2024 In Review
A rewind of the year across the threat landscape and at Pulsedive.

This blog aims to highlight some of the major incidents and events in cyberspace in 2024. Looking back, it feels like 2024 flew by with a steady stream of issues constantly grabbing the attention of defenders (and the media). Apart from the continued targeting of public-facing sources such as firewalls and other networking appliances, this year will be remembered for law enforcement takedowns and the CrowdStrike outage.
Read on for a review of:
- Our predictions for 2024 from last year
- Key exploited vulnerabilities
- Top malware
- Outages
- Law enforcement actions
- Looking ahead to 2025
- Pulsedive rewind
Recap
Looking back at our predictions for the year
Vulnerability and Exploitation Predictions
In 2023, we predicted that exploitation attempts against public-facing infrastructure and the rapid exploitation of these appliances will continue to increase in 2024. Unfortunately, this prediction appeared to come true, with several vulnerabilities within public-facing applications being exploited for initial access into environments being observed throughout the year. This blog's Key Exploited Vulnerabilities section below discusses some notable exploited vulnerabilities.
Ransomware Predictions
We expected ransomware to continue being one of the more prominent threats organizations faced in 2024. This was observed as ransomware attacks continued to grab headlines as threat actors targeted organizations worldwide. We also observed several groups deploying ransomware at healthcare organizations. Defenders and law enforcement had some success against ransomware, with takedowns against LockBit.
Key Exploited Vulnerabilities
Cleo File Transfer Software
On December 3rd, 2024, Huntress released a blog outlining the exploitation of Cleo Harmony, Cleo VLTrader, and Cleo LexiCom software, which led to unauthenticated remote code execution. Organizations use these file transfer software programs to share files with other users. Initially released as CVE-2024-50623, it was quickly discovered that the patches for this vulnerability did not mitigate the risk, and patches for CVE-2024-55956 addressed the issues.
CVE-2024-55956 allowed an unauthenticated threat actor to import and execute bash or PowerShell commands using the Autorun directory. This vulnerability allowed the attacker to access external infrastructure to download files used in post-exploitation attempts.
BleepingComputer reported that the Cl0p ransomware group used this vulnerability to exfiltrate data from organizations.
Exploitation of Public Facing Infrastructure
Threat actors heavily targeted networking software and file transfer appliances throughout 2024. These software and appliances are public-facing and may offer access to corporate environments. Because they are more accessible, they remain high-priority targets, and we observed threat actors rapidly exploit these vulnerabilities once they are made available.
Some of the notable vulnerabilities in public-facing software observed this year included:
CVE-2024-3400 - PAN-OS: Arbitrary File Creation Leads to OS Command Injection Vulnerability in GlobalProtect
CVE-2024-3400 is an arbitrary file creation vulnerability in the Global Protect feature of PAN-OS. It can lead to OS command injection and has been used to exfiltrate data from the server or run commands. Palo Alto tracked the exploitation of this vulnerability as Operation MidnightEclipse.
CVE-2024-8190 - OS Command Injection in Ivanti CSA
CVE-2024-8190 is an OS command injection vulnerability in the Ivanti Cloud Services Application (CSA). For versions 4.6 Patch 518 and before, exploiting this vulnerability could allow an unauthenticated attacker to execute code remotely. CISA has added this vulnerability to its known exploited vulnerability catalog.
CVE-2024-47574 (FortiJump) - Authentication Bypass in FortiClientWindows
CVE-2024-47575, also called FortiJump, is an authentication bypass in Fortinet FortiClientWindows versions 7.4.0, 7.2.4 through 7.2.0, 7.0.12 through 7.0.0, and 6.4.10 through 6.4.0. This vulnerability allowed a threat actor-controlled FortiManager device to execute code against vulnerable FortiManager devices. Mandiant observed exploitation of the vulnerability as early as June 27, 2024.
XZ Utils Backdoor
One of the year's biggest stories, CVE-2024-3094, is a vulnerability that affected the xz compression libraries in Linux distributions. The affected versions (5.6.0 and 5.6.1) of the xz libraries contained malicious code that allowed unauthorized access.
