Collection through Correlation: Operationalizing IP and Domain Indicators of Compromise
IP addresses and domains aren’t just for blocklists; when analyzed with the right tools, they can be operationalized to enrich alerts, support threat hunting, and uncover risk.

In the field of cyber threat intelligence (CTI), IP addresses and domain names are commonly shared indicators of compromise. They are commonly used solely to create blocklists on tools such as firewalls and other networking devices. Blocking these atomic indicators of compromise is a viable solution when consuming threat intelligence feeds, but they can also be used to enrich alerts, provide context, and expand detection logic. This blog outlines how IP addresses and domains can provide additional value within the disciplines of threat intelligence, detection engineering, and threat hunting. Moreover, this blog will share details and guidance on how to conduct IP and domain analysis to draw conclusions, as well as showcase examples of data processing from Pulsedive and popular analyst tools.
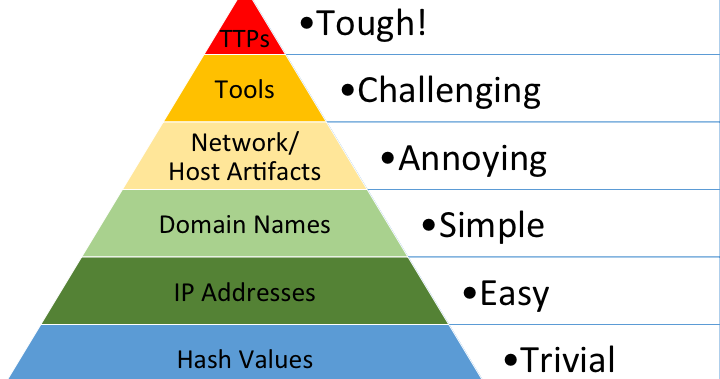
The Pyramid of Pain
Any discussion about value within threat intelligence will likely touch upon the Pyramid of Pain. The Pyramid of Pain, coined by David Bianco, is a model used in CTI to illustrate the difficulty experienced by adversaries and threat actors when defenders detect and respond to different types of indicators during an attack. Moving up the pyramid from hash values to TTPs is correlated with the increased "pain" inflicted on the adversary, becoming more challenging to replace or adapt. IP addresses and domain names make up two of the lower tiers in the pyramid and may not cause as much pain to threat actors as detecting tools or TTPs. This is because IP addresses and domains can be ephemeral. Threat actors can quickly rotate through IP addresses during campaigns, negating the impact of blocking individual addresses. Similarly, domain names can be registered in bulk; with various registrars, it is easy for a threat actor to spin up network infrastructure fairly quickly.
Since these indicator types are ephemeral, even adding these indicators to blocklists may provide limited value. Blocking provides value when a threat actor consistently uses the same IP address or domain name across a campaign. Once they rotate to a new IP address or domain, the blocked indicators cease to provide value outside of retroactive investigations. In the short term, blocking IP addresses and domain names can yield timely results and identify malicious or suspicious activity. However, these lists need to be actively maintained and regularly purged to remove indicators that are no longer active or have been removed by vendors.
- The confidence level associated with that IOC
- When was the indicator last seen?
- Is this indicator associated with other threats?
- Storage limitation on tools (blocklists have a finite size)
Uses of IPs and Domains
Providing Context During Investigations
Security analysts often spend time either manually enriching data to gain additional information about events or leveraging automated lookups to provide this context. Enriching IP addresses can include leveraging IP geolocation data, reputation data, and provider data. Geolocation data can give an approximation of the user’s location when a specific activity is performed and can be used to identify compromised accounts when multiple login sessions or actions are performed by the same user, but from physical locations that are not possible. Reputation data is another valuable enrichment during investigations, as it sheds light on the IP addresses and the other activities associated with them. Common reputation clues include if it has been reported by other users for exploitation or scanning activity, or if it belongs to a VPN provider.
Examples of how Pulsedive users leverage this enrichment data:
- Manual Approach: An analyst visits Pulsedive, performs a scan, and collects the relevant information to help during an investigation.
- Hybrid/Automated Approach: A SIEM/SOAR solution integrates with Pulsedive and is configured to retrieve data about IP addresses and domains. An alert may be triggered based on suspicious activity, where an analyst then uses this data to investigate an alert and make a determination about this activity.
Atomic indicators can also be used to hunt for malicious activity in an environment. Simpler to conduct than behavioral threat hunting, indicator-based hunting focuses on the presence of known malicious indicators of compromise (IOCs) to identify malicious activity in historical network logs. Security tools can be used to search for the presence of IOCs that security researchers have shared throughout an environment. Hits on these IOCs may lead to the discovery of previously undetected intrusions.
