to the first point I’d like to make:
Threat intelligence can be used to detect and alert on cyber threats.
Now, being the good Samaritan that I am, I decide to publish lists of these URLs so that other companies can use them, and in doing so, I’ve just published a threat intelligence feed. In the wild, these come in many different formats: JSON, CSV, XML, STIX, etc. Below is an example of the feed from OpenPhish.
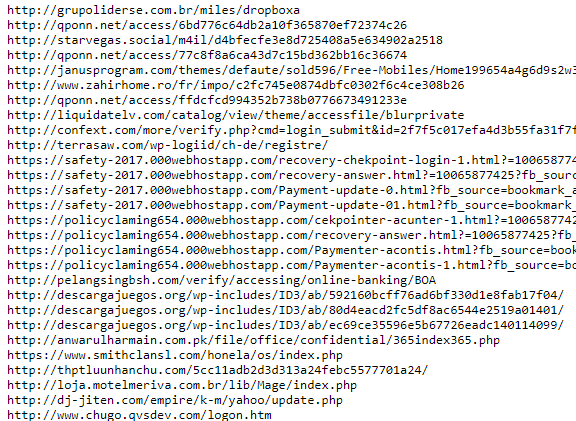
Network-based threat intelligence is probably the most common flavor of threat intelligence because while many companies might not have visibility into processes and files on their employees’ machines, they likely have network visibility at the proxy or firewall, so more companies can both generate and make use of network-based intel.
Host-based
Another similar example, an employee forwards me a different spam email but instead of links, it contains an attachment, “ovvbdu.zip.” Presumably, the attacker wanted to be found out with a clever name like ovvbdu, but that’s besides the point.
I submit the suspicious sample to Payload Security’s free Hybrid Analysis sandbox and get a ton of details and a threat score of 100/100, meaning the file is most likely malicious.

Now that I have a confirmation that the suspicious file is probably malware, I can use information like the SHA256 hash or the file name “scan_doc.exe” to uniquely identify and block the file when it’s been opened on an employee’s machine.
However, because the file name can easily be changed and the SHA256 hash will change when the malware is updated and re-released by the attacker, I can try to use some more persistent information like processes the malware starts, strings found in the file, other files downloaded, network-based information, behavior-based information, or a combination of all of the above.
Information like the SHA256 hash, file name, process names, and related files are all indicators of compromise (IOCs), and are generally considered host-based threat intelligence because they are destined for the actual host, the employee’s machine, rather than used for communication over the network. You certainly might see some of the information in network traffic such as when the employee downloads the malware, but the file’s destination is still the employee’s machine. Additionally, the employee could take their laptop home, get infected with malware, and return to work compromised, so the initial download wouldn’t show up in network traffic.
Behavior-based
US-CERT just published an alert for “malicious cyber activity by the North Korean government,” affectionately referred to by the US Government as HIDDEN COBRA. The alert describes activity attributed to the Volgmer Trojan and provides a list of IOCs as well as a Malware Analysis Report (MAR). Alerts and reports such as these often provide TTPs as well (Techniques, Tactics, Procedures), a term borrowed from terrorism studies. In the context of information security, TTPs refer to the behavioral patterns observed by malware, malicious actors, cybercriminal organizations, etc.
Some tools like intrusion detection systems (IDS) can use behavioral signatures to alert on potential intrusions or suspicious activity (similarly, intrusion prevention systems block activity that’s triggered by a signature).
If we take a look at a previous US-CERT alert describing the CrashOverride malware, we can find some behavioral information:
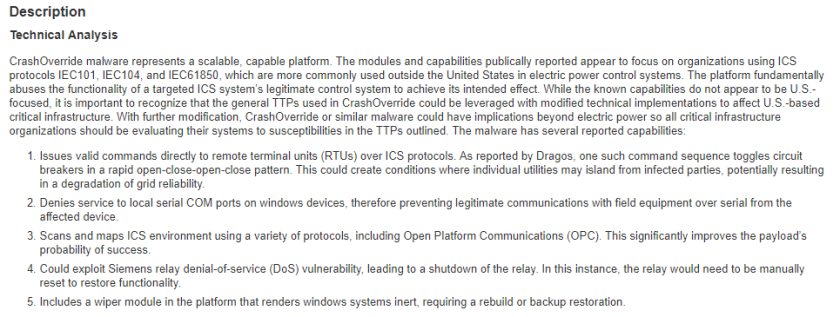
If I see behavior in my environment matching what’s outlined above, I can attribute the activity I see to the CrashOverride malware. This brings us to my last point:
Threat intelligence can be used identify a cyber threat.
So what is threat intelligence?
The moment we’ve all been waiting for:
Threat intelligence is network-, host-, or behavior-based information that can be used to detect, alert, or identify a cyber threat.
Eh? What do you guys think? Maybe it’s totally wrong but, either way let me know in the comments.