xz is a data compression format within Linux distributions. It helps compress and decompress large files into smaller sizes. The multi-stage backdoor is used to extract a shared object liblzma_la-crc64.fast.o, which is added to the compilation of the liblzma. The shared object replaced a function name, and when any process loads liblzma, the malicious code interferes with the function resolution process. OpenSSH’s RSA_public_decrypt function uses the liblzma, and the malicious code could be used to extract a command from the authenticating client’s certificate and use it for remote code execution.
liblzma library could be used by sshd. Source: AkamaiMalware
This year, information stealers, like Agniane and Mystic Stealer, and other malware-as-a-service continued to be used against users and organizations. Information stealers served as the initial stages of intrusions, either collecting credentials or deploying other malware. Ransomware continued to be a major threat to organizations, with several groups targeting healthcare organizations and other critical industries.
Ransomware Targeting Healthcare
ALPHV targeted Change Healthcare, a revenue and payment management provider, in February 2024. 100+ million individuals had their data stolen in the attack, impacting the operations of healthcare organizations that used Change Healthcare. Change Healthcare appeared to pay a ransom of $22 million before ALPHV performed an exit scam, including deploying a fake law enforcement seizure banner on their data leak site.
Qilin targeted Synnovis with ransomware, which disrupted the operation of several NHS Trust locations in June 2024. For the NHS, Synnovis, a lab services provider, was hit with ransomware that disrupted their IT systems. The group was able to exfiltrate sensitive patient information, including names, dates of birth, NHS numbers, and test descriptions.
In May 2024, Ascension Health suffered a ransomware attack by Black Basta. The attack impacted hospital operations by taking Ascension’s MyChart, an electronic health record system, offline. While the service was down, healthcare professionals had to resort to manual documentation. Following an investigation, Ascension identified that 5.9 million individuals had their data stolen. The data exfiltrated during the attack included patient and employee names, as well as medical and payment information.
In addition to continuing ransomware attacks and identifying new malware types, malware authors continued experimenting with different methods of deploying their malware onto devices. One method that grew in popularity this year is ClickFix.
ClickFix
This social engineering tactic manipulates users into executing code on their devices. The user is presented with a document or a web page with a banner with instructions for the user to follow, similar to figures 6 - 8.
The banner will instruct the user to:
- Launch the run dialog
- Paste in content that is in their clipboard (an older version of ClickFix required the user to copy the malicious code, while newer versions automatically add it to the user’s clipboard)
- Run the command
CrowdStrike BSOD Outage
On July 19th, CrowdStrike pushed a detection update to its Falcon sensors. This update included a problematic configuration file that caused the Windows operating system to crash, causing users to observe the blue screen of death. Computers experiencing the blue screen of death caused this outage, which led to business disruptions as the impacted organization no longer had access to its devices.
Threat actors quickly took advantage of the situation by registering domains for phishing attempts. These phishing scams capitalized on the outage and operated by offering recovery software or processes in exchange for money. The goal was to get users to send the money or deploy malware.
threat=“Crowdstrike BSOD Impersonation”.To learn more about the outage, read the blog CrowdStrike BSOD Outage: What We Know.
Law Enforcement Action
Operation Cronus
In February 2024, law enforcement agencies disrupted LockBit operations through Operation Cronus. This multi-agency investigation resulted in the freezing of over 200 cryptocurrency accounts tied to LockBit and the UK’s National Crime Agency (NCA) taking over the group's infrastructure. The investigation also led to the publication of details about the group using the seized infrastructure.
Authorities also made decryption keys available, which helped victims of LockBit with recovery efforts. The decryption tool is available through NoMoreRansom.

