2023 In Review
Here's our 2023 roundup of cyber threat intelligence news: key exploited vulnerabilities, ransomware, and Pulsedive updates over the last year.

Threat Recap
2023 was a challenging yet interesting year for defenders with several mass exploitation events that made headlines around the world. Apart from the exploitation of third party software to steal data or gain initial access into environments, ransomware remained a common threat for organizations worldwide. Here are some of the biggest threats from 2023:
Key Exploited Vulnerabilities
GoAnywhere
Cl0p started the year off by exploiting a vulnerability in the GoAnywhere MFT application (CVE-2023-0669). The vulnerability was first published on the 6th of February 2023. This was not the first time the group has exploited a file transfer service in an attempt to exfiltrate data, in 2020 and 2021, the group targeted Accellion File Transfer Appliance (FTA) in a similar zero-day driven exploitation campaign (CISA). GoAnywhere MFT is a managed file transfer, similar to MOVEit, that facilitates the secure transfer of files between entities. Cl0p claimed that they have used the vulnerability to steal data from 130 companies (Bleeping Computer). Victims of Cl0p’s GoAnywhere campaign included the City of Toronto, Hitachi Energy and Community Health Systems. Community Health Systems disclosed that approximately one million individuals may have been impacted when their GoAnywhere MFT instance was exploited (SEC).
The vulnerability was a remote code execution vulnerability that was the result of improper sanitization of serialized data. This vulnerability was exploited to create users within the file transfer application.
MOVEit
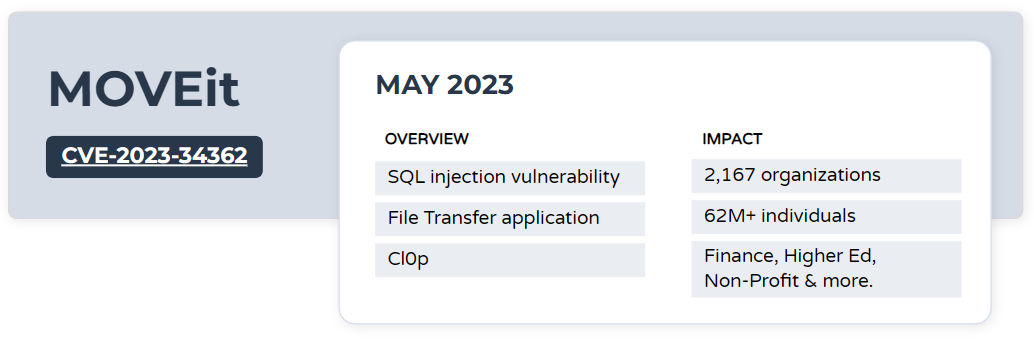
On May 31, 2023, Progress Software, the developers of MOVEit, reported a vulnerability (CVE-2023-34362) that allows for unauthorized access into the environment. CVE-2023-34362 is a SQL injection vulnerability that allows an unauthenticated attack access to the SFTP’s database. Huntress reported that exploitation of the vulnerability could lead to the deployment of ransomware or code execution (Huntress).
Exploitation of this vulnerability has been attributed to the threat group Cl0p. Following their exploitation of GoAnywhere MFT servers at the beginning of the year, the group was able to rapidly target MOVEit servers after getting their hands on an exploit. Emisoft states that as of October 2, 2023 2,167 organizations and over 62 million users have been impacted by MOVEit (Wired). Most organizations impacted were using the File Transfer application to share data with other entities. Some victims include the likes of Austrian Financial Market Authority, BORN Ontario and the University of Los Angeles, California. Additional details about the exploitation of MOVEit can be found on the Curated Intel GitHub.
3CX
In March of this year, 3CX updates (CVE-2023-29059) were observed to be spreading malware within their installation packages. 3CX is a phone application that allows users to send messages or place calls. The packages were available for download from 3CX’s website. The method of intrusion into the 3CX environment is of particular interest since it was a supply chain compromise upstream. Threat actors gained access to a 3CX endpoint through a compromised financial software from Trading Technologies (Mandiant). The trojanized application was installed on a 3CX employee’s device and allowed the threat actors to navigate through the environment and reach the software development environment. The initial compromise was in Trading Technologies’ X_Trader application that was used by financial services firms to conduct trading activity (Wired). This application was no longer supported in 2020. This attack has been attributed to a North Korean threat actor that Mandiant has named UNC4736.