Research
Indicators can be tied together to identify particular malware families and reveal commonalities that make it easier to identify other artifacts associated with that threat. For example, Pulsedive threat research used IP addresses, domains, and content served on web pages to track and identify additional Mystic Stealer control panels back in July 2023.
When we encountered research from other vendors regarding Mystic Stealer, we utilized the IOCs to identify commonalities between them before attempting to identify additional domains to track. Our approach involved looking at the following items for each identified IOC:
Based on information shared by security researchers, we observed that the HTML title for the control panel was "Mystic Stealer - Login". We used this information to pivot to tools such as FOFA, Shodan, and Binary Edge to identify additional IP addresses and domains associated with Mystic Stealer Control Panels.
IP Analysis Tools
Depending on the use case and the information we want to obtain, many tools can provide information about IP addresses. This information can include:
- IP Reputation
- IP Geolocation
- Is it a Cloud/CDN IP?
- Is it a VPN, Tor node, or proxy?
- IP WHOIS
- ASN
- Open Ports & Services Running
During investigations, some of the first items analysts commonly check for are the reputation and geolocation of an IP address. IP reputation can show if an IP address has been observed by others performing scans or attempting to exploit vulnerabilities.
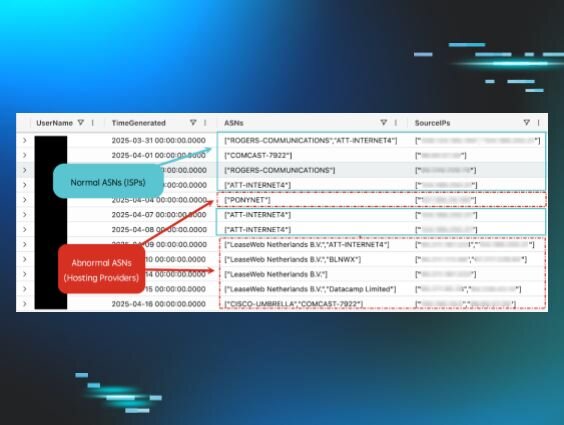
Tools such as Spur or IP Quality Score can be used to detect VPN or Proxy usage. This information is valuable during investigations, as it can explain differences in geolocation and be used to track activity against specific devices or sessions. Moreover, the use of specific VPN providers or proxies can be used to cluster activity to different threat groups. For example, security researchers have identified that Famous Chollima frequently uses Astrill VPN during intrusions.
Other Analysis Tools
Data collected about domains can also be used to cluster activity back to a particular threat or actor. In some cases, this will be as simple as examining X.509 certificates to identify common names. In contrast, in other cases, it will require a wealth of data from both the domain and the IP addresses to recognize patterns.
Some of the information that can be collected about domains includes:
- WHOIS/RDAP Information
- Date registered
- Registrar Information
- Content hosted
- Certificate Details
- Favicons
- Meta Tags
X.509 certificate data contains a wealth of information that can be used to identify additional IOCs.
Taking an entry for DCRat from the SSL Blacklist provides us with a SHA1 fingerprint, Subject Name, and Issuer Name. Any of these can be used to search tools like Censys to identify additional IP addresses using the same certificate.
Searching Censys for the value DCRat in the subject common name yields 46 results. Drilling into the IP 203[.]104[.]42[.]92, the certificate details reveal that the subject common name is the same, but the issuer distinguished name is different.
Unique values within certificate data can also be incorporated into detections. A blog by Corelight contains network signatures that focus on the content of the TLS certificate.
Conclusion
The ephemeral nature of IP addresses and domains means that they may not seem as valuable within threat intelligence and detection engineering as other artifacts. This is true to a certain extent, but analyzing IP addresses and domains can help researchers and analysts uncover additional detections useful in identifying additional IOCs or malicious activity.
Analysis of IP addresses and domain names can reveal patterns or unique identifiers, such as particular proxies being used to initiate connections. X.509 certificates contain specific values that allow security teams to detect additional suspicious or malicious data. Moreover, analysis can help cluster activity based on commonalities between artifacts to identify a particular threat or actor. The speed of sharing, ease of automation, and availability make these IOCs a component of a holistic threat intelligence program. When contextualized alongside other indicators higher up in the pyramid of pain, teams can gain valuable insights into threat actor behavior, which may lead to additional detection opportunities.
References