In addition to the takedown efforts in February, the US Department of Justice announced charges against Rostislav Panev, a Russian and Israeli national, who was arrested in Israel on December 20, 2024. The DOJ press release indicated that Panev was responsible for developing the LockBit ransomware and maintaining technical infrastructure. The DOJ has also indicted Dmitry Yuryevich Khoroshev, who is thought to be LockBitSupp, the persona used by LockBit to communicate on forums such as XSS.IS.
While LockBit appeared to recover from Operation Cronus and was able to deploy ransomware at organizations throughout the year, the arrest of its developer may impact future operations. While the takedown of technical infrastructure benefits defenders and such law enforcement action should be applauded, arresting those behind these groups will significantly disrupt operations.

Looking Ahead
We expect 2025 to be similar to 2024 regarding the types of threats defenders will have to deal with. Threat actors will continue to target public-facing applications and servers, and prioritizing patching these applications will become increasingly important. However, solely relying on patch management will not be sufficient, and a layered defensive approach is required to mitigate risks. This includes host—and network-based monitoring to identify anomalous processes and the traffic related to these applications.
Remote management and monitoring (RMM) tools were heavily abused in 2024, continuing the trend from prior years. These tools allowed threat actors to access environments and establish persistence while blending in. The use of tools already present within a victim’s environment will continue, requiring defenders to track tool usage and deploy policies through device management solutions to restrict access to authorized applications.
Finally, generative AI (Gen AI) is another avenue we expect threat actors to abuse heavily in 2025. We anticipate threat actors using Gen AI to create more effective social engineering lures and aid in developing malicious tools.
Pulsedive Rewind
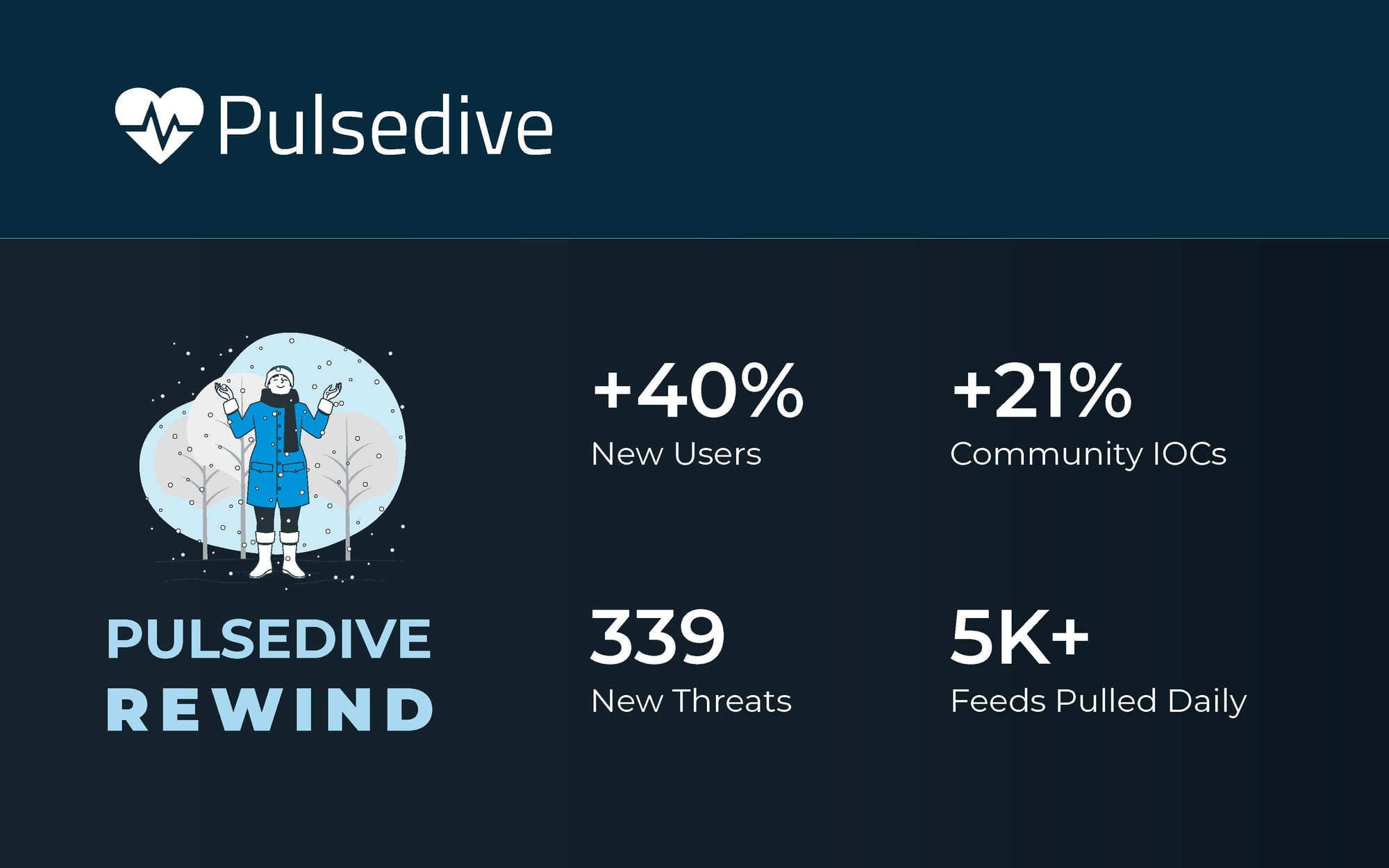
As we close out the year, we also wanted to share a few of our highlights. In 2024, we strengthened our infrastructure and capabilities across our products. We were energized by our community of Pulsedive users and clients - some of whom we were lucky to meet at various events throughout the year. Check out what our team was up to, plus some of our favorite moments below.
New and Favorite Integrations