Barracuda Email Security Gateway (CVE-2023-2868)
On May 30th 2023, Barracuda disclosed a remote command injection vulnerability, CVE-2023-2868. This vulnerability appears to have been exploited by threat actors as early as October 2022 and is due to how the initial screening of incoming email attachments takes place (Rapid7). Barracuda requested that customers that were using devices that were running impacted versions completely replace their devices even if the devices have been patched. It is not often where a vendor tells its customers to replace devices even if patches have been applied and where a vendor offers to replace appliances at no cost (Barracuda).
Based on reports from Mandiant, this vulnerability was exploited by UNC4841 (a suspected Chinese actor). Exploitation started through a TAR file attachment which was used to execute a payload for a reverse shell (Mandiant). In some observed intrusions the reverse shell contains base64 encoded commands that were used to establish connections to a remote IP address. Once the threat actor got access to an environment, they leverage applications including wget to download additional tools and payloads.
Looking Ahead: Vulnerability & Exploitation Predictions in 2024
Looking to 2024 and beyond, we expect that attacks against public facing infrastructure and the rapid exploitation of third party applications will only continue to increase. Exploiting internet-facing assets was a common theme across ransomware groups with the operators of Akira targeting Cisco or Fortinet VPN endpoints while LockBit operators focused on Citrix NetScaler ADC (Citrix Bleed) in 2023. We predict this trend to continue.
Ransomware
Similar to previous years, ransomware continues to be a major threat for organizations all around the world. In 2023, prominent ransomware groups including LockBit and Cl0p continued to target organizations. Several groups took advantage of vulnerabilities on internet facing assets as evidenced by some of the key exploited vulnerabilities above and the players behind them. Apart from ransomware groups that have been active for a few years, this year we observed the emergence of new or rebranded groups that were particularly aggressive.
Emerging Groups & the Conti Leaks Legacy
Akira
A few of the newer ransomware groups on the block appear to have similarities to Conti. After the Conti leaks (internal Jabber conversation and source code from the ransomware group were leaked by an Ukrainian security researcher when Conti expressed support for the Russian Government during the early stages of the Russia-Ukraine war last year - Trellix), it was suspected that more groups would appear using Conti code. This appears to have happened but it also makes attributing groups to Conti developers and those who are simply using the code more difficult.
One of the groups with links to Conti is Akira. First observed in early 2023, with a retro looking data leak site, the group was particularly active in its first few months of operation and targeting organizations across various industries.
In some confirmed Akira instructions, the threat actor was observed exploiting vulnerabilities in internet-facing assets including CVE-2023-20269, a vulnerability within Cisco’s Adaptive Security Appliances (ASA) and Firepower Threat Defense. Following initial access, attackers leveraged tools including Mimikatz, PCHunter64 to further achieve their objectives. Data exfiltration was assisted through legitimate tools including RClone, WinSCP and FileZilla (Trellix).
Analysis of Akira’s code base by Arctic Wolf revealed similarities to Conti including which file types and directories are excluded from the encryption routines. Additionally, their analysis of blockchain transactions related to Akira revealed several wallets that overlapped with those used by Conti (Arctic Wolf).
Royal Ransomware
Another group that garnered some headlines in 2023 was Royal Ransomware. The group was first observed in 2022. Based on the tactics, techniques and procedures (TTPs) used in Royal intrusions, some researchers suspect that the group may consist of former Conti members that compromise Conti Team One.
An article from The Record Media on November 13th 2023, states that the FBI and CISA suspect that Royal ransomware group may rebrand as BlackSuit (The Record). The Department of Health & Human Services released a report on BlackSuit where several parallels between them, Royal and Conti were made.