We added integrations with OpenCTI, ServiceNow, and Torq.
Your favorite integrations? Palo Alto Cortex XSOAR, Cisco SecureX, SpiderFoot, Tines, and pfSense pfBlockerNG.
Top Blogs

Our CyberChef tutorial and example walkthrough quickly became top blog. We hear you: expect more helpful guides on free resources and tools in 2025.
- Tool Guide: CyberChef 101
- CTI Networking Report 2024
- Leveraging Threat Intelligence in Security Operations
Threat Research: Loaders, Stealers, Ransomware, and More
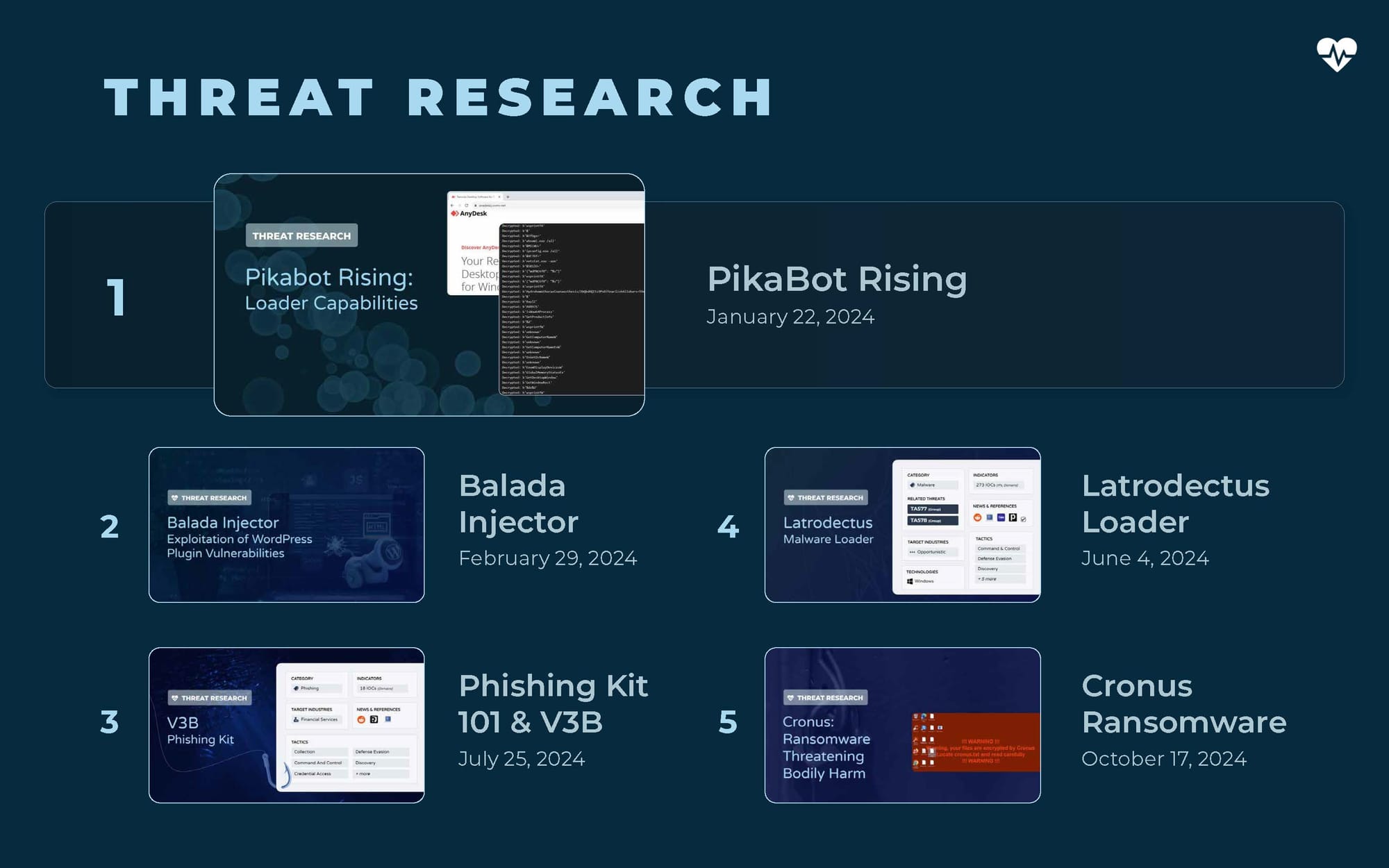
With an unending cycle of threats, news, and vulnerabilities, it’s hard to stay on top of every development. We focused on providing clear summaries with unique insights to help analysts and researchers stay in the know. Here’s which threats piqued your interest the most:
- PikaBot Rising
- Balada Injector
- Phishing Kits 101 & V3B Phishing Kit
- Latrodectus Loader
- Cronus Ransomware
Events