Predictions in 2024
For 2024 and beyond, we expect that ransomware will continue to be one of the more prominent threats organizations will face. We’ve seen this year that ransomware groups are particularly adept at leveraging vulnerabilities for mass exploitation and have seen some groups drop the encryption of files from their operations and simply threaten to leak data to coerce victims into paying ransoms. The use of remote management and monitoring (RMM) tools is a technique that we expect to continue to see from ransomware authors. Using off-the-shelf RMM tools has allowed threat groups to establish a connection mechanism into corporate networks and fly under the radar since these tools are commonly used by IT personnel as well. A good practice is to regularly audit the use of RMM tools within environments and restrict which users can install additional applications.
Inside Look: Pulsedive
2023 was a busy year at Pulsedive. There have been a number of noteworthy initiatives and developments that have taken place. These items range from new features for the platform, to research blogs and presentations at key conferences throughout the year.
Platform Updates
The Pulsedive platform received two key updates this year - versions 6.1 and 6.2. Each new version contained enhancements focused on improving the platform and a better user experience for free, paid, and enterprise users.
Version 6.1 introduced indicator screenshots on threat pages. This feature groups indicators together for pivoting based on similar web content. Examples of shared indicator screenshots are available in the Screenshots section of the Phishing threat page. Mystic Stealer is another threat where the shared indicator screenshots can be used to group IoCs together.
Version 6.2 introduced several enhancements to threat pages. From version 6.2 onwards, threat pages will now have fields for suspected attribution, targeted industries and tactics being displayed right at the top of the page. Suspected attribution is primarily being used to indicate where researchers believe the threat groups originate. When adding a suspected attribution, users can leverage 2-letter country codes (Alpha-2) used by IBAN.
Targeted industries is a field based on the STIX 2.1 Industry Sector Vocabulary with some minor tweaks for ease of use and additional industries. One of the tags that was not present in STIX but is used within Pulsedive is Home Users. This industry tag was created to show threats that do not necessarily go after a particular organization but rather end users. Threats that target a particular industry can be searched for using the Explore page and the query industry=<industry type>. The screenshot below shows threats that have targeted financial services organizations.
Threat Research
This year, Pulsedive went through the process of hiring a threat researcher to conduct research and update data sets available to our user community. The role received 205 applications, narrowed down to 18 interviews focused on past experience and applied experience through the review of the threat bulletin. Our team validated the value of the live exercise, and recommended this to other hiring teams, as it offered key insights into how the candidates review materials and pivot to other sources to collect additional information.
Once onboarded, the researcher worked with the team to identify topics of interest and worked on creating content surrounding them. To date, we have published four research blogs about different threats:
- Akira Ransomware
- Identifying Mystic Stealer Control Panels
- Analyzing Agniane Stealer
- Analyzing DarkGate Loaders
Our threat research blogs focus on the analysis of new or emerging threats and details about TTPs to inform security defenders on trends and relevant actions to take. In addition, we also embed helpful tips and tricks to support newer security practitioners and aid other analysts during their analysis. For example, in Analyzing Agniane Stealer, the UnProtect Project was used as a reference for malware evasion techniques.
Presentations
We met so many familiar and new faces at conferences throughout the year. If you missed it, here were some of our key talks, including links to learn more:
PancakesCon, March 2023
Collaboration Required: Threat Intelligence Sharing & Coop Board Games
Abstract: Sorry to say, but we’re all in this together. Whether it’s cybersecurity threat intelligence (CTI) or surviving invader ravages, cooperation is not an option. In this talk, we discuss the basics of CTI and how to build up bidirectional sharing for improved outcomes, as well as a handful of my favorite coop board games - and why they rose to the top.
Chryssalid aliens! APTs! The Habsburg Monarchy! Virulent strains! All of these threats and more. You’ll leave prepared to gather peers around and stave off attacks, both in cyberspace and on the tabletop.

SECON, June 2023
Demystifying Cyber Threat Intelligence
Abstract: Cyber threat intelligence (CTI) is a critical and evolving space in security dedicated to collecting, analyzing, and operationalizing knowledge around cyber attacks and threat actors. This talk delves into the who, how, what - and most importantly - the why, of CTI. Learn the core competencies that make a CTI analyst shine, the cycles and frameworks structuring CTI programs, and the tools that elevate output.
We also had the pleasure of sponsoring a handful of student tickets for aspiring cyber talent from 4 different universities in the NJ area!
FIRST CTI Conference, November 2023
How to Align CTI and Risk Management: Successfully Connecting Two Related Practices (Workshop)
Workshop Abstract: Cyber Threat Intelligence (CTI) and Risk Management are two traditionally separate areas yet over the past few years, there has been a growing recognition of benefits from coordinating workflows and sharing knowledge between CTI and Risk Management. Transcending cyber risk-intelligence silos creates synchronized cyber defense organizations, enabling larger strategic initiatives. There is just one thing, aligning the two is not always an easy task.
This workshop demystifies misconceptions about each team, identifying elements unique to each, highlighting cultural differences that may lead to potential friction points that would inhibit collaboration. We will jointly identify collaboration opportunities unique to participants’ organizational culture and develop key building blocks across products and processes to improve team collaboration, organizational effectiveness, and resilience.
After the workshop, participants will be equipped to have open conversations with their partner team(s) about how to improve collaboration between the functions. Participants will have developed a baseline understanding of the unique terminology each uses and frame of reference that aligns with role and responsibility within the organization to assist in these discussions. Similarly, participants will have created products or processes in which they can use to jumpstart the conversation about creating collaborative workflows.
A Sneak Peek at Pulsedive in 2024
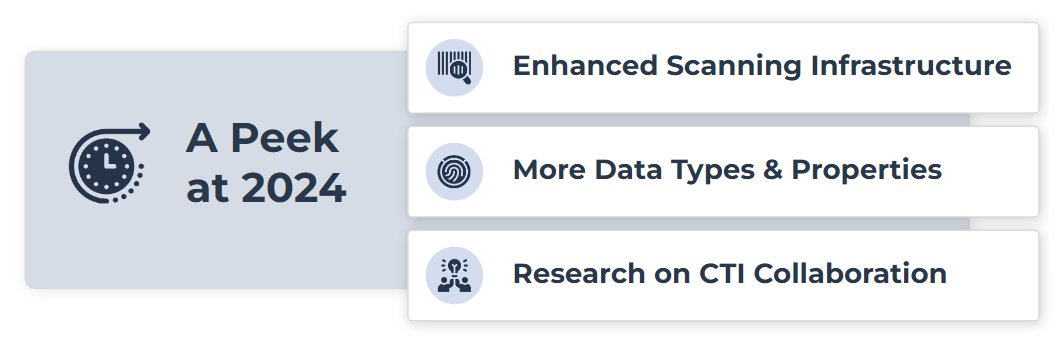
While 2023 was a big year for us, we are looking forward to sharing some details about what our users can anticipate in 2024. Our team has been working hard on Pulsedive’s next generation scanning infrastructure, expected mid-2024. While the full capabilities have not been announced, we can share a tiny sneak peek: users can expect RDAP data and JARM hashes will be stored as searchable properties and integrated into on-demand scans.
In January 2024, Grace will publish her latest report and present findings from the CTI Networking Survey. This research analyzes how practitioners are effectively collaborating - and shared challenges faced by teams around the world. Make sure to register for the 2024 SANS CTI Summit to catch the presentation live.
More to come - stay tuned for updates!
References
https://www.cisa.gov/news-events/cybersecurity-advisories/aa23-158a
https://chsnet.gcs-web.com/node/22076/html
https://www.huntress.com/blog/moveit-transfer-critical-vulnerability-rapid-response
https://www.wired.com/story/moveit-breach-victims/
https://github.com/curated-intel/MOVEit-Transfer
https://www.mandiant.com/resources/blog/3cx-software-supply-chain-compromise
https://www.wired.com/story/3cx-supply-chain-attack-times-two/
https://www.barracuda.com/company/legal/esg-vulnerability
https://www.mandiant.com/resources/blog/barracuda-esg-exploited-globally
https://www.trellix.com/about/newsroom/stories/research/akira-ransomware/
https://blog.pulsedive.com/akira-ransomware/
https://arcticwolf.com/resources/blog/conti-and-akira-chained-together/
https://twitter.com/VK_Intel/status/1557003350541242369
https://therecord.media/cisa-fbi-warn-royal-ransomware-gang-rebrands-blacksuit
https://www.hhs.gov/sites/default/files/blacksuit-ransomware-analyst-note-tlpclear.pdf