This year, we presented our research on sharing at the SANS CTI Summit, volunteered in our local community’s SECONNJ and Alice in Cyberspace conferences, pulled back the curtains to share stories about the realities of bootstrapping at BSidesNYC, served on the CFP review panel for Cyberjutsu, donated licenses for live NOC demonstrations with our partner Cisco at BlackHat and RSA, and more. It’s always an amazing time meeting with users and clients from all over the world. Two of our recorded talks include:
SANS CTI Summit "Sharing, Compared” Talk
Stellar Cyber “Securing the Right Deal” Webinar

Pulsedive Product

In 2024, our team released improvements to our free add-on, introduced MFA to all users, improved our scanning infrastructure, updated our STIX/TAXII docs, and a bunch more in the backend. Up next, you can expect improvements to scanning performance, risk scoring, searchable properties, and downloadable content from scans.

We can’t say it enough: feedback from our community keeps us motivated and committed to making Pulsedive better every year. When we get messages out of the blue like “I just want to send a HUGE thank you and congratulations to all of the team that built and maintains this awesome platform!” and “You folks are great, thanks for being such a wonderful group in the Intel space”, it continues to solidify why we do what we do, and how we do it every day.
We thank you from the bottom of our hearts for your support and for being part of our journey. On to 2025.
References
- https://blog.bushidotoken.net/2024/12/top-10-cyber-threats-of-2024.html
- https://blackpointcyber.com/resources/blog/2024-soc-year-in-review/
- https://industrialcyber.co/cisa/cisas-2024-year-in-review-document-details-cyber-defense-infrastructure-protection-milestones/
- https://www.ncsc.gov.uk/files/NCSC_Annual_Review_2024.pdf
- https://www.trendmicro.com/en_ca/research/24/d/operation-cronos-aftermath.html
- https://www.justice.gov/opa/pr/united-states-charges-dual-russian-and-israeli-national-developer-lockbit-ransomware-group
- https://www.europol.europa.eu/media-press/newsroom/news/lockbit-power-cut-four-new-arrests-and-financial-sanctions-against-affiliates
- https://www.nomoreransom.org/en/decryption-tools.html
- https://www.nationalcrimeagency.gov.uk/the-nca-announces-the-disruption-of-lockbit-with-operation-cronos
- https://www.bleepingcomputer.com/news/security/clop-ransomware-claims-responsibility-for-cleo-data-theft-attacks/
- https://www.huntress.com/blog/threat-advisory-oh-no-cleo-cleo-software-actively-being-exploited-in-the-wild
- https://support.cleo.com/hc/en-us/articles/27140294267799-Cleo-Product-Security-Advisory-CVE-2024-50623
- https://nvd.nist.gov/vuln/detail/CVE-2024-55956
- https://www.sentinelone.com/blog/xz-utils-backdoor-threat-actor-planned-to-inject-further-vulnerabilities/
- https://www.redhat.com/en/blog/urgent-security-alert-fedora-40-and-rawhide-users
- https://www.akamai.com/blog/security-research/critical-linux-backdoor-xz-utils-discovered-what-to-know
- https://socradar.io/year-of-takedowns-law-enforcement-operations-of-2024/
- https://bishopfox.com/blog/a-look-at-fortijump-cve-2024-47575
- https://cloud.google.com/blog/topics/threat-intelligence/fortimanager-zero-day-exploitation-cve-2024-47575/
- https://www.rapid7.com/blog/post/2024/12/16/2024-threat-landscape-statistics-ransomware-activity-vulnerability-exploits-and-attack-trends/